Archive
- 1010 Data
 It is a New York based company and started its service back in 2000. It supports parallel inflow of data and has its independent query language that supports its interface and work. It also handles machine data and data obtained from social network sites. It offers optimization of data, machine learning and statistical analysis of the same.
It is a New York based company and started its service back in 2000. It supports parallel inflow of data and has its independent query language that supports its interface and work. It also handles machine data and data obtained from social network sites. It offers optimization of data, machine learning and statistical analysis of the same.
- Action
 Ingres Corp christened themselves in 2011 when they took the name Action. The company is a huge platform and is flourishing since... Read more
Ingres Corp christened themselves in 2011 when they took the name Action. The company is a huge platform and is flourishing since... Read more
- Android API 1.5 (Cupcake) and 1.6 (Donut)
 1.5 And 1.6 versions are the first stable version of Android incorporated to the devices for the public. It is API level three and four respectively and supported keyboard applications, searching through voice and text feature upgraded in this version and multiple selections of videos, photos, etc. The launch happened in 2009 and marked the beginning of a new era.
1.5 And 1.6 versions are the first stable version of Android incorporated to the devices for the public. It is API level three and four respectively and supported keyboard applications, searching through voice and text feature upgraded in this version and multiple selections of videos, photos, etc. The launch happened in 2009 and marked the beginning of a new era.
- Éclair (Android 2.0)
 It is the advanced version of donut and cupcake. This version launched in October... Read more
It is the advanced version of donut and cupcake. This version launched in October... Read more
India not only being the top destination for It outsourcing, but it is also emerging as a hub of innovations in the field of IT businesses which is into the growing phase helping all to think out of the box and reach new heights of success. The ratio of business relying on IT solutions has increased rapidly turning out to be an emerging new business era for techies to show up their potential and help serve the society in a best possible way. IT industry is providing a platform to new e-businesses especially the aggregating business for growing up and...
Read moreIt is a technology which used in different types of applications that identifies or recognise human face with the help of digital images. Face Detection is also known to be as the physiological process by which human identify their face in a visual scene. It is a computer technology which identifies human faces without their presence. In Face Detection Technology, it requires no physical interaction of the user it can be done even if he or she is not present. It is accurate and it allows high verification rates. All identification or authentication is done by following the four stages...
Read moreFirstly, I will start with what is Database Security? , It refers to collection of data and protection of data from unwanted threats. There are so many methods or tools are used to protect the data. We have some aspects of Database Security. There are three main aspects i.e. Secrecy, Integrity, Availability. 1. Secrecy It protects the database from those users who may be at some time illegally uses the data and it ensures that the user is allowed or not to do such things which he or she wants to do. For ex. Employees are not allowed to see the...
Read moreEverybody loves to eat, and It’s their favorite pastime. What people don’t like is the extra body weight and fat which comes with it. Before you grab your shoes and go out running in excitement or order a fitness tracker for yourself, have a look at these apps which, when used judicially, will make your phone your personal trainer imparting much-needed knowledge on you.
 1. Runtastic
1. Runtastic
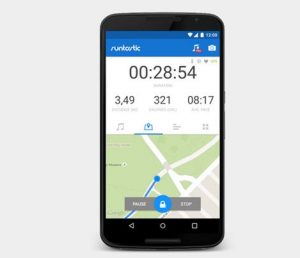 Simply put, Runtastic is Fantastic. Apart from theadvantage of being totally free, Runtastic has a host of other features too....
Simply put, Runtastic is Fantastic. Apart from theadvantage of being totally free, Runtastic has a host of other features too....
Demonetisation in India has adversely affected the way of exchange in monetary terms these days. This wind of change has completely changed the mode of usage of money which indeed is a good sign to promote digitalization in the country.
This step changed the direction and headed towards the new way of monetary exchange in the country. The digital payments or E-cash payment systems is a unique, convenience and reliable method to transfer, receive and process the money in a digitalize way accepting this new trend by the people of India will lead India move towards more digitalization world.
Read more
I don’t want my files to open or seen by anyone how can I encrypt my drives on PC? Windows 7 hard drive encryption.
Read moreHow can I start windows 7 group policy editor?
Read moreHow can I install windows 7 family pack clean install without losing the media files?
Read more









