What is Kerberos and How Does it Work?
Kerberos is protocol software that is used in the authentication of communication among the computers connected in a network. It works by prompting computers connected to the same network to provide their identity. This ensures that each user operates in a secure mode, preventing unauthorized access to data. Kerberos is mostly used on the client to server type of networking, and it ensures that the client and server are experiencing equal authentication.
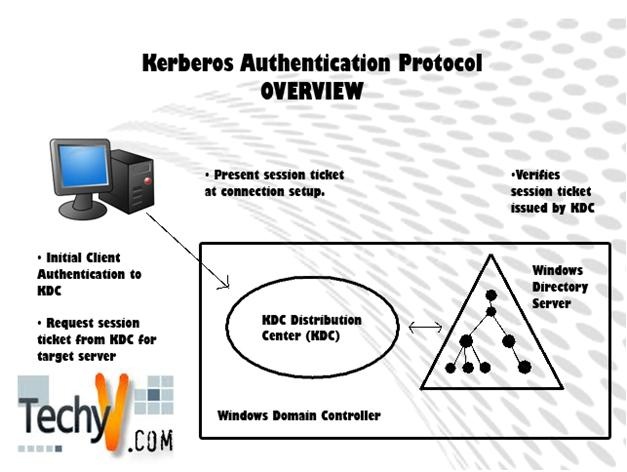
It should be noted that while using the Kerberos protocol in the client to server network connection, there will be no communication if neither of them has verified that they are sharing a network. Also, content from Kerberos protocol is safe from eavesdropping and replay attacks. Additionally, Kerberos allows the users to choose who to share the network with, and it provides services that prompt the user to be sure that the person they are sharing the network with is who they claim to be.
While working with Kerberos as a third party, you need to make yourself known to the server by providing information such as your password. Users (and sometimes software) are referred to as the client, while the “Key Distributer Center (KDC)”, is referred to as the third party. Not to worry – your identity is safe. The password that you share with Kerberos is converted to a cryptographic key while the other passwords are created randomly. Kerberos conveniently makes it is possible to freely share files over the network, and you can also sign into the system to obtain credential without having to use the “kinit” tool.
Kerberos Versions
So far, there are two versions of Kerberos. These versions are the Kerberos version 4 and the Kerberos version 5. If you’re wondering why the versions start with 4, it is because versions 1, 2 and 3 were actually never released to the public. Those versions were intended for “in-house” use within Kerberos only. It’s important to note that Kerberos version 4 has some disadvantages, and this version will be phased out in the near future.
How Useful is Kerberos?
Working with Kerberos has several sometimes unseen benefits. Kerberos was developed to overcome some of the problems faced by users sharing data over a network. The main problem was the theft of passwords. Also, Kerberos was developed to sustain a number of database accounts. When installed on your machine, this software will prevent the computer from remembering your password, thus preventing unauthorized use of your account. Also with Kerberos, instances of relocating the password in plain text to the network are reduced. In addition, it places your password and user name in a central location which makes the task of maintaining your data and logging into your account much easier.
Who Can Benefit From Using Kerberos?
Big companies will benefit the most from the use of the Kerberos application, because it helps the employers to share data related to the organization. This doesn’t mean that it’s not useful on smaller or personal computer networks. Regardless of who utilizes it, Kerberos is valuable in authenticating your account.