Endpoint protection has become the essential aspect of IT security for protecting business and customer data and identities. When a device connected to a corporate network has a malware-infected application, the hacker will channel the machine to steal information or perform keylogging operations without user consent. It requires strict endpoint security and full security protocol for endpoint security and network protection. Endpoint security tools have evolved over the past few years. An endpoint security platform must provide anti-virus, encryption, and application control capabilities to secure devices that access your data and monitor and prevent risky activity. An endpoint security tool should include the following features.
10. Third-Party Integration
Endpoint security tools communicate with other security systems in the organization’s environment. These tools need to share and capture threat intelligence and learn from each other. Using an API system, endpoint security products should integrate with other security tools, such as Active Directory, intrusion prevention, and network monitoring.

9. Advance Endpoint Security
Although the threat from inside the business is significant, preventing external attacks is an essential requirement. The best endpoint security system protects against known security threats and zero-day attacks. These systems can block attacks from email, social networks, P2P applications (such as Skype and Dropbox), and websites. That ensures that your devices and employees are protected where they use the internet the most.
8. Server Security
When looking for a new security solution based on a set of requirements, ensure that all your endpoints are protected. Servers are a particularly sensitive endpoint, so it’s essential to choose a system that can save them. Ensure your system can block threats on your collaboration servers, data storage servers, internet gateways, and mail servers.

7. Awareness Of Security Measures
Employees should be trained to secure endpoints. They need to know the difference between malicious and authentic mail. Equipping employees and users with adequate knowledge of security measures will prevent data loss and stop the exploitation of security vulnerabilities.
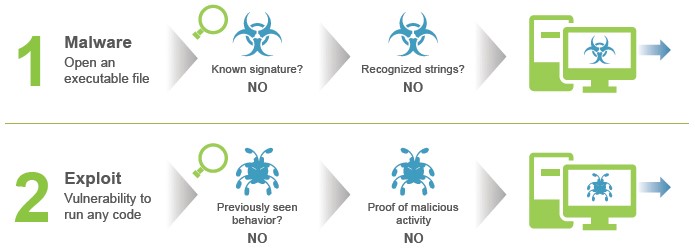
6. Rapid Detection
Detecting threats as early as possible is essential. The longer a threat lingers in the environment, the more it spreads and the more damage it can cause. Many endpoint security tools offer real-time detection.
5. Machine Learning
Vendors who use advanced technologies like AI and machine learning can keep your security infrastructure relevant to the ever-changing threat landscape. Machine learning can analyze significant amounts of data to understand endpoints or user behavior. You can use this information to identify suspicious or malicious activity and alert security personnel or trigger automated actions before threats execute on your device. It combines multi-factor authentication, file system level scanning, and permission authorization to prevent data loss and ensure overall security.
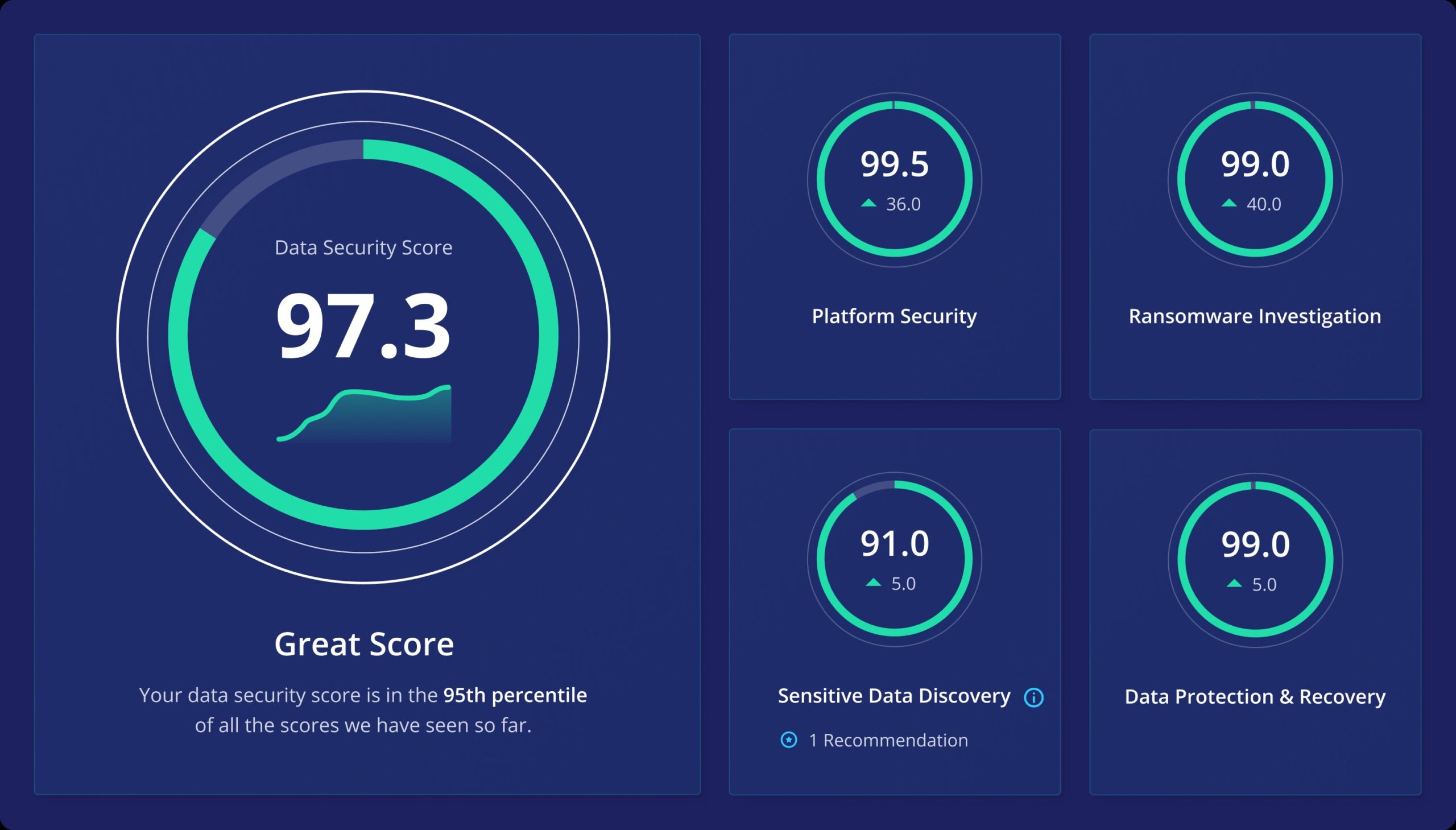
4. Data Security
Data security is a complete endpoint security strategy with a data protection system. Restrict device access to specific users to ensure that only relevant users are authorized to access data and thus do not expose data to unauthorized users. Organizations must ensure
• Network segregation
• Data Encryption
• Monitoring access to data
• Endpoint security management systems need to be well equipped to manage the protection of data assets.
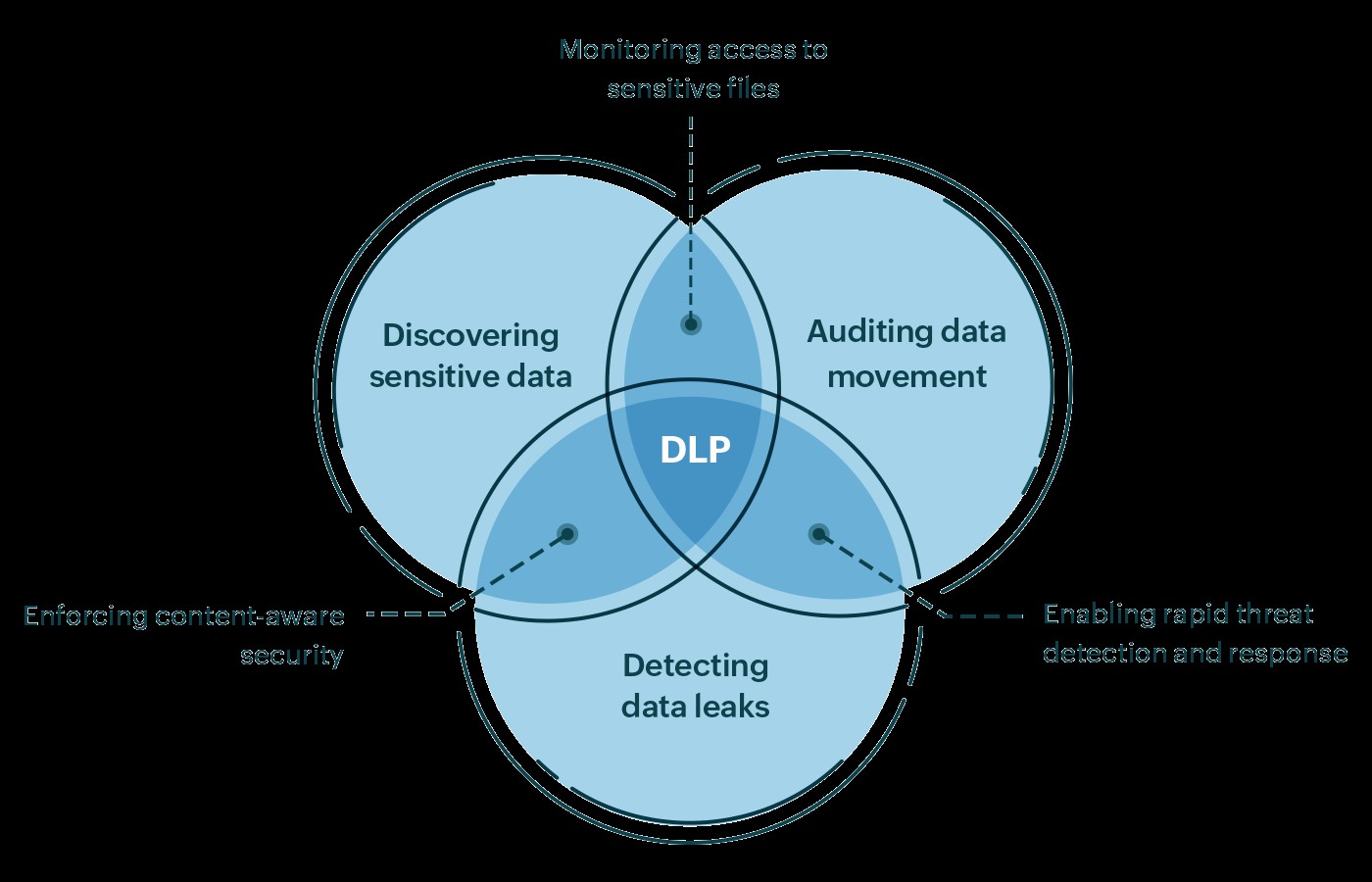
3. DLP Or Data Loss Protection
DLP prevents access breaches caused by insiders, including employees, and intentional or unintentional data loss in the event of a system breach. DLP allows organizations to intercept files transmitted via email or group collaboration tools.
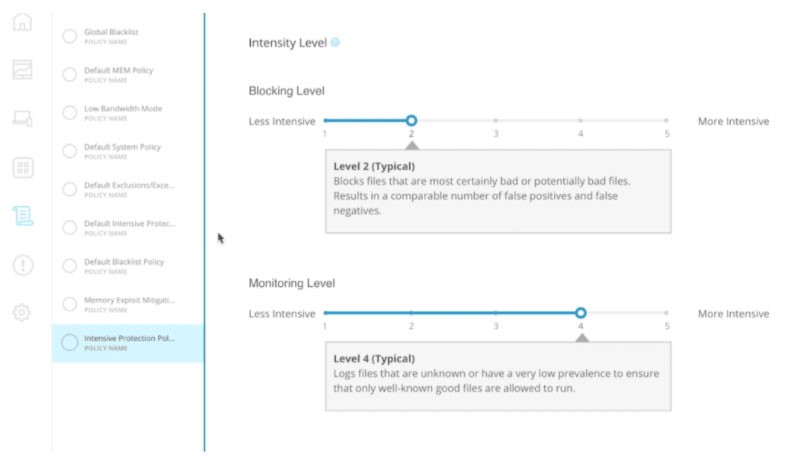
2. Configuration Management And Management Option
These tools provide a centralized dashboard to manage all your other endpoint security requirements and features. System administrators use configuration management to modify and set policies, receive alerts, view audit trails, and detect when users attempt to bypass them. That allows for clearer visibility into threats and allows administrators to make exceptions when users need access to specific applications or information.
1. Centralized Security Management Portal
Managing thousands of devices, computers, and other terminals with just manual intervention are beyond human potential. Therefore, an integrated security solution would be a plan to avoid redundancy and human error. A centralized security management system is all you need to monitor and manage network integrity and endpoint security.
• It has user-friendly features to wreak the havoc
• It has lesser security issues
• It is affordable
• It provides an instant response in case of suspicious intrusion.



















