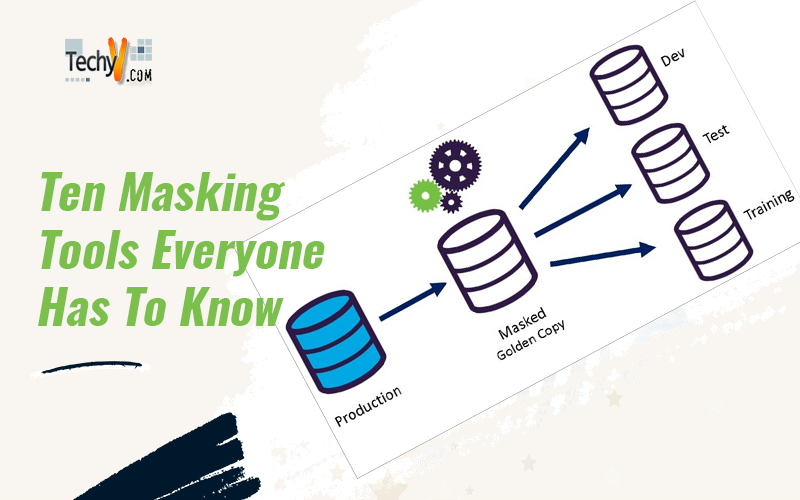
The market for DM technologies includes solutions for desensitizing data to protect it from breaches of confidentiality or privacy. Without extensive custom development, these technologies enable organizations to minimize the footprint and propagation of sensitive data (or its viewing). The masking of data depends on the use case. The most common application of DM technologies is data desensitization in nonproduction environments. It protects transferring files from one location to another. It also aids in the security of application development, testing, and CRM applications. It gives users access to dummy data for testing or training purposes.
1. Broadcom
The Broadcom Test Data Manager provides data masking for organizations that use the product. Developers can use this product to generate realistic test data or use existing data without compromising sensitive information. Data masking allows developers to conceal confidential or classified information during the product or software development, testing, and quality assurance (QA) phases. As a result, businesses can ensure that their product development processes are efficient and meet regulatory requirements.

2. Oracle Data Safe
You can use Data Safe to manage your Oracle Databases by understanding the sensitivity of your data, assessing data risks, masking sensitive data, implementing and monitoring security controls, assessing user security, monitoring user activity, and meeting compliance requirements regarding data security. Data Safe provides essential data security capabilities on Oracle Cloud Infrastructure, whether using Oracle Autonomous Database or Oracle Database Cloud Service (Exadata, Virtual Machine, or Bare Metal).

3. K2View Data Masking
K2View secures sensitive data at rest, in use, and in transit throughout the enterprise. The platform organizes data uniquely into business entities while protecting referential integrity and enables several masking functions. A wide range of masking functions is available by default.
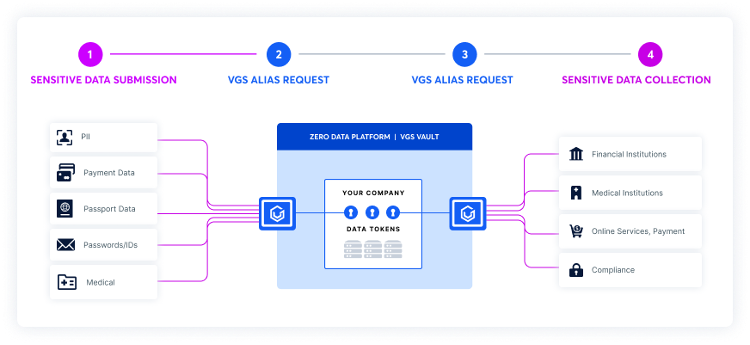
4. VGS Platform
Using the VGS Zero DataTM approach, clients can de-risk their technical environment and achieve compliance certifications such as PCI DSS faster, using the VGS Platform to secure sensitive data collected, stored, and exchanged. The VGS Zero Data approach enables you to work with sensitive data without the risk and liability of touching or keeping it, thereby decoupling the data’s value and utility from the associated security and compliance risks.
5. Datprof
DATPROF offers an intelligent method of masking and generating data for database testing. It uses a patented algorithm to subset the database in a simple and proven manner. With an easy-to-use interface, the software can handle complex data relationships. It has a clever way of temporarily bypassing all triggers, constraints, and indexes, allowing it to be the best-performing tool on the market.

6. Delphix
In unprofitable environments, the Delphix data platform provides an automated approach to data masking. It masks sensitive information (such as social security numbers or credit card numbers) with realistic data, allowing it for development, testing, quality assurance, and analytics. Even though the masking algorithms are pre-configured, you can customize them to meet the security.

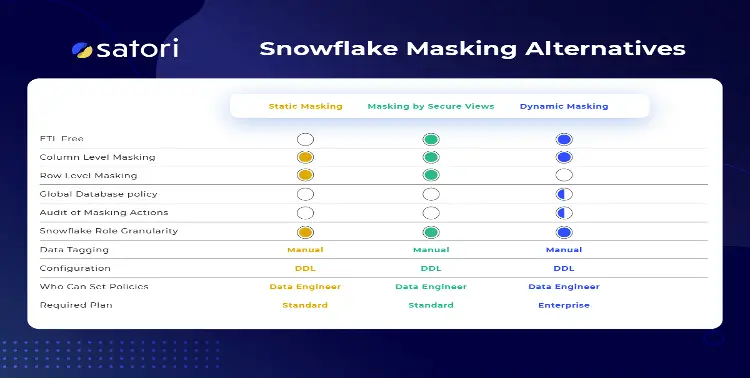
7. Satori
Satori developed the first DataSecOps solution. It simplifies data access while addressing security and privacy issues. The Secure Data Access Service provides a unified visibility and control plane across all data stores, allowing you to monitor and control your data in real-time while automating access controls. The service maps the organization’s sensitive data and monitors all data flows across all data stores in real time.
8. Accutive Data Discovery
Accutive’s Data Discovery and Data Masking solution, or ADM, enables you to discover and mask your critical sensitive data. It is possible to preserve multi-source data while maintaining its properties and fields. Using pre-configured, editable compliance filters or user-defined search terms, Data Discovery efficiently identifies sensitive databases. You can incorporate your Data Discovery findings into your Data Masking configuration or create your own.
9. IMask
With iMaskTM, Mentis offers data protection, security, and governance solution. It protects sensitive app and database data in production environments by encrypting and tokenizing it with the NIST-approved fips140 algorithm. The solution accepts data from different sources.
10. Liveramp
LiveRamp is the leading data connectivity platform for data security and efficiency. LiveRamp allows companies and their partners to connect, control, and activate data to transform customer experiences and generate more valuable business outcomes by leveraging core identity resolution capabilities and an unparalleled network. With LiveRamp’s fully interoperable and neutral infrastructure, brands, agencies, and publishers can address customers end-to-end.