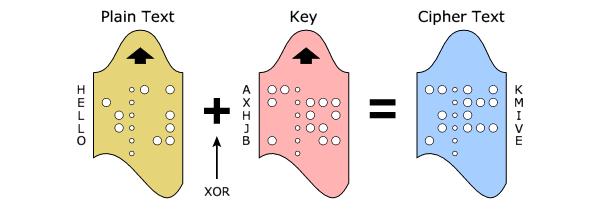
The basic work of the cipher

When we talk about the Information Systems Security, we use cipher algorithms to Encrypt or Decrypt data.
What is the basic work of the cipher and the basic concepts use in these ciphers.
- Caesar Cipher
- The Perfect Substitution
- The Vernam Cipher
- Block Cipher
- Stream Cipher