Archive
LCS 2005 versus OCS 2007
In most enterprises the real time communications and instant messaging (IM) became important communications tools since late 1990's. But in many enterprises the implementation of these systems has taken place in a disorganized fashion.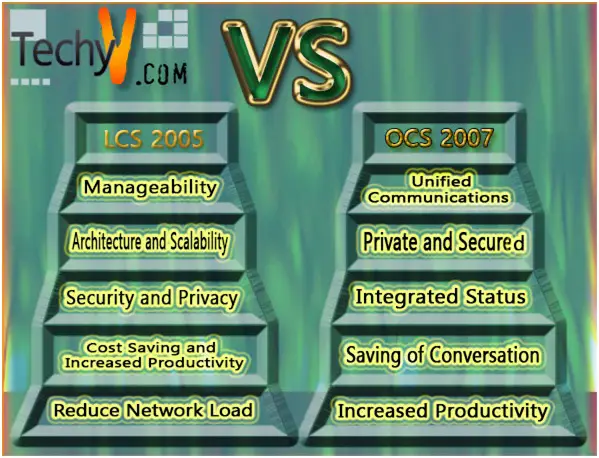
AD Auditing
Chalk it up to human nature, but all part of the job when you are running servers. Political scientists put it nicely when they ask, "Where and when does who gets what?" Who's logged onto which computer? Which resources are they requesting? Of course, we know there are all sorts of logging and auditing tools lying around. The problem doesn't lie in accessing the information, but rather picking out the useful bits. If you run a high-security environment, for example, you will have to figure out how to track access to specific resources. Essentially, an audit is a... Read moreHow to migrate from Exchange 2003 to 2010
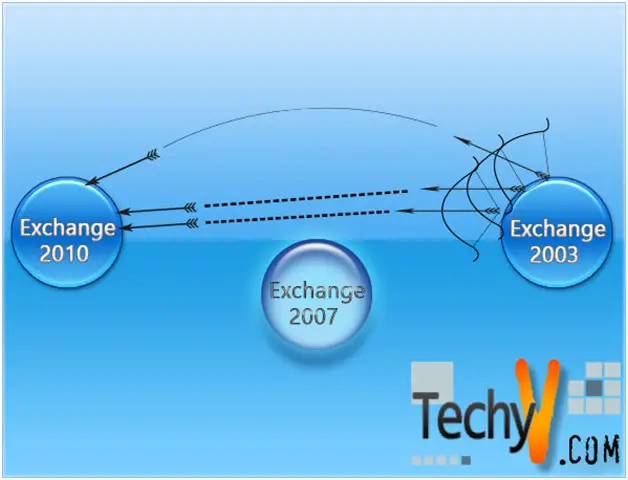
Sometimes all the planning in the world won't do. You know very well that Exchange Server 2003 is simply crumbling away in the face of demands in the late nineties. So you take a look at 2007, and then decide to wait for the first Service Pack, which popped out a little bit sooner than you'd expected. Before you know it 2010 is out, and you've made all these plans for migration.