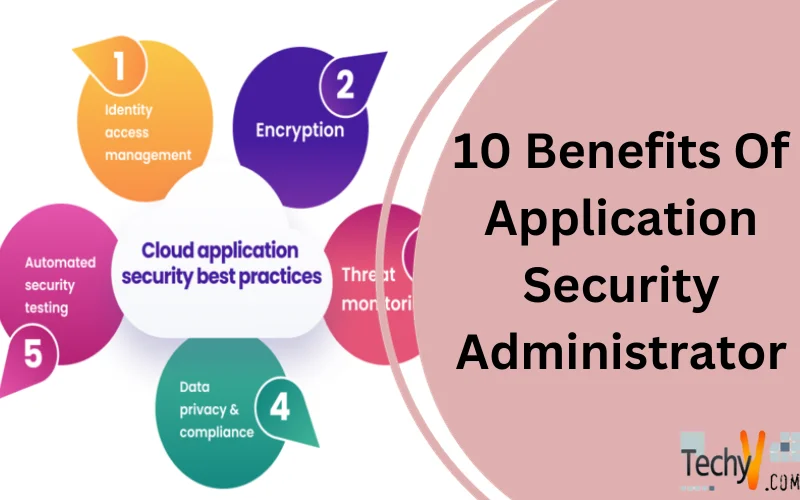
What Is An Application Security Administrator?
Application Security is developing, deploying, and testing an application’s security features to avoid security loopholes from hazards. It defines the security calculates needs at the application stage to protect the application code and data from cyberattacks.
Application security involves software, hardware, and processes to reduce security loopholes. Data Encryption, Antivirus, firewalls, etc. It is used to avoid denied access to the application. It also involves security examinations during the application development and purpose level. It also helps execute various security rules and approaches to secure the application even after the deployment.
Application security administrators are critical in protecting digital assets and sensitive information by creating and maintaining robust security mechanisms within software programmers.
Why Do Businesses Need Application Security?
Data privacy and security are the most essential concerns of every business, but well-defined application security protocols from cyberattacks. A data breach can result in a considerable loss of consumer trust and confidence and the downfall of reputation overall.
Application security helps to avoid security loopholes associated with the application. Application consumers and users can be ensured of data protection from cyberattacks with suitable data security, privacy, and protocols.
- The key benefits of using application security are as follows:
- Protects private information from data stealing.
- Reduces the bring-your-Own-device (BYOD) risk of application protocols.
- Minimizes the attack surface and loopholes in the application.
- Offers better visibility and control over applications despite security policies and ports used.
- Reduces hazards from both internal and third-party sources of application.
- Secures the user data and improves customer confidence.
It Finds Vulnerabilities
DAST is an efficient way to find loopholes in web applications. It tests websites while they are running to locate what natural hazards it is prone to from the outside world.
It Can Detect Crucial Vulnerabilities
DAST can recognize crucial loopholes in web applications that could be utilized by hackers. It makes it an effective method for helping you secure an application that may be organizing sensitive data.
It Finds loopholes That Other Tests
Security assessments may only look at general security and not specific hazards, whereas static code evaluations cannot test running applications. DAST can assist in filling these gaps and offer more comprehensive content.
It’s Non-intrusive
DAST is a non-intrusive testing method, meaning it does not need to administer the source code or launch any agents on the system being tested.
It’s Easy To Use
DAST tools can be more straightforward and don’t need technical skills or knowledge to regulate. It makes them ideal for management that doesn’t have a devoted security team.
It’s Scalable
DAST is a scalable testing strategy, meaning that it can be pre-owned for small or large applications.
It Helps With Observation
Management required to meet observation needs may find DAST an essential tool in helping them achieve observation.
It Helps With Risk Management
Management uses DAST as a segment of a broader risk organization method to help recognize and mitigate potential risks.
It Can Be United Into Your SDLC
DAST can be united into your software development life cycle (SDLC), offering continuous security testing throughout the application development procedures. It will in turn save costs and minimize testing times in the future.
It Helps To Enhance Security Posture
DAST can help to improve a website’s overall security posture by identifying security flaws. Most DAST tools offer tips to fix the faults they detect, which allows for remediation.
1. Risk Mitigation
Application security administrators are necessary for recognizing and mitigating potential security risks within software applications. By managing thorough risk assessments and executing protective measures, they help manage enterprising address loopholes, minimizing the likelihood of security breaches.
2. Data Protection
Securing sensitive data is a top order for any management. Application security access executes encryption, access controls, and other evaluating to ensure the confidentiality and principle of data, securing it from denied access or manipulation.
3. Regulatory Conformity
In the regulatory landscape, conformity with data-securing laws and industry regulations is non-negotiable. Application security access stays abreast of including conformity requirements, ensuring that applications adhere to essential standards and regulations.
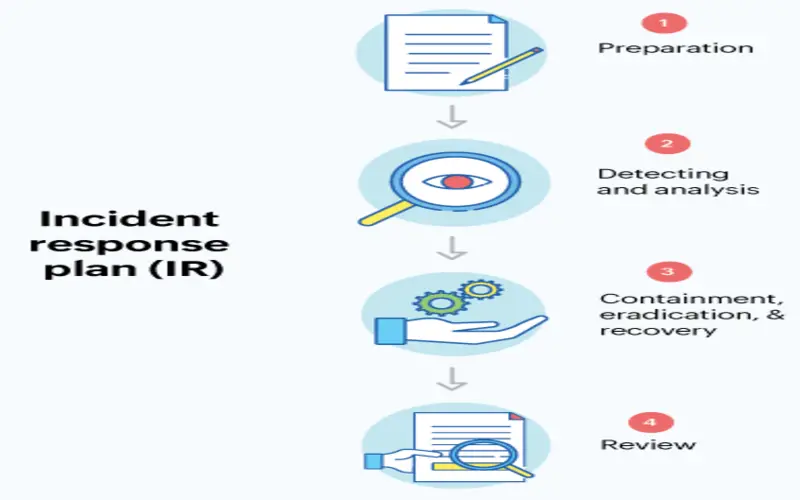
4. Events Response
Rapid response is crucial in security events. Application security assesses develops and executes event response plans, helping organizations minimize the effect of security breaches and swiftly reserve normal operations.
5. Secure Development Applications
Consideration with development teams and application security administrators promotes secure coding applications. They integrate security into the software development life cycle, supporting a proactive approach to identifying and resolving flaws early in the development process.
6. Loopholes Organizations
Continuous observing and assessing application loopholes are vital features of an application security administrator’s role. By remaining ahead of potential hazards, they allow management to apply timely patches and updates, minimizing the risk of operation.
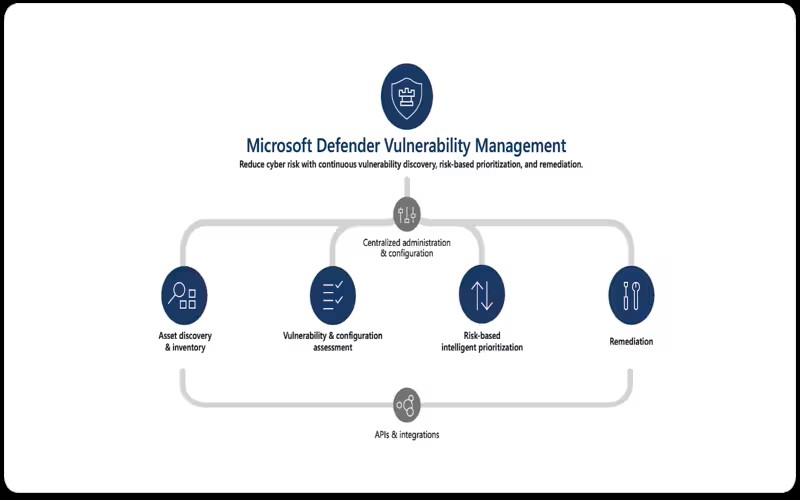
7. Security Attention Training
Educating employees about security best custom is crucial in avoiding social engineering attacks and other human-centric loopholes. Applications security access develop and deliver security attention training program to ensure a well-informed workforce.

8. Security Audits And Assessments
Regular audits and assessments are essential for analytics and the efficiency of security controls. Security access conducts a thorough investigation of applications, recognizing areas for enhancement and implementing necessary changes to improve security posture.
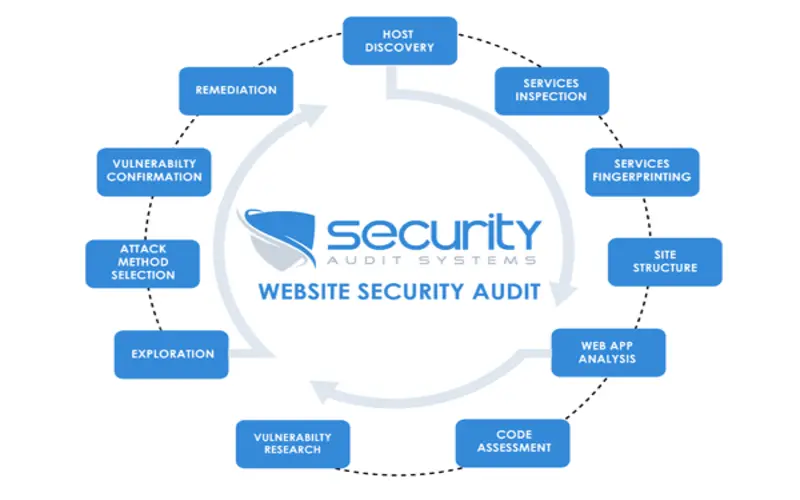
9. Secure Organizing Management
Organizing issues can find loopholes. Security administrators enforce secure organizing management methods, ensuring that software applications are managed to reduce potential security risks.
10. Continuous Enhancement
Cybersecurity is a practical field, with new threats developing daily. Application security access engages in continuous learning, staying updated on recent security trends, innovations, and flaws. This commitment to ongoing development is critical for adjusting to changing security landscapes.