Archive
Panda Antivirus
Panda Antivirus prides itself with stability, speed, and holistic protection against viruses, spyware, and malware. It is efficient when it comes to virus removal and detection. It ensures your computer system has full protection.Cloud computing vs. data center
Cloud Computing – A Brief Overview Cloud computing is a kind of internet computing wherein the shared software, information, and the resources are provided to the computers as well as the other devices as per the demands such as the electricity grid.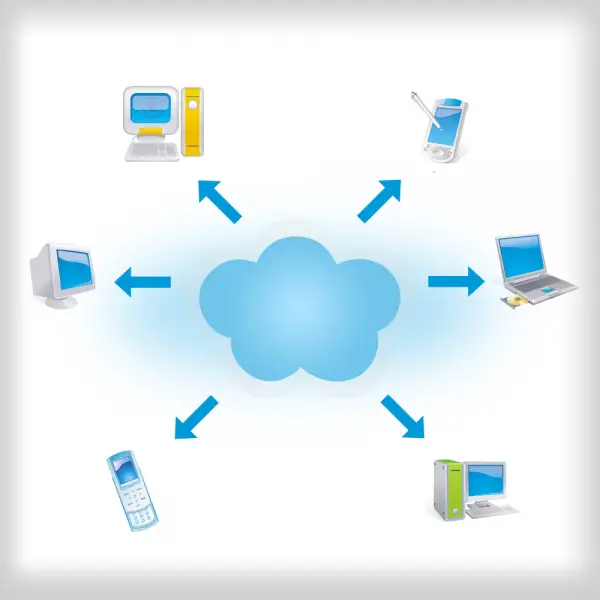
Wireless Lan
WLAN or technically speaking, wireless local area network is the most admired technological innovations created by mankind. Using this technology, two or more devices can stay connected even without the hassles of using physical cable wires that will connect them together.Convergence and Overview to Some Network Peripherals
Convergence is the perfect term to describe computer networks. Computer network or merely called a network is simply defined as a way for computers to speak or communicate with each other. With the benefits of a network, life becomes more practical and convenient. Establishing communication with different people from various spots in the world is just some clicks away, reducing cost and time constraint. Through network, computers can send file to each other, receive emails from each other, share various hardware and resources with each other, set up a security, preserve information and... Read moreLAPTOP VS NOTEBOOK
The world of computers. Computer-related technologies and computer products are becoming more and more complex as the manufacturers of these technologies and products try to make them more suitable to the user's requirements as well as making them more user-friendly and easy for the normal people to use without the requirement of technical knowledge. Due to these reasons, computers and their related products have become cheaper, easy to use and they enable their users to achieve their tasks in a much more effective and efficient manner. There are many computer technology related devices or products that cannot be... Read moreCloud Migration Software, Their Benefits, Features and Why to Use Them
Cloud Migration Tools Do you want to migrate towards the cloud and want such a tool to do so? Well, this is how you can precede your stuff without mislaying precious metadata.Checkpoint Firewall – the best at all times
There are a number of security software around that claim to be more effective when it comes to the protection of networks and overall business processes. Most of them come along with different hardware, which make the processes of protection more effective.CLOUD COMPUTING - IAAS
The term IAAS stands for a company acronym Infrastructure as a Service. The service is provided to the consumers to store, process, and facilitate the fundamental computing resources. In this service, the keeper can rely upon for taking chances including operation systems and applications as well.Back up: History, Types and Devices
In our everyday life, a lot of things come and go, but we need something we can go back to for us to continue and base our decisions from. That is where the word back-up comes in. Back-up is an idiomatic expression that means ‘a reserve or a substitute’. This word is mostly used in the ‘Techy’ world, as what we call the fast-paced world of technology.- Normal backup is also known as the full back up and the most... Read more











