Archive
Information mining, otherwise called learning revelation from databases, is a procedure of mining and dissecting measures of information and extricating data from it. Information mining can rapidly answer business addresses that would have expended a great deal of time. Some of its applications incorporate market division – like recognizing qualities of a client purchasing a specific item from brand, misrepresentation location – distinguishing exchange designs that could presumably bring about an online extortion, and market-based and inclines examination – what items or administrations are acquired together, and so forth. This article centers on the different open source alternatives accessible and...
Read moreThe security business has been around for a considerable length of time, thus have a portion of the best-known affirmations. ISC2's Certified Information Systems Security Professional (CISSP) for example, was discharged in 1994 and ISACA's Certified Information Systems Auditor (CISA) goes back to 1987. This vast scale movement towards the cloud – supported by speculation from big business – is a splendid open door for experts who can demonstrate their cloud learning with perceived affirmations. Confirmation, preparing, and encounter is three of the best four most vital properties while contracting for a cloud-related position, as indicated by Microsoft and IDC. 1. Certified...
Read more"Enormous Data" includes the measures of information gathered about each on earth and their environment. On the off chance that the aggregate source created in 2012 is 2500 exabytes, at that point, the aggregate data produced in 2020 will be around 40,000 exabytes! Such information’s utilized as a part of different courses for enhancing client mind administrations. Be that as it may, the enormous measures of information produced are exhibiting numerous new issues for information researchers, especially concerning the protection. 1. Approval and Filtering of Endpoint Inputs End-focuses are a piece of any Big Data accumulation. They give input information to capacity,...
Read moreAs Mobile Device Security is involved the security of various highlights, for example, Information protection and security highlights Consent confinements for snoopy applications A boycott for undesired calls Encryption usefulness Google's Android is exceptionally portable working frameworks that can satisfy all these cell phone security challenges if select the correct security applications from Google Play Store. 1. TextSecure Private Messenger (Free) There is an immense number of secure informing applications accessible in Play Store. However, the inconvenience part is that the majority of them work just if both the gatherings utilize a similar for encryption to work. TextSecure breaks that boundary and works with standard SMS instant...
Read moreMicrosoft Windows working framework is the most generally utilized programming far and wide, and with a large number of PCs running the OS, it prompted MS building up a great deal of supporting instruments for servers, application improvement, and cloud stage to adapt up to developing needs. From a trying understudy or employment searcher's point of view, finishing any of the best and most sought-after Microsoft accreditations in 2018 will furnish them with an imposing profession that every one of these courses knows about the OS that the organization has created. 1. Microsoft. Net: ASP.Net MVC 5 Before you take the...
Read moreOur reality is a social group, and all is a direct result of systems administration organizations. The Internet is conceivable because of system gadgets as it were. Online networking happens to exist because of the web. Cell phones survive as a result of systems administration segments fitted to it. So in general, this world is a family in light of the items fabricated by Networking Companies. 1. Brocade (www.brocade.com) Brocade Communications System, Inc. is a USA based organization established in 1995 by Seth Neiman, Kumar Malavalli, and Paul R Bonderson. It is spent significant time in information and capacity items....
Read moreThe iPad is a fabulous tablet. It can utilize for profitability. It can use to peruse the web. You can associate it with your TV. You can make it as a radio. Hell, it accompanies its very own aide, so it is no big surprise it can without much of a stretch supplant your PC. Gracious, and did I specify its influences as a convenient amusement to reassure? Regardless of whether we could disregard a 'best amusement' involves feeling, distinctive players adore diverse types, so who is to state that the best pretending diversion on the IPad is any superior...
Read moreIT security accreditations are a method to lift up.
"The confirmation face off regarding seethes on," said Jason Kent, CTO at AsTech. "From one perspective, there are a lot of gifted experts that I would state are specialists and have no confirmations. There are many good people with numerous confirmations."
Security accreditations demonstrate fundamental learning levels and regularly show the individual's actual advantages.
Top 10 Information Security certification courses are:
1. CompTIA Security+
Security+ supported by CompTIA. Security+ accreditation holders are perceived as having abilities, elaborate learning and aptitude in numerous security-related orders.
 While Security+ is a section...
While Security+ is a section...
Hard disks are mechanical gadgets, and, similar to every mechanical appliance, they can come up short without taking note. Some hard plate disappointments are avoidable, yet numerous others are represented just by fortunes and shot. Not at all like state disk or USB streak drives, which have no moving parts, each customary hard drive has an exceptionally delicate part called the read/compose head. This head resembles a smaller than usual gramophone needle, and its motivation is to change the platter's attractive field into electrical current to peruse information from the circle and transfer electrical current into a different area to...
Read moreSystems and laptops don't have CD or DVD scholars, and you require a bootable USB drive to stack or introduce working frameworks. There is a considerable measure of instruments out there to make bootable USB drives from ISO records. A few apparatuses enable you to make solitary OS USB drive while some others are multiboot drive makers. These bootable drives are anything but difficult to convey and offer quicker composition speeds. Here are the ten best-tried programming to make bootable drives.
- RMPrepUSB
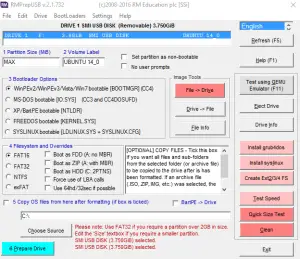 Key Features
Key Features
- The interface is intricate and jumbled.
- Can make various segments on a bootable USB drive
- Fit to make the two Windows and Linux bootable drives.
- Read and Write Speed Test on the USB drive
- Backings four record frameworks that incorporate FAT16, FAT32, NTFS and exFAT
- An alternative to making an ISO document from Bootable Drive
- Suggested for Advanced client
- WinToBootic











