1. HashiCorp Vault
HashiCorp Vault is a mid-variety solution that offers encryption as a service. This forum allows you to better defend sensitive records inside the cloud, as well as provide higher visibility on your company’s senior control. Encrypting and deleting information encryption is a simple technique the use of available APIs, consisting of UI, CLI, and HTTP. FIPS a hundred and forty-2 is authorized with the aid of organizations that require compliance with sure criminal necessities. It’s far this adaptability that facilitates making HashiCorp Vault one of the top records protection gear. HashiCorp Vault supports the use of tokens, passwords, certificates, or encryption keys. Such considerable help can shield your most sensitive facts. It has an unfastened trial application, so you can begin the usage of this system and spot it if you like it. HashiCorp also offers a threat to an open-source option to developers. Open source permits extended customization alternatives for your commercial enterprise. HashiCorp also offers a complete series of tutorials in your app, which incorporates use on any home windows tool.

2. FortiGate Next-Generation Firewall
Firewalls are not designed for high-overall performance or combined cloud environments. If you have severe statistics middle necessities, you need a cause-constructed solution that serves because the first line of defense for your community. The FortiGate subsequent-era Firewall is a network safety platform designed to guard agencies against internal and external threats in complicated cloud-based totally complexes and a hybrid hyper-scale records middle. It sets itself as much too provides the fastest viable lightning protection. Those regular updates ensure ultra-modern security.
3. Egnyte
Disbursed personnel want to get the right of entry to content and other assets to perform their duties efficiently. These files may be allotted to more than one cloud storage company, network drives, domestic workplace computers, and limitless different places. Stopping unauthorized get entry to this information at the same time as allowing faraway employees to get the right of entry to it could be a project without the proper answer. Egnyte is a primarily commercial enterprise content material control platform that offers records control, control, and protection for organizations with an allotted group of workers and others that require similar stages of flexibleness. It consists of many beneficial features to protect touchy facts without violating them every time, anywhere get entry to content material.
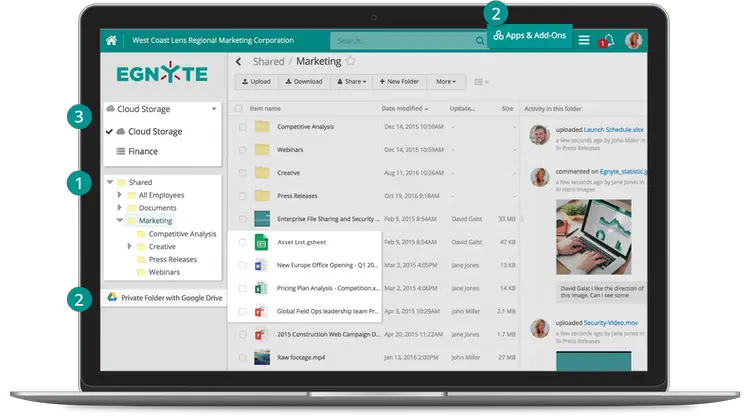
4. Data Recovery And Distribution Software
One key aspect of records safety lies within the separation of facts and acquisition. The facts sorting tool will be able to experiment with your records repositories to filter and label vital or perceived data kinds based on enterprise privacy requirements, which includes PCI DSS, IP, and GDPR information. Filtering and labeling software provides specific digital signature information based on its class so you can focus statistics security resources on those hubs. Mixed with other safety software, touchy data detection and partition software programs can offer your crew an extremely high level of understanding of the vicinity, protection, and motion of sensitive statistics documents.
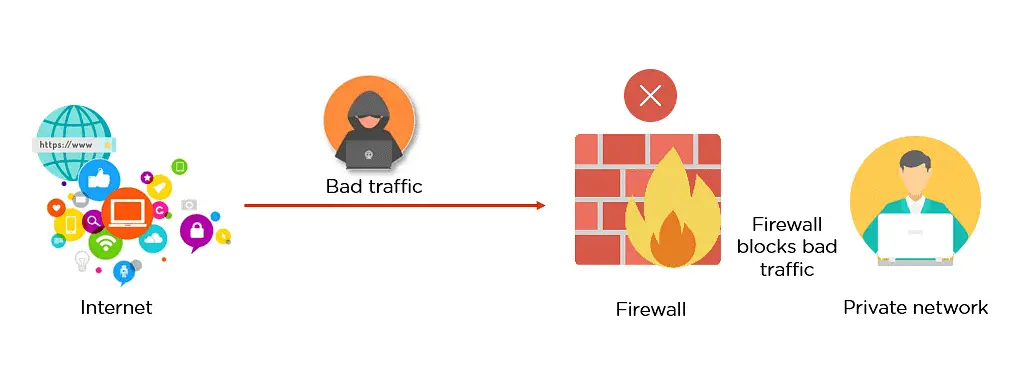
5. Firewall
A Firewall is mostly a laptop and the primary line of defense for the community. The Firewall protects undesirable traffic, including viruses, from accessing your laptop network. A firewall also can guard easily on hand ports, limiting the hazard of a capacity crook assault if they can be in a position to break your organization’s firewall. You must bear in mind each software and hardware firewall solution is specifically close to information protection. The Firewall comes fashionable for Mac applications and home windows operating systems, however, corporations can buy their very own, commercial enterprise firewall.
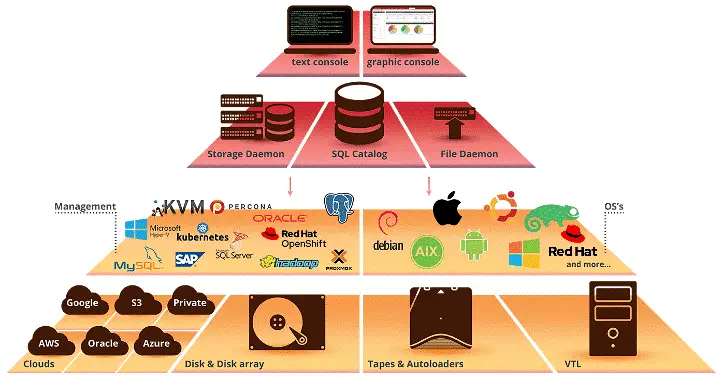
6. Backup And Recovery Systems
A backup and recuperation solution is wanted for the enterprise to recover records documents and return to running standards in the event of a facts breach. Normally, backup files should stay encrypted, but your IT head or system administrator needs to be capable of getting the right of entry to them as quickly as they may be wished. Backups should be executed often, and healing plans have to be written down, so humans recognize the orderliness of the processes. Backups are commonly available on Mac and home windows OS but can be performed with the comprehensive protection software program.
7. Antivirus And Anti-Malware Software
Antivirus and anti-malware software is widely used in both personal and commercial use to stop, guess, viruses and malware on incoming networks. Since viruses and malware operate in different ways, this software can identify and obtain malicious code to remove Trojans, viruses, and rootkits that attempt to steal, damage, or alter sensitive data.

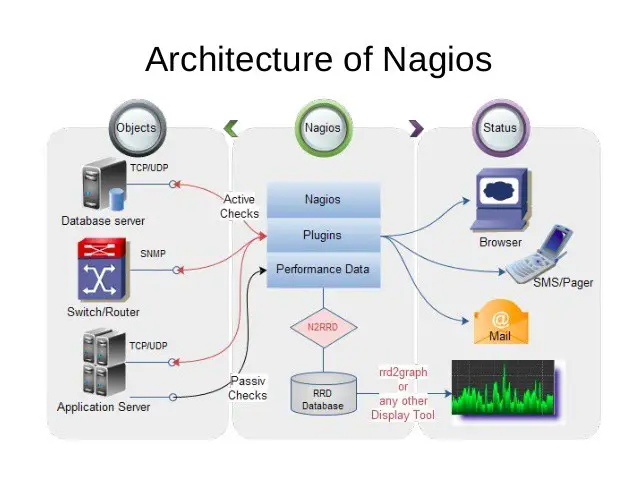
8. Nagios
Nagios uses a basic approach to network management. It is one of the most effective network security tools for both Cyber Security professionals. Nagios tracks strangers, devices, and networks and provides real-time alerts. It allows users to choose which notifications they would like to receive. It can track network services such as HTTP, NNTP, ICMP, POP3, and SMTP.
9. Tcpdump
Tcpdump is a compatible application for Mac, Windows, and Linux that precedes the market-leading tool, Wireshark. It set the standard for network security. Tcpdump continues to be an effective network sniffer in a new way.

10. Splunk
One of the handiest apps with a single interface, Splunk is the appropriate device for the ones in a price range. A paid app with unfastened versions is available for a restricted time. Designed for real-time statistics and history search, Splunk’s effective seek function makes monitoring programs clean. Splunk is one of the quickest and maximum uncontrollable network scanning tools.
















