Protecting organizational networks and systems from continuously advancing cyber threats requires proactive security measures for timely attack detection. Threat detection encompasses solutions and techniques for uncovering malicious activity through monitoring, logging, analytics, and feeds of expert-curated intelligence. As attacks grow more sophisticated, evading traditional signature-based defenses, behavior-centric detection, and intelligence-augmented tools become indispensable for security teams seeking comprehensive coverage and visibility across networks and endpoints. Open source tools in this domain provide capabilities comparable to commercial products without licensing costs, offering a flexible and potentially more feature-rich alternative. This article highlights ten prominent open-source network security tools for facilitating threat detection and investigations.
1. AI Engine
The AI Engine leverages artificial intelligence and machine learning to detect anomalies and advanced threats through continuous monitoring and analysis of network traffic. It can identify deviations from normal traffic patterns to catch attacks using more subtle or incremental approaches intended to evade traditional signature-based tools. The AI Engine integrates with the Suricata IDS engine and other security products to bolster detection capabilities.

2. APT-Hunter
Designed specifically for uncovering advanced persistent threats (APTs), APT-Hunter comprises a set of scripts to analyze network artifacts such as NetFlow records. It looks for indications of C2 communications, lateral movement, data exfiltration, and other tactics associated with sophisticated multi-phase attacks. APT-Hunter also checks for overlaps with known adversarial infrastructure based on threat feeds.
3. AttackerKB
The AttackerKB project offers an adversary-focused knowledge base for tracking software vulnerabilities continuously. It includes a comprehensive repository covering vulnerability details, detection guidance, threat actor usage, and mitigation advice. The project aims to help security teams better understand vulnerabilities posing the greatest risks. Participation is open to vetted security researchers.

4. Automater
Automater takes a hunting-centric approach to threat detection by establishing baseline system and user behavior through historical log analysis and then flagging statistically significant deviations as anomalies warranting investigation. It uses analytical techniques like Markov chain modeling, Dirichlet processes, natural language processing, and computer vision algorithms to define normal activity levels across endpoints. By surfacing outliers from these behavioral baseline models, Automater identifies previously unseen attack patterns and advanced threats not detectable using signature-based systems dependent on known bad patterns. Its unsupervised anomaly detection approach combined with the ingestion of threat intelligence enables the identification of novel attack variants early in the cyber kill chain before data exfiltration or ransomware encryption.

5. BotScout
Botnets powered by compromised hosts conscripted into remotely controlled armies of infected machines pose significant threats to organizations through vectors like distributed denial of service attacks, spam campaigns, and platform misuse. BotScout focuses specifically on detecting botnet infections within networks by masquerading as IRC or HTTP-based command and control infrastructure. It elicits responses from infected hosts reaching out to C2 channels and aggregates lists of compromised systems requiring remediation. BotScout’s specialized bot detection scans can run continuously or periodically to map out infections that persist in traditional antimalware tools. The tool can also identify C2 communication patterns to inform disruption or takedown efforts targeting botnet infrastructure.

6. CrowdFMS
CrowdFMS deploys crowdsourcing techniques for collaborative security monitoring aimed at gathering, analyzing, and sharing threat intelligence across a distributed participant pool. It ingests IOCs including compromised hosts, malware samples, phishing sites, spam campaigns, attacker infrastructure, and other threats extracted from community input. Participants can submit intelligence using APIs or browser extensions with bidirectional sharing allowing access to aggregated IOCs. This community feed of indicators and observables enables protecting organizations against emerging attacks seen within other networks. CrowdFMS also provides analytics on submitted artifacts using sandboxes, antivirus scans, and GeoIP mapping to augment detection mechanisms.

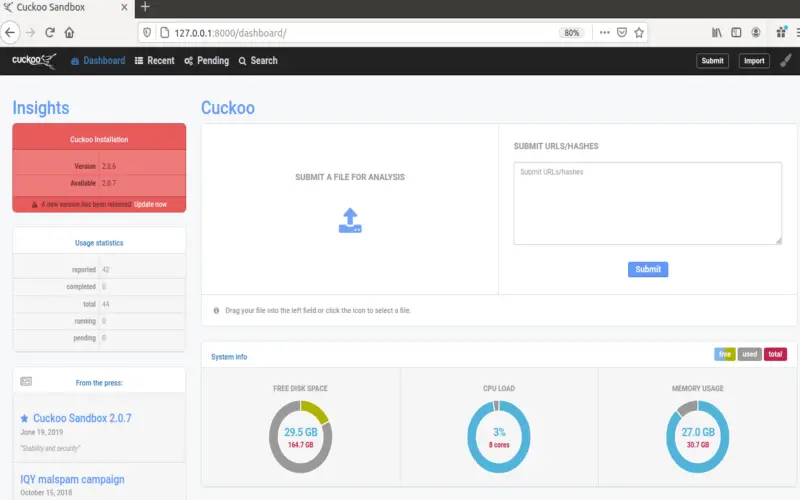
7. Cuckoo Sandbox
Analyzing malware entails understanding infection vectors, internal capabilities, C2 communication protocols, and other operational details to bolster defenses and enable remediation. Manually reverse engineering samples is resource-intensive and often infeasible given volumes of new variants. Cuckoo Sandbox offers an automated open-source framework for executing suspected malware samples within instrumented Windows, Linux, MacOS, and Android virtualized environments. It observes runtime behavior non-intrusively including filesystem, memory, network activities, and high-level capability assessments. Detailed JSON-formatted reports capture malware characteristics, screen captures, dropped files, registry modifications, and network artifacts. An API allows automating submissions, retrieving reports programmatically and integrating Cuckoo Sandbox malware assessments into investigative and detection workflows.
8. Snort
Snort operates as an open-source network intrusion detection and prevention system performing real-time traffic inspection and analysis to identify threats through signature-based pattern matching, protocol anomaly detection, and statistical outlier flagging. It compares observed packets and connections against community-sourced rules containing malicious traffic fingerprints and vulnerability attack markers. Snort can detect exploits against vulnerabilities like buffer overflows and web app injections. Its flexible architecture supports deploying across enterprise networks, perimeter choke points, endpoints and cloud environments. Snort benefits from constant rule updates as well as customizable configurations tuned using local network data for particular environments using open format control files.

9. Suricata
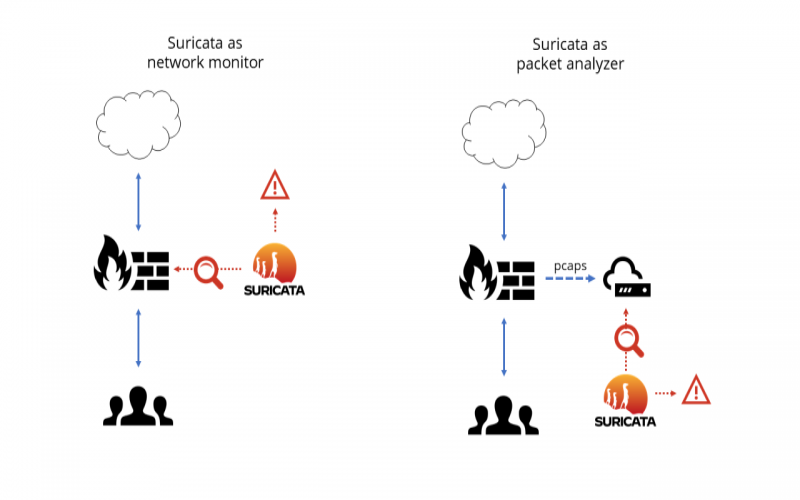
Developed under the aegis of the Open Information Security Foundation, Suricata offers an advanced IDS/IPS engine for network monitoring that combines signature-based techniques, protocol analysis, threat reputation data, and anomaly detection capabilities. It can tap into emerging threat feeds including Proofpoint ET Intelligence and the Emerging Threats expert-curated ruleset to bolster the detection of current attack campaigns, malware activity, suspicious domains, and known adversarial infrastructure. Suricata also leverages specialized hardware through GPU integration and SIMD support for high-throughput multi-pattern matching using Hyperscan. These capabilities combine to provide robust network monitoring and threat hunting across complex, high-traffic networks.
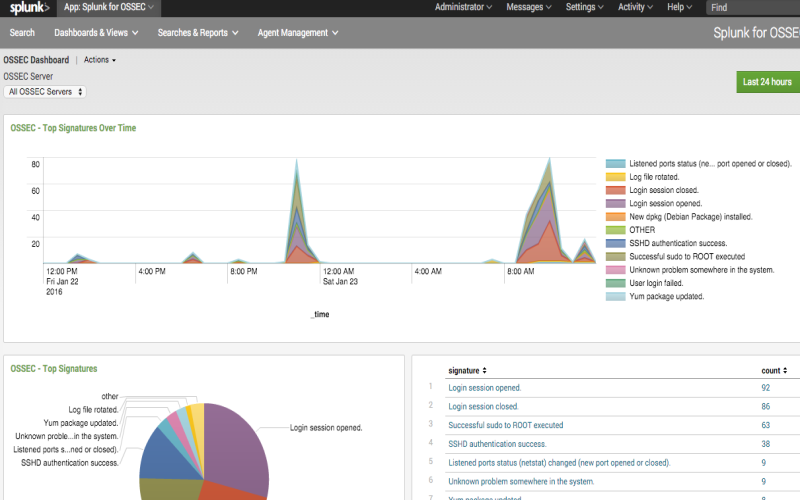
10. OSSEC
OSSEC brings open-source host intrusion detection capabilities through log monitoring, filesystem integrity checking, rootkit checks, Windows registry monitoring, and real-time alerting for endpoints. Supporting both agent and agentless modes allows flexibility for securing servers, user systems, and network devices. OSSEC checks for discrepancies relative to saved state baselines indicating potential malicious or suspicious activity. It relies on XML-based configuration files to define rules specifying metrics for different observation types covering threshold breaches. anomaly counts and frequency as well as multiple correlation rules to reduce false positives and enable wider coverage of attack space through expertise contributed openly by information security professionals.