Last Monday, the whole world has braced the spread of a substantial ransomware cyberattack that cripples thousands of computers in hospitals, banks, and even the government institutions.
The WannaCry (or also known as WannaCrypt, WannaCrypt0r 2.0, WCRY, or Wanna Decryptor) ransomware attack is an on-going cyberattack of the WannaCry ransomware computer worm, aiming computers with Microsoft Windows operating system. The intruders are demanding ransom payments in the form of cryptocurrency Bitcoin or they will lock down a computer and remove all its data. Europol, the European Union law enforcement agency, has described the attack as unprecedented or extraordinary in scale.

Organizations are now scrambling to utilize the latest security patch and prevent the spread of this perilous cyberattack. The ransomware attack has already affected more than 200K computers in over 150 countries.
According to Talos (Cisco’s security research wing), the WannaCry attack started at 3:24 AM ET on Friday, 12 May 2017. The intruders took advantage of a glitch in Windows operating system. Similar to the previous ransomware, the WannaCry spreads through phishing emails, and also uses the purloined EternalBlue exploit, and the NSA’s Equation Group’s DoublePulsar backdoor exploit to lay out through a network, which has not yet installed Microsoft’s latest security updates and infect exposed systems directly. On March 14, 2017, almost two months before the attack, Microsoft had issued a critical patch that will eliminate the underlying susceptibility for supported systems; however, several organizations had not applied it yet.

Particularly at risk were computers that are still running older and unsupported operating systems like Windows XP and Windows Server 2003, but Microsoft has taken a highly unusual step to release patches for the unsupported operating systems.
Soon after the attack started, the MalwareTech, a web security researcher, has found a kill switch accidentally. This registers a website mentioned in the ransomware code and helps in delaying the spread of infection. Unfortunately, new ransomware variations were already circulating and millions of devices may be vulnerable if they have not yet applied the necessary patches.
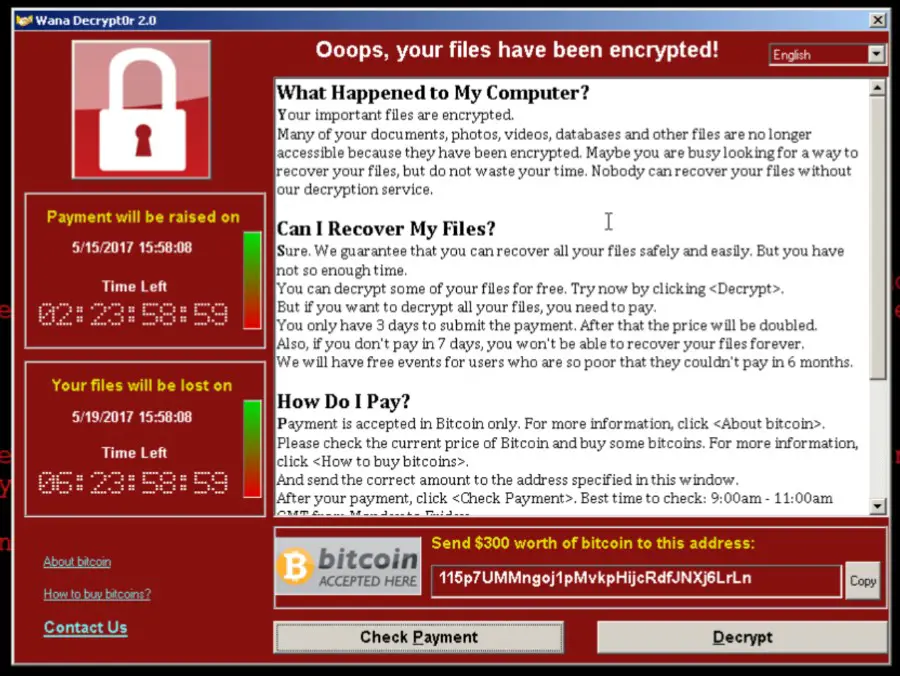
According to the latest reports, India was said to be one of the countries worst affected by this ransomware cyberattack. According to Kaspersky, an anti-virus provider, 5% of all affected systems were from India. The officials from India clearly stated that they do not have major reports about the said disruptions, but reminded that the latest assessment of the collision would be clear by Monday.
Director General Sanjay Bahl of Indian Computer Emergency Response Team (CERT-In) stated that they have shared a list of do’s and don’ts to banks, airports, defense, public utilities, etc. and warned those who have not yet applied Microsoft’s latest software patch to apply it immediately.
To avoid the ransomware, Microsoft’s Malware Protection Center advised everyone to install an updated antivirus solution, ensure that all your software is up-to-date, do not instantly click on links or open any emails or attachments from people you don’t know, turn on smart screen (in IE) to identify phishing and malware websites, install pop-up blocker on your browser, and create a back-up of your important files regularly.