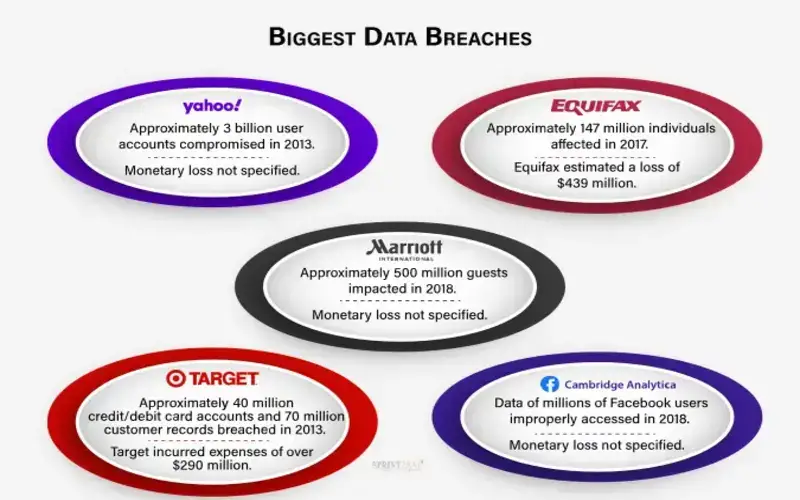
What Is Continuous Penetration Testing?
Conducting a penetration test at least periodically means continually accessing your security posture. Continuous penetration testing is a subset of ethical hacking devoted to securing the security posture of your business. It frequently shows the flaws exploited by hackers to breach your management IT bubble. The modern DevOps reach is always facing an ever-changing perimeter and hazard landscape. Continuous penetration testing is essential to respond to it. Here are some factors that can point to a need for continuous penetration testing involve:
High-Value Assets: If a company has secure important assets, such as sensitive data or essential infrastructure, continuous penetration testing can aid in identifying and correcting vulnerabilities that could be exploited by attackers.
Compliance needed: Enterprises that work in regulated fields like healthcare or business may have to cohere to rules that often call penetration testing.
Frequent Changes to the Network: Continuous penetration testing can help in recognize and address loopholes that may be introduced as an outcome of network changes regularly.
Previous Security events: if an organization has accomplished security events in the past, continuous penetration testing can help recognize and remediate loopholes that may have been devoted to those events.
Risk Appetite: If management has a high-risk appetite, continuous penetration testing will allow them to have a broader understanding of the management security posture, thus minimizing the risk of attacks.
1. Considering The Frequency
The frequency with which a pentest should be performed is usually determined by how frequently you develop new features or make significant modifications to our networks/codebase/infrastructure, as well as how critical the newly evolved feature is. Always think of the security suggestion and the possible defeat case schemes.
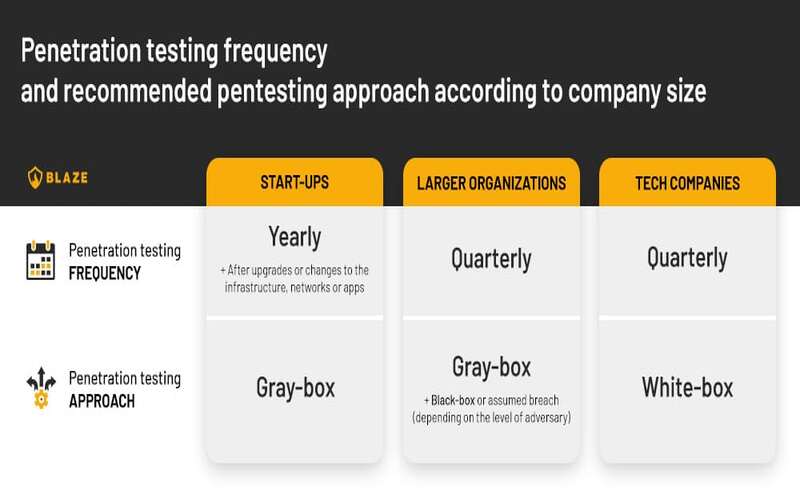
2. Use Both Manual And Automated Techniques
The methods and techniques will be pre-owned throughout the pen test. A service that employs a combination of manual and automated testing methodologies. For example, automated penetration testing will scan and try to utilize loopholes found on the network or application. A manual strategy is needed to identify out-of-the-box security rules set in say Microsoft or security misconceptions that may be present. Augments and extends your staff’s knowledge transform. Pentesters will have a deep Your IT staff can administer pen-testers for a comprehensive of your environment through continuous testing. Closer connection with your security testers will also bring more expensive insight into reduction planning and solutions.
3. Forces Better Conveying
Complicated mitigation solutions that take time to implement typically necessitate additional communication. Consultants help with mitigation methods, and all development is tracked through an interactive web portal. Testing status and action are registered for actual time and historical views. Visibility into all testing activities is always available.
4. Schedule Continuous Penetration Tests Regularly.
Scheduling your tests provides better effectiveness and a lot less stress. Scheduling tests regarding changes made to the application ensures that possible new loopholes are found and sold with earlier they can cause damage.The scheduler is one feature in Beagle Security’s weapons that will help you acquire the best results from a penetration test. It allows you to plan exams to keep up with your needs, with time gaps ranging from a test every week to bi-yearly testing. The capability to choose the time zone also enables you to schedule the test period when your servers are less busy, enhancing the overall effectiveness of the test.
5. Continuous Penetration Testing Slow Down Development
Continuous penetration testing does not slow down development. It means the security experts executing the testing get to know your project, learn how the group functions, find out the security priorities and manufacture communication channels. With this basis in place, you can construct a program that combines seamlessly with your development procedures and makes it possible to reveal more protected software on time and within budget.
6. Agile And Fast Product Growth Maximizes The Risk Of A Security Breach
Digitalization puts ever high pressure on the data systems product developed. The security testing done on the earlier version does not contact the system’s security today. Just as a product contract, it is a process is testing. Cyber attackers are particularly interested in the following:
- Business crucial systems
- Apps that protect sensitive or confidential information.
- Systems related to essential infrastructure.
- In common, all web apps are available publicly online.
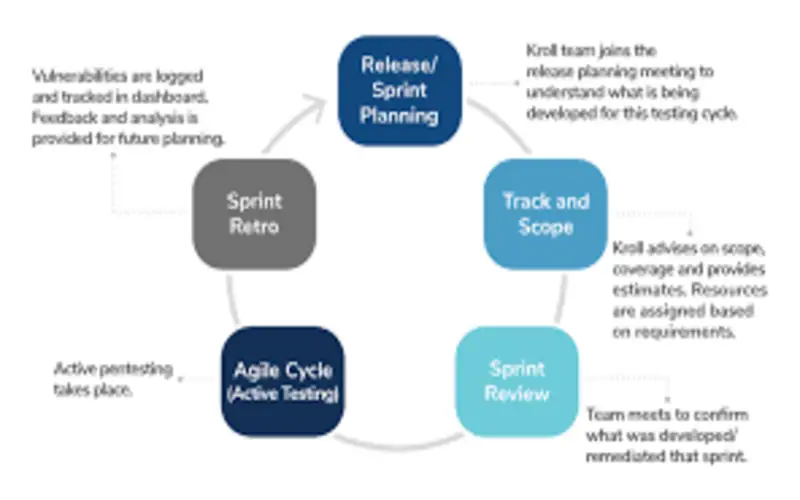
7. Risk Recognizing And Prioritizing
Continuous penetration testing enables better analytics of web applications across internal and external security. Not only does it include web application pen-testing but also testing of the network security perimeter. It aids in a better understanding of security standards and the level of protection required to protect your company’s assets. Also, you can optimize the risk to your organization and avoid potential attacks.
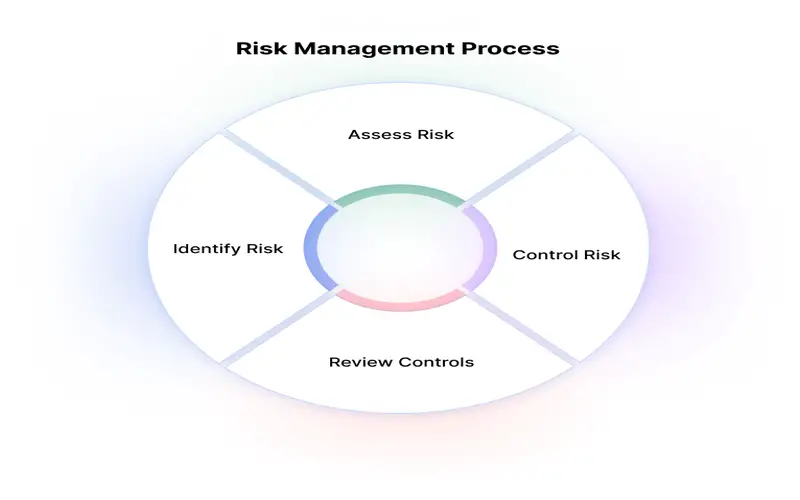
8. Captures Actual-word Conditions
The schemes of the hazards landscape online are continually changing today. Random pen tests like the annual ones can become outdated after two weeks. Continuous penetration testing will keep your protection measures up the present needs. Your security teams will be one step ahead of the hackers. It will have a positive effect on the security of your infrastructure.

9. Better Avoid Hacks And Infiltrations
Penetration tests are assumed of actual attacks and provide and give you a clear idea of your network’s objection to hackers. Regular penetration tests will analyze your cybersecurity and uncover all the security holes that might cause catastrophe. These often attack simulations enable you to take curative steps before an attack.
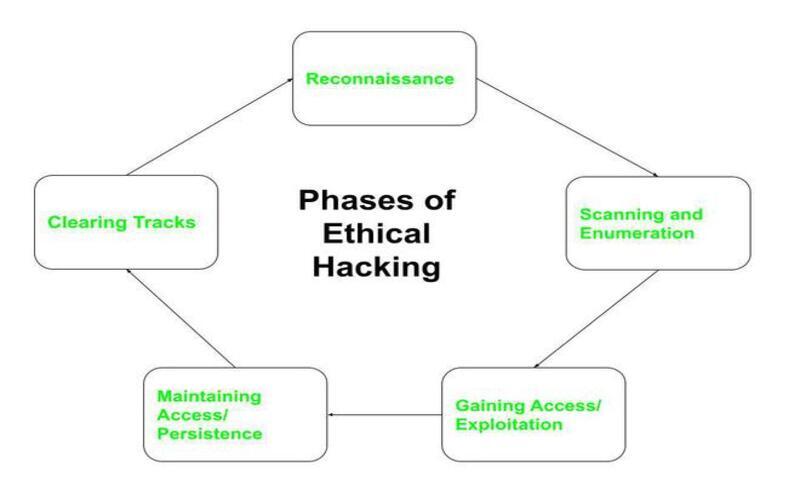
10. Prevention Of Costly Data Breaches And Downtime
If a cyber-attack becomes profitable enough to break your security perimeter, it results in a cascade of losses. The cost of data loss, curative, rebuilding, and downtime entirely might cost you a lot. Financing a portion of this total cost might save you from all these problems and financial blows. Bringing a company back on track after a hacker is quite tricky. It makes your clients and stakeholders lose confidence in your management setup.