Zero Trust Security has emerged as a vital strategy focusing on strengthening network security in the ever-changing cybersecurity scenario. The concept is developed with the principle of “never trust, always verify,” prioritizing a proactive approach to security.
Zero Trust refers to a group of techniques designed within the cyber world that operates on the assumption that every digital activity has some wrong intentions and therefore, each activity must be verified and appropriately authenticated. The access to a network is granted only after complete verification. If the device accessing the network is not verified, then the network access is denied. The Zero Trust Security aims to check the device’s identity and integrity vigorously and allow access to applications and services based on user authentication.
It helps to mitigate the risks by constantly verifying devices and validating users before granting access. In Zero Trust Security Network, external users are not allowed to access the services on the public internet to prevent attacks from unknown entities. Access is granted only after approval from the trust broker. It is crucial to select the right zero-trust security vendor that would help in improving the security posture of an organization. In this article, we will look at the top 10 zero-trust vendors known for their exceptional services in the industry.
1. NordLayer
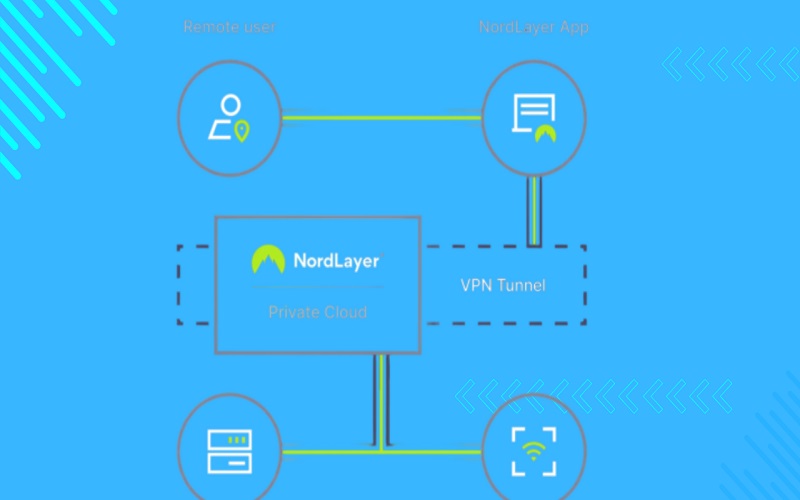
NordLayer provides a standardized zero-trust model. The company offers an advanced and scalable security solutions to protect your organization’s complex hybrid and multi-cloud environments. NordLayer works similarly to VPN within an integrated access rights management. The tool is easily deployable on mobile devices and PCs. The request for approval passes through the central NodeLayer when the users connect to the application.
2. Twingate
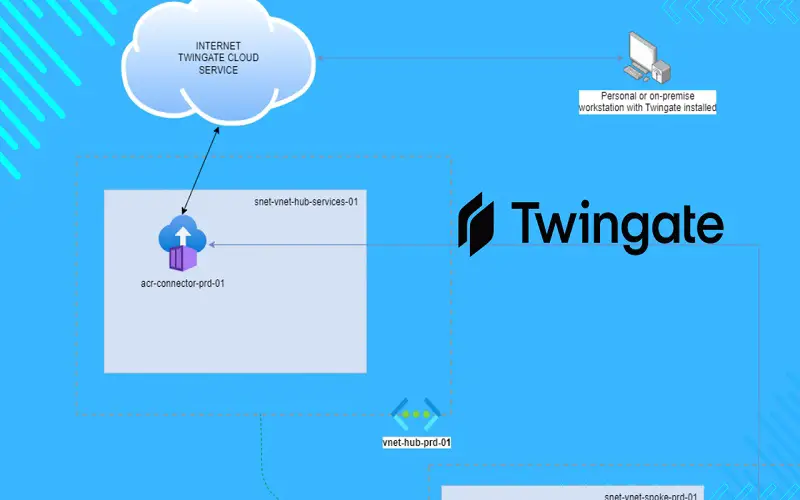
Twingate is a rapidly growing cloud-based Zero Trust Security company that protects your applications running on both cloud and premises. Access is governed by a service menu granted to each user. On denial of access, the software will not appear on an individual’s menu list. Companies can easily implement the latest zero-trust networks using the Twingate solutions without altering their existing infrastructure. The software enables centralized management of access to digital resources.
3. CloudFlare
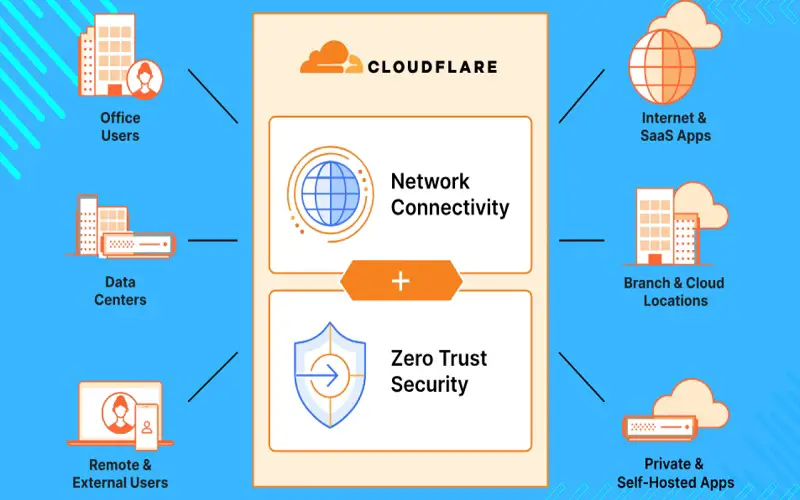
CloudFlare enables users to access resources without needing a VPN and help them to shift from traditional models of network infrastructure. The security solutions provided by CloudFlare company include minimizing data loss, malware and phishing, isolation of browsers, and email security. The services offered by CloudFlare offers visibility and control over SaaS applications. You can attain the lowest latency with precise control and automatic code deployment on all global locations.
4. Palo Alto Networks
Palo Alto Network offers next-gen firewall solutions and focuses on real-time threat detection. With an easy-to-use interface, the company is known for its dedication to offering dynamic cybersecurity solutions for businesses. Palo Alto’s Zero Trust Security vendor focuses on cloud security and establishing a secured framework to access the resources. The cybersecurity vendor leverages threat intelligence to stay updated with emerging threats. It offers a comprehensive interface enabling smoother navigation and management to enhance user experiences.
5. Perimeter 81
Perimeter 81 ensures zero trust access to web apps and remote network access protocols using IPsec tunnels. Users log into the client application, and once, it’s connected, they can choose from a range of available applications. Their payment plans are flexible, billing is done on an yearly or monthly basis. Perimeter 81 offers combined security solutions for application access and connections. Their Zero Trust Security solutions are easily scalable, enabling companies to secure access to their network infrastructure and digital assets quickly.

6. Cisco
Cisco’s Zero Trust cybersecurity offers an advanced threat protection and scalable solutions for businesses. The company provides a comprehensive set of security services, including network protection, endpoint, and cloud security. Cisco’s security solutions are easily scalable to meet the growing demands of businesses. Cisco’s robust security solutions seamlessly integrates with your existing infrastructure, making it easy to implement and enhance security measures.

7. Okta
Okta’s Zero Trust security solutions are designed with the identity-centric security solutions i.e. access decisions are made based on user identity and context. The company has expertise in rendering SSO integration and adaptive authentication solutions for an enhanced user experience. Okta enables adaptive authentication through which authentication requirements are altered based on human behavior and risk factors. It’s robust identity lifecycle management feature helps in streamlining the onboarding and offboarding process for users.

8. CrowdStrike
CrowdStrike offers the world’s most significant unified threat-centric data fabric to secure businesses against cyber attacks. The company provides scalable and flexible Zero Trust security solutions for businesses to help them identify all managed and unmanaged endpoints affecting security postures. CrowdStrike’s solutions adheres to the NIST 800-207 standard. The solutions helps in preventing security breaches such as execution of malicious codes in real-time ransomware, etc.

9. ThreatLocker
ThreatLocker is a cloud-based security solution offered as a SaaS package. ThreatLocker offers tools to create elements of a ZTA network, managed through a centralized console hosted on the ThreatLocker server. The controller efficiently manages resources and users across multiple locations. It helps in managing and controlling applications usage both in cloud and on-site. With its “Allowlisting” feature, you can easily block unwanted software from running on computers and execute packages mentioned in the allow list.

10. Illumio
Illumio offers zero trust micro-segmentation from endpoints to cloud and datacentres, to prevent cyberattack and ransomware. With Illumio’s Zero Trust platform, businesses can safeguard data against lateral movements across devices, applications, and servers. The Illumino core operates on a system running on both server and cloud, while the Endpoint tracks complete activity from a particular device. Illumino’s zero trust strategies possess vsrious capabilities, including micro-segmentation, data encryption, and vulnerability management.