1. Social Engineering is more important than fancy technologies:
Most hackers exploit the human trust and override common sense via implanting themselves in the existing social context. This is a very easy procedure. All the hacker has to do is to get the list of your friends which is easily available on Facebook, LinkedIn etc. and spam them. Even if few people fall in the trap, their email, and social networking accounts are searched for conversations with you. Then the hacker secretly associates itself with the context.
How to protect yourself?
- Always keep your system up-to-date with proper anti-virus, etc.
- Restrict privacy on social networking sites.
2. Common Password for different accounts:
It is quite common for people to have a single password for different accounts. Hackers can utilize this against you very easily. This means, if one of your accounts is compromised, you are hacked everywhere. This happens, simply because some websites are known to trade your data with these hackers. Not only this, hackers know that most of us like to use very easy passwords which make us very soft targets.
How to protect yourself?
- Use unique password for every website.
- 2-Factor Authentication: Facebook, Google, and most banks implement this.
- Using password managers like LastPass
3. Hacking is not as fancy as it is being shown in the movies:
It is this misconceptions and myths that hackers misuse. Hackers usually work silently. The most common methods that they like to use are as follows:
- Keystroke Logging: a virus or Trojan is installed on your computer which helps in tracking your keystrokes. Hackers use this to retrieve passwords and usernames by incorporating a little bit of social engineering, example: the first keystroke of the day would most probably be the login id and password for the system, etc.
- Phishing: Hackers take advantage of our tendency to trust too often. Fake and imposter websites, survey forms, etc. are some of the ways the hackers trick you into sharing important information. Hence, phishing is the most common and most profitable cyber attack.
- Packet sniffing: The hackers intercept the data during transmission. As soon as the network is compromised, the data packets can be easily sniffed for private information.
How to protect yourself?
- Maintain good cyber hygiene to prevent viruses, Trojans, etc.
- Packet encryption with the help of SSL/TLS or VPN
4. Microsoft Office Macros:
One of the most common attacks is this one i.e. sending a Word document with a malicious macro. On opening the document, an error is generated:
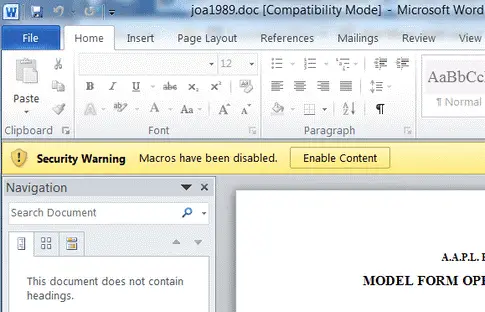
As soon as you click the button, the malware is installed on the computer without the user’s knowledge.
How to protect yourself?
Make sure your email account filters out Microsoft Office document with macros.