Archive
Exchange 2010 Security
State-of-the-art won't do, even the most advanced version of Exchange Server. Security is inevitably a circumstantial matter, and you'll always have to tailor things to a custom specification. Naturally, you'll inadvertently annoy your users, since securing attack surfaces is the corollary of taking away things people used to take for granted. Access to services might be disrupted, and features are no longer as easy to reach as before.Amazon Elastic Compute Cloud
Amazon provides a real time virtual computing environment to use any application for business subscribers. A subscriber needs to create an Amazon Machine Image (AMI) which contains the operating system, libraries, data, application programs and configuration settings.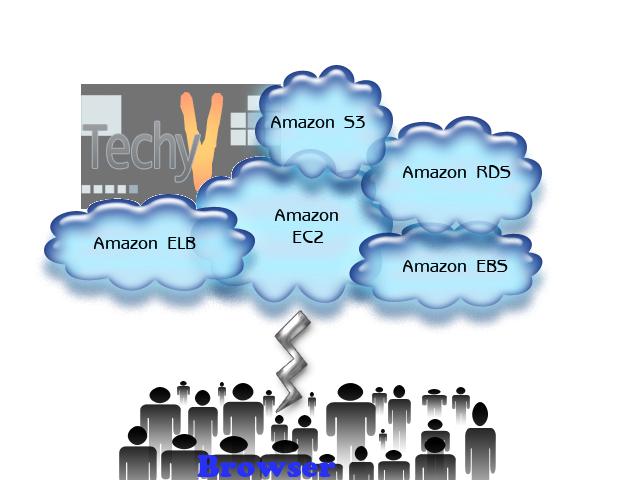 The second step is to upload the AMI at Amazon Simple Storage Service (Amazon S3) and register with Amazon Elastic Compute Cloud (EC2). After creating and completing it, the business subscribers can requisite virtual machines as needed. Amazon provides unlimited set of virtual machines. The capacity of virtual machines can be increased... Read more
The second step is to upload the AMI at Amazon Simple Storage Service (Amazon S3) and register with Amazon Elastic Compute Cloud (EC2). After creating and completing it, the business subscribers can requisite virtual machines as needed. Amazon provides unlimited set of virtual machines. The capacity of virtual machines can be increased... Read more
Windows 7 Tips Life is nothing without technology, and when it comes to technology the computers are at top. Windows 7 with all versions are currently being used by major part of computer users. Windows 7 tips are used to save the precious time of users, it provides the efficient and quick way to manage Windows 7.
A tip provides very good solution for small queries and problems of users.
There are many scenarios when users have options to use Windows 7 tips. Command prompt is basic function of every operating system, and so in Windows 7....
Read moreApproaching Web 2.0 and all its issues
All about Web 2.0
The notion of Web 2.0 started with a seminar brainstorming meeting between O'Reilly and MediaLive International. Dale Dougherty, web pioneer and O'Reilly VP, documented that far from having crashed, the web was more significant than ever, with stimulating new submissions and sites popping up with astonishing regularity. What's more, the businesses that had endured to have some things in common. Could it be that the dot-com disintegrate assessed some kind of rotating issue for the world.

a. The Web as...
Read moreA quick guide to DLLs and device drivers
Some of the terminology in computer hardware and operating systems can be a bit confusing. In particular what makes certain components talk to other programs and where things are stored? This is a quick guide to DLLs and device drivers.
Cloud Computing System and Its Layers
Cloud computing system stunned the world with its introduction. From day one, businesses around the world have shown interest in the functionally and the systematic engineering of this system. However cloud computing has ever been challenged by its reliability, security and pricing issues. A number of businesses have also formally raised objection against the pricing of this particular system. But this system continues to attract new clients around the world. People have realized that with this system around them they don’t need to make unnecessary investments for developing new departments. They can just purchase... Read moreLCS 2005 versus OCS 2007
In most enterprises the real time communications and instant messaging (IM) became important communications tools since late 1990's. But in many enterprises the implementation of these systems has taken place in a disorganized fashion.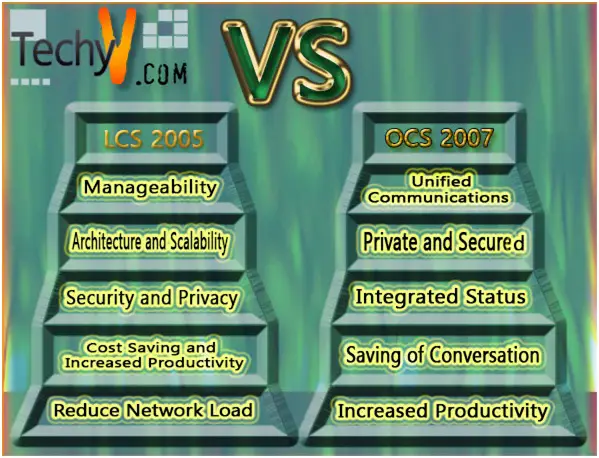
AD Auditing
Chalk it up to human nature, but all part of the job when you are running servers. Political scientists put it nicely when they ask, "Where and when does who gets what?" Who's logged onto which computer? Which resources are they requesting? Of course, we know there are all sorts of logging and auditing tools lying around. The problem doesn't lie in accessing the information, but rather picking out the useful bits. If you run a high-security environment, for example, you will have to figure out how to track access to specific resources. Essentially, an audit is a... Read moreConfiguring Hyper-V in Windows 2008
It will be helpful to begin by understanding a few important terms as follows:
Virtual means not real and refers to something that is just conceptual with no physical reality whatsoever, this term finds popular use among computer experts/scientists. It can be compared to an engineer’s design of a road; the design is not the actual road but is rather an imaginary road. A computer scientist can refer to the road design as a virtual road.
Virtualization: When used in computing, virtualization refers to the creation of a virtual version of some devices or computing resources...
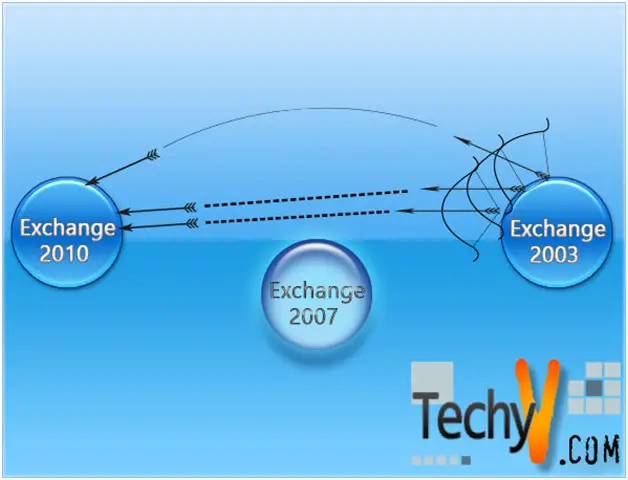
Read moreHow to migrate from Exchange 2003 to 2010
Sometimes all the planning in the world won't do. You know very well that Exchange Server 2003 is simply crumbling away in the face of demands in the late nineties. So you take a look at 2007, and then decide to wait for the first Service Pack, which popped out a little bit sooner than you'd expected. Before you know it 2010 is out, and you've made all these plans for migration.