Archive
Best Free 5 Disk Space Analyzer
What is Disk Space Analyzing? Disk Space Analyzing is a graphical representation of the total contents of your hard drive. The information displayed clearly lets you see the folders, sub-folders, and files. There are several applications used for disk space analysis known as Disk Space Analyzers. Disk Space Analyzers therefore show each folder and subfolder and tells you which folder/subfolder or file occupies what amount of space.
5 Best Root Kit Scanners
Using the internet or loading any files on your system for that matter come with the attendant risks of malicious programs that camouflage as genuine system applications.
Uninstall Guide for Exchange 2003
Scenario: In this scenario an organization is running Exchange 2003 in co-existence with Exchange 2007. We have to completely remove Exchange 2003 without affecting any services and major downtime. Uninstalling Exchange 2003 There are a number of operations that must be performed in a sequence to accomplish this task. Who can perform the Un-installation Operations? A user performing exchange operations must be member of following groups:- Domain Administrators
- Enterprise Administrators
Configuration Yahoo & Hotmail & Gmail 3 Versions Outlook Microsoft Outlook
Microsoft has brought so much convenience for users in this era of Information Technology. Microsoft Outlook is one of them, which is a good tool to use an email application. However, outlook needs to be configured with an email account e.g. Gmail, Yahoo or Hotmail. Microsoft Outlook allows users to send, receive, forward and search the emails from any of the configured email accounts. Users can configure more than one email account at a time. Furthermore, it allows saving the emails onto your hard drive that can be accessed later in offline mode or... Read moreOutlook 2010 Explained
Open Microsoft Outlook 2010. You will get a window similar to the one shown below.
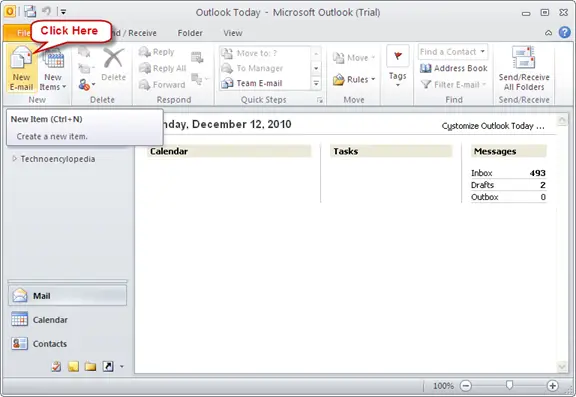
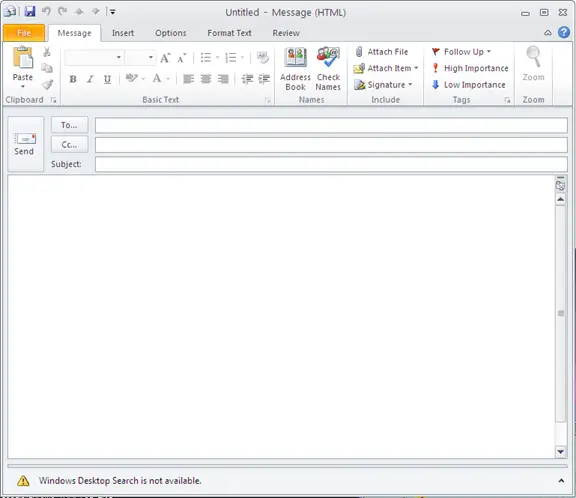


Outlook 2007 Mail Formats
Microsoft Outlook 2007 has evolved many new features with user-friendly options transforming this email-client application in many interesting ways. With the increasing use of internet and email-based communication, the importance of standards and formats are increasing very rapidly. This version offers alternative standards so users have many choices to select or modify the default formatting that enhances the standard of their company. Mail Format option serves the users in this context. It can be accessed from the Tools under Options menu. The options window has Mail Format tab that contains all the accessories of email formatting.... Read moreCache
A Cache (pronounced as cash) in computer engineering, enables the processing units of computers to minimize the average time that the computer requires in order to access the memory. The cache is a very small and quite fast memory space which provides storage for the data and information from the memory locations that are mostly used in the main memory.
It is a fact that when most accesses of memory are cached memory locations, the required average latency to access these memory locations is much closer to the latency of the cache rather than the...
Read moreA Brief Background On The Computers Process
When one turns on a computer, the user starts a complex set of steps that would somehow be discussed here. And the starting process or boot process is one of the most important elements in understanding how computers works. For a successful boot process, the computer's BIOS, operating system and components of hardware must all be functioning properly. If any one of the said three elements malfunctions, the whole start up process would probably result in a failed and unsuccessful boot.
5 Best Antivirus Software
The debate goes on whether a firewall or antivirus program is more crucial and vital to protect your system. It normally depends upon the work and the system's requirements. For this reason antivirus applications have more weight age than any other program.
Jscript, Ajax and JavaScript
This is the era of web browsing and scripting languages are one of the core elements of Web Development. Scripting languages and tools enable loads of features to enhance interactivity, security and browsing of a website.











