What Is Homomorphic Encryption?
Homomorphic encryption is transferring data into obscured form using a secret key. Only those with the key can decode the data and authorize its original condition. Encryption can secure data from denied users, modification, or theft. However, encryption also limits the uses of data, as it can’t easily be observed, searched, or manipulated without decoding it first. Homomorphic encryptions are a kind of encryption that enables certain mathematical forms that are executed on encrypted data without releasing the data or key.
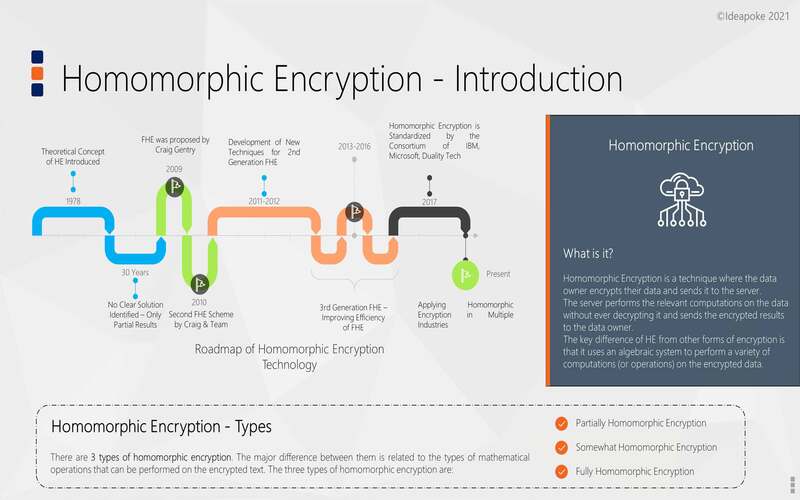
Homomorphic encryption is a variety of encryption that enables computations to be executed on encrypted data without decoding it first. It means that sensitive data is divided and observed without compromising its security.
Why Do We Use Homomorphic Encryption?
Homomorphic encryption can provide various advantages for data security and privacy, specific schemes where data is updated to cloud offers or shared with other parties. For example, it can allow secure data analysis, enabling statistical, machine learning, or artificial intelligence analysis on encrypted data without expanding the data or the results to cloud providers or other analytics. It can also allow secure data sharing, enabling encrypted data to be split with access without compromising the integrity of the data. Homomorphic encryption can allow safe data production, enabling encrypted data to be prepared according to predefined rules or strategies without decoding it first. There are several benefits to homomorphic encryption involving
1. Increased Security
Homomorphic encryption can improve and increase the security of sensitive data by averting unauthorized admin to the data. Because the data stays encrypted even when watched, unknown users cannot read it.
2. Improved Efficiency
Homomorphic encryption can help to enhance the productivity of data analysis by enabling computations performed on encrypted data. It saves your time and resources, as it removes the requirement to decode the data first.
3. New Applications
Homomorphic encryption can allow new applications that were not possible earlier. For example, it can be used to enable safe cloud computing and provide privacy-restoring machine learning.
4. Privacy And Confidentially
Homomorphic encryption allows sensitive data to remain encrypted by computations, ensuring privacy and confidentially. It is essential when dealing with primary information, such as financial data, as it lowers the risk of unofficial access.
5. Secure Updating Of Computations
With homomorphic encryption, data owners can update computations to third-party service offers while keeping the data encrypted. It enables safe and privacy-restoring cloud computing, where data remains secure even after remote servers process it.
6. Data Collaboration
It facilitates safe collaboration and data sharing between multiple gatherings. By enabling computations on encrypted data, different groups can jointly observe information without expanding the raw data to each data, restoring privacy and confidentiality.
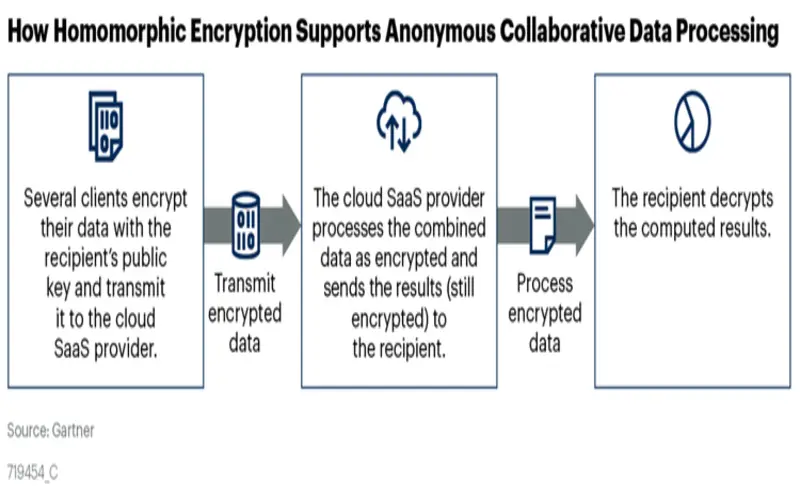
7. Enhanced Security
Homomorphic encryption can ease security risks associated with data breaking. Even if an attacker acquires access to the encrypted data or the computing surroundings, the details remain obscured without the decoding key. It adds a layer of security to sensitive data.
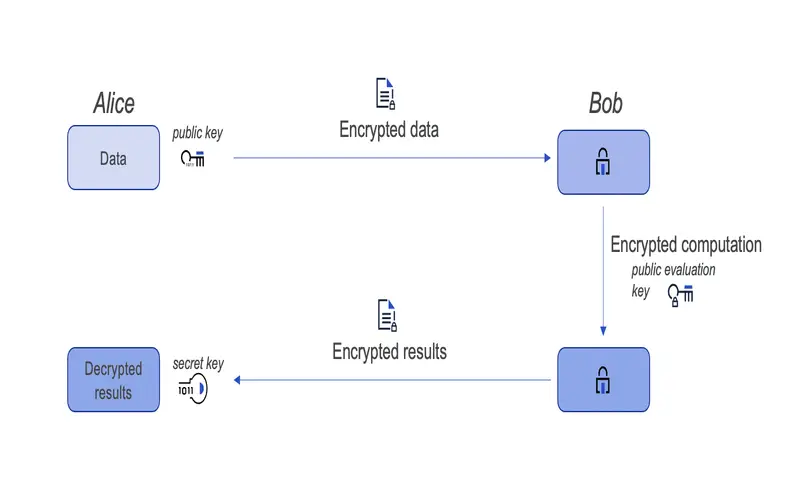
8. How To Improve Your Threat And Loopholes Management
Homomorphic encryption can help you enhance your threat and loopholes management by improving the protection and privacy of your data while allowing its functionality. To ensure its efficiency and suitability, it is essential to assess your data needs and risks, test and evaluate your homomorphic encryption, and observe and update them frequently, identifying what kind of data you want to encrypt, what activities you want to perform on it, and what to dull or prevent will help you choose the most proper encryption scenarios, parameter, and tools for your data. Testing and evaluating the performance, compatibility, usability, security, accuracy, and functionality of your homomorphic encryption solutions before establishing them in production or actual-world scheme will help you to identify any errors or conditions that may affect your data processing or results. Observing and updating your homomorphic encryption solutions will help you determine any changes that compromise or affect your data privacy.
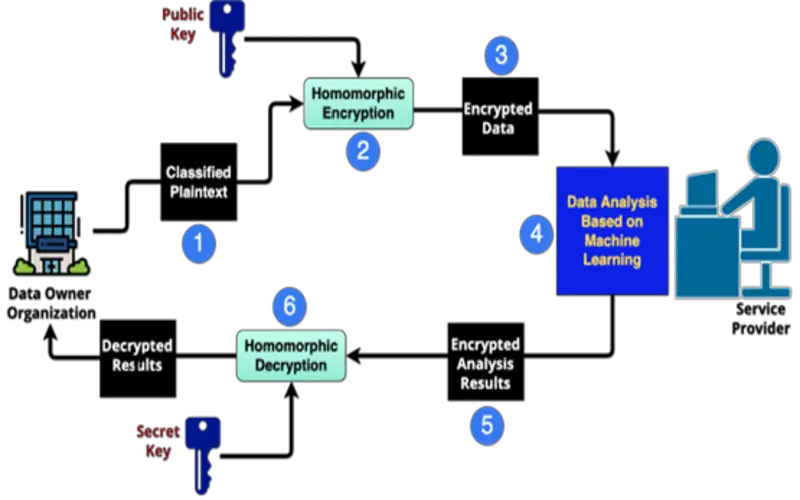
9. No Trusted Third Parties
Data remains secure and private in unreliable environments such as public clouds or third-party vendors. The data is always encrypted, reducing the possibility that sensitive information may ever be hacked.
10. Removes The Trade-off Between Data Usefulness And Data Privacy
There is no need to disguise or remove any functionalities to protect data privacy. All features can be used in an analysis while maintaining privacy.