What Is A Cyber Attack?
A cyber-attack is an effort by cybercriminals, hackers, or another digital opponent to access a computer network or system, generally, to alter, steal, destroy, or display information.
Cyberattacks can target a vast range of prey from identical consumers to organizations, the hacker’s goal is generally to authorities sensitive and costly company resources, such as expert property (IP), user data or payment information.
What Is A Malicious Code?
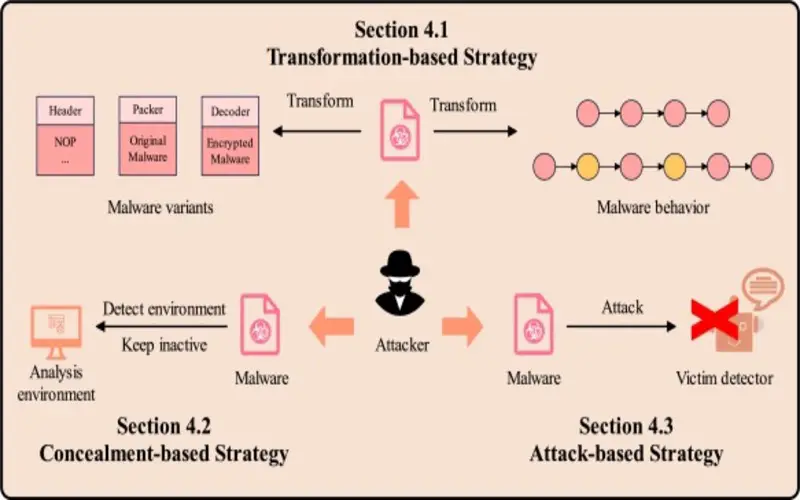
Malicious code is any type of code that causes harm to a computer system or network. It includes viruses, worms, Trojan horses, ransomware, logic bombs, and other malicious software.
Malicious code is the language used by threat actors to communicate with computers. This code is pre-owned to influence the computers and make changes. It then patterns programming scripts – or “phrases” -to destroy, alter, or breach the network to generate or utilize system threats. Malicious code is used to trade multiple forms of malware and is worn to bring out various cyber-attacks. Dreadfully, these attacks are more straightforward to bring out as the malicious code scripts can be utilized and automated. It enables widespread and quicker cyber-attacks to take place.
Three Types Of Cyber Attacks?
1. Unpatched Security Vulnerabilities
While they are constantly developing new vulnerabilities, many of them rely on old security vulnerabilities to function. With so much malware looking to manipulate the same few threats repeatedly, one of the enormous risks that a company once they are discovered.
It’s far too common for a business–or even simply the same users on a network—to reject the “update available” reminders that appear in specific programs because they don’t want to sacrifice the 5-10 minutes of creative productive time that executing the update would require.
2. Phishing (Social Engineering) Attacks
In a phishing attack, the attacker tricks an employee in the sacrifice organization into providing away sensitive information and account credentials- or into downloading malware. The most basic form of this attack comes as an email impression of one of your firm’s traders, someone who has a lot of access to the company. For instance, the attacker may say something like: “This is Mark from IT, your consumer account shows suspicious actions, please click this link to reset and protect your password.”
3. Malware Software
Malware or malicious software is any program or code that is created to harm a computer, network, or server. Malware is the most general type of cyberattack, mainly because this word encloses many subsets such as ransomware, trojans, spyware, viruses, worms, keyloggers, bots, crypto-jacking, and any other type of malware attack that authority software in a malicious way.
1. Uniting Innovation Leaders For A More Robust Defense
In the recent cyber landscape, cybercriminals no longer work alone but perform within complex networks, constantly refining their strategy. If cybersecurity leaders work in separation, without exploiting the facilitating of shared knowledge and learnings, they will be in a position of weakness.

2. Creating The Game Plan For Resilience
Trend Micro not only supports a vast network of global partners and users but also expends heavily in research and development to retain at the bleeding edge of cybersecurity. Given today’s companies climate, with maximized interest rates and tightened budget limitations across the board, it’s necessary for innovation leaders to openly confirm the link between solid cyber hygiene and its overall company effect on management. Companies’ decision-makers admit they are being asked about security in negotiations with possibility and suppliers.
3. A Scalable Is The Best Method
As organizations navigate the complicated digital transfer and an extending attack surface, proactive cyber risk management becomes critical. By acquiring the complete structure of assessment, evaluation, response, and reduction of risks, cybersecurity heroes can support their enterprises’ cybersecurity flexibility. The best defence method is a three-pronged approach that includes attack surface management, expanded detection and response (XDR), and zero belief. XDR enhances effectively by combining data and workflows, automating daily duties and improving vulnerability detection and prioritisation.
4. Evolution Of Malicious Methods
Malicious software programmers consistently develop their methods to stay ahead of cybersecurity measures. From standard viruses and worms to the latest ransomware and zero-day utilizes, the range of malicious software has broadened, posing an essential difficulty for cybersecurity experts.
5. Enlarging Attack Vectors
Attack paths have multiplied with the maximizing interconnectedness of tools and systems. Malicious malware now reaches not just basic endpoints like PCs, but also aims at IoT, devices, cloud structure, and even critical structure systems, increasing the potential impact of cyber-attacks.
6. Sophistication In Code Obfuscation
Malicious code is becoming maximally sophisticated, deploying the latest obfuscation methods to evade evaluation by antivirus and incursion systems. It complicates cybersecurity specialists’ ability to examine and identify malicious software before it causes harm.

7. Ransomware As A Lucrative Business Model
Ransomware assaults have increased in recent years, spurred by their profitability as a business model for cybercriminals. The development of consumer-friendly ransomware kits, accessible on the dark web, enables even non-technical identical to launch ransomware attacks, distributing to the overall maximizes in malicious software events.
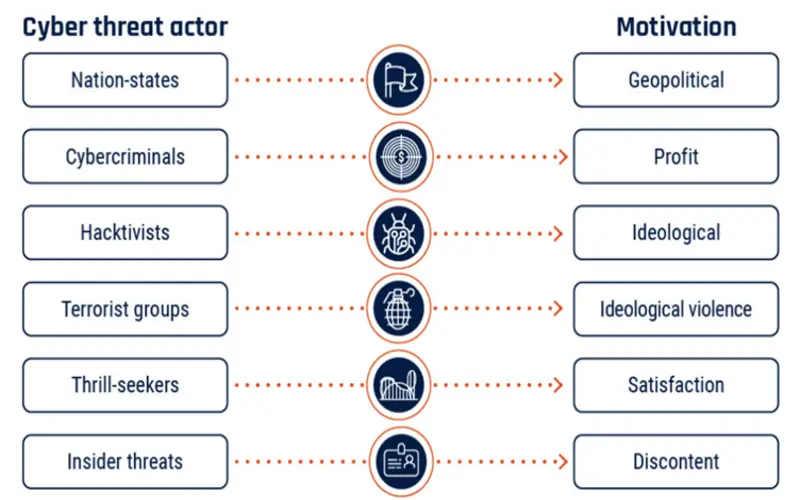
8. Nation-State-Sponsored Malware
State-sponsored cyber actions have introduced the latest dimension to malicious software development. Nation-states are maximizing success methods goals, such as spying or disrupting crucial structures in rival nations.
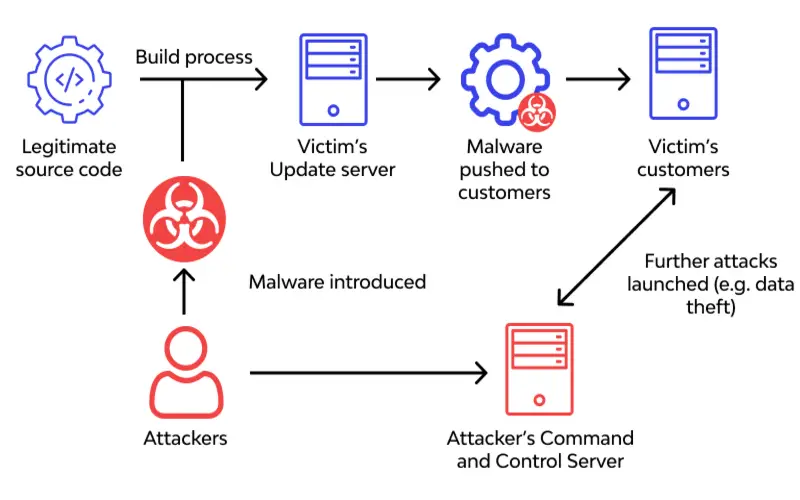
9. Supply Chain Attacks
Malicious actors manipulate loopholes in the supply chain to inject malware into software and hardware early as they approach end-users. This strategy allows attackers to bargain for huge numbers of systems quickly, making it an appealing method for those seeking wider effects.
10. Evasion Of Machine Learning-Based Military
With the maximizing use of machine learning in cybersecurity, malicious software programmers are developing methods to evade evaluation by machine learning models, which are becoming more established, needing consistent refinement of defence mechanisms.