Cybersecurity software is necessary for a business or an individual’s cybersecurity and privacy. The technique used to protect against cyberattacks on the network, system, or applications is known as cybersecurity. It protects against identity theft, cyberattacks, and unauthorized data access. The different components of cybersecurity include application security, information security, network security, disaster recovery, operational security, etc.
1. Syxsense
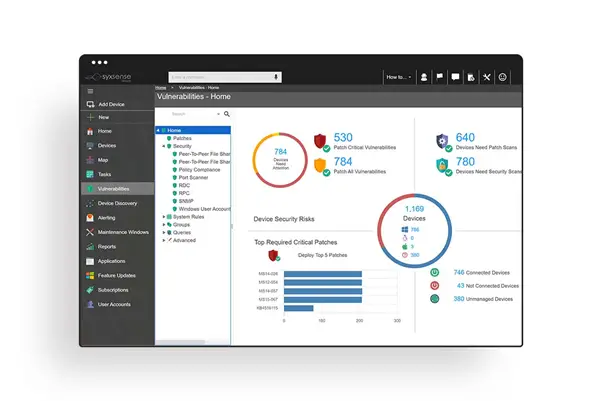
By combining security scanning, patch management, and remediation into a single cloud-based console, Syxsense Secure enables IT and security teams to stop breaches with a single endpoint security solution. Utilize our security scanner to scan for authorization problems, security implementation, and antivirus status to prevent cyberattacks. Automatically deploy Windows 10 Feature Updates, OS, and third-party patches with support for all major operating systems.
2. NMap
A port scanning tool is called NMap. It is utilized for security auditing and network discovery. You can use it to schedule service upgrades and manage Network Inventory. You can use it to track host or service uptime as well. Nmap is a robust, adaptable, simple, and cost-free tool that supports different port scanning techniques. Nmap suite is a collection of tools that includes items like Zenmap, Ncat, Ndiff, and Nping.

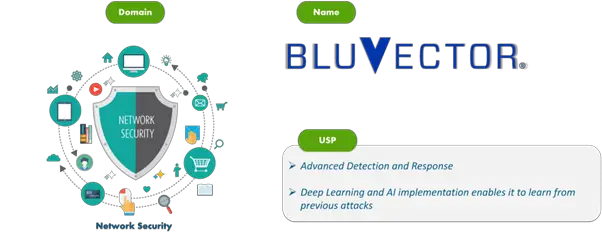
3. BluVector
BluVector offers real-time advanced threat detection. This network intrusion detection system is based on speculative code execution, machine learning, and artificial intelligence. Real-time detection, analysis, and containment of ransomware and zero-day malware are also possible. BluVector Cortex can handle both malware with and without files.
4. Norton Security
Norton 360 with LifeLock offers an all-inclusive solution. The business provides cybersecurity software options like antivirus, virus eradication, malware protection, cloud backup, password managers, and secure VPN. Norton Antivirus offers a defence against malware, ransomware, viruses, spyware, and other online dangers. For computers, smartphones, and tablets, there is a Norton security solution. It offers a range of solutions, including VPN, antivirus software, and password managers.

5. Webroot
Webroot uses a cloud-based platform. It can defend mobile devices, Macs, and PCs. It offers a solution for partners, businesses, home offices, and personal use. Platforms for Windows, Mac, Android, and iOS are supported. Webroot offers threat intelligence, endpoint security, and DNS protection for businesses. Additionally, it offers businesses security awareness training.

6. Snort
The platform Snort is open-source. It is a network intrusion prevention application. It supports the Windows, Fedora, Centos, and FreeBSD operating systems. It can stream data to your screen while keeping an eye on network packets. As it is located behind the firewall, Snort will serve as the second line of defense. Additionally, it can make a rule-by-rule comparison of the traffic.

7. Mimecast
Utilize the cloud-based Mimecast platform for email security and cyber resilience. It offers a wide range of goods and services, including cloud archiving, information protection, web security, and email security with threat protection. Protection from spear-phishing, ransomware, impersonation, and some other types of targeted attacks is provided by email security with threat protection. The automated Content Control and data loss prevention features are both present.

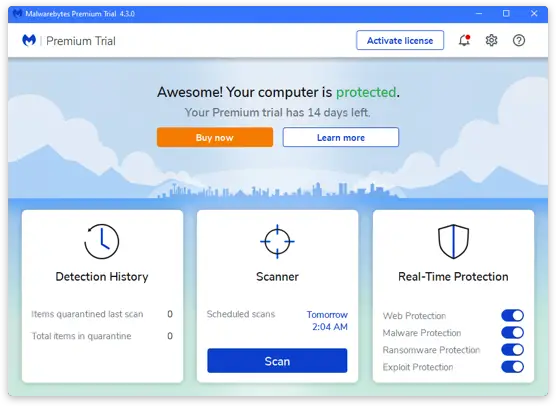
8. Malwarebytes
Malwarebytes provides cybersecurity products for both businesses and homes. Malware, ransomware, malicious websites, etc. can all be protected from. Additionally, it can defend against sophisticated online threats that antivirus software is unable to identify. Devices running Windows, Mac, Android, iOS, and Chromebooks are supported. It provides a range of goods and services for businesses, including incident response, endpoint security, etc. These options are available for the healthcare, finance, and education sectors.
9. LifeLock
LifeLock is a tool for keeping an eye out for threats and identity theft. You can protect your identity, devices, and online privacy all at once with Norton 360 and LifeLock. It is the platform that has the ability to block cyberthreats, identify and notify users, and restore and reimburse. With identity restoration agents, the issue of ID theft will be resolved. Up to the amount of your plan’s cap, it will reimburse any funds that are lost due to identity theft.

10. Intruder
The most well-known cloud-based network vulnerability scanner, Intruder, enables you to identify cybersecurity flaws in your most vulnerable systems and prevent costly data breaches. It is the best answer to your cybersecurity problems. It significantly contributes to time savings.



















