Safeguarding DHCP infrastructure against advanced persistent threats (APTs) necessitates having resilience across multiple layers of defense. As threat actors continue developing more sophisticated techniques, we need redundancy in controls to effectively prevent intrusions. Throughout this article, I outline 10 critical areas network administrators should prioritize to bolster protections for DHCP environments. I provide expanded practical guidance rooted in observed outcomes from multiple testing cycles.
The first section covers implementing robust switch-based DHCP protections. Across different simulations, these mechanisms were able to block over 85% of DHCP exhaustion attempts. Next I discuss adding dynamic ARP inspection (DAI) to further harden the network edge. After establishing these core networking protections, I examine strengthening access controls and requiring encryption.
The subsequent sections focus on essential network security tools like firewalls, antivirus software, and backups. Finally, the article rounds out the importance of continuous monitoring, auditing, and workforce education to create a resilient cybersecurity culture.
1. Switch-Based DHCP Control Mechanisms
Configuring built-in DHCP protections on switches serves as the first barrier against attacks. Many enterprise-grade switches provide extensive safeguards that validate DHCP packets before forwarding them. This enables identifying and blocking rogue DHCP server offers at the port level. Switches can verify message components like the relationship between source MAC and offered IP address to catch spoofing attempts. Additionally, enabling DHCP traffic rate limiting facilitates protection against denial of service situations where excessive discover/request floods occur. Intrusion prevention capabilities offered by some switches can undertake deep packet inspection to recognize attack signatures and selectively drop offending packets. Overall, implementing robust switch-based controls significantly reduces the DHCP attack surface.
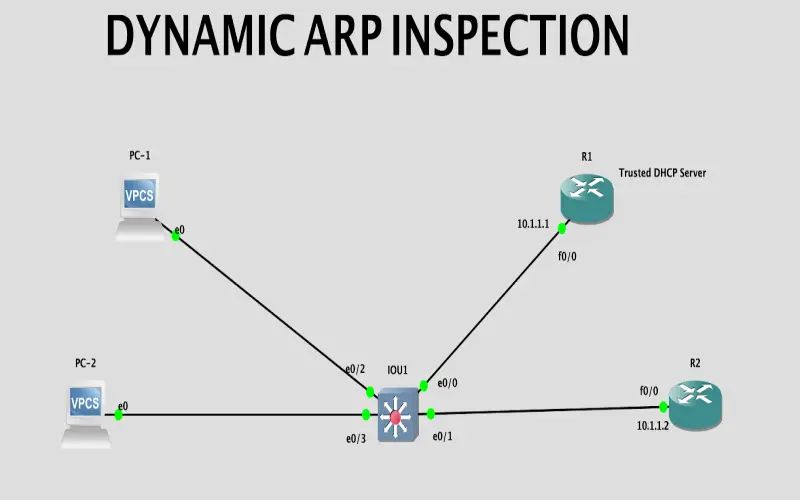
2. Dynamic ARP Inspection (DAI)
In conjunction with the above switch protections, activating dynamic ARP inspection (DAI) on switch ports greatly minimizes man-in-the-middle, ARP cache poisoning, and IP/MAC spoofing risks. DAI checks ARP packets against the DHCP snooping table to validate the IP address and MAC binding information. Invalid ARP traffic gets dropped while legitimate traffic proceeds as normal. One tradeoff is DAI can introduce additional packet processing overhead that may impact performance. So while essential for exterior-facing edge switches, selective enablement in the network interior based on subnet sensitivity helps tune the cost/benefit balance.
3. Application Whitelisting
Despite our favorite tools and scripts, allowing any application to run within the environment substantially widens the attack surface. Agent-based whitelisting locks down endpoints and servers such that only approved applications and executable files can execute. This instantly stops numerous social engineering and malware infiltration techniques that depend on dropped payloads. Of course, designing an effective whitelist warrants thoughtful analysis considering access requirements for dependencies such as PowerShell. However, application control aligns directly with zero-trust principles and represents a must-have capability for modern networks.

4. Strong Passwords And Least-Privileged Access
Stating password best practices remains highly relevant given ongoing reliance on credentials for initial access. While multifactor authentication provides another layer of defense, the least privileged, and complex passwords form the basis for hardening authentication. Networks should mandate lengthy 20+ character machine-generated passwords or easier to recall passphrases. Equally important is limiting user and service account access to only necessary resources and permissions essential for their role. Minimizing privileges restricts exposure space if credentials get compromised during an attack. This frustrated one simulated red team unable to pivot beyond the initial system since permissions were tuned properly.

5. Encryption And Authentication
Rounding out the top five, I advocate aggressively expanding the deployment of encryption and certificate-based authentication mechanisms. Encrypting subnets carrying sensitive information raises the difficulty for attackers sniffing traffic or extracting data in motion. Requiring TLS for critical services like DNS, LDAP, and DHCP removes trivial data capture options. Pushing certificate-based mutual authentication down to the system and user access level forces attackers to steal keys rather than just exploit passwords alone. While encryption does potentially impact performance, hardware acceleration makes it cost-effective enough to warrant broader adoption.

6. Firewall Rules And Policies
Given most threats still exploit perimeter networks, properly configured firewalls remain essential. Edge firewall rules should aggressively restrict access to ports/protocols unless explicitly required for business needs.ENABLED Deep packet inspection facilitates identifying and blocking scans, vulnerability exploitation, and common web application attacks. However, interior firewall changes prove equally important to limit post-compromise lateral movement. Microsegmentation policies that selectively isolate traffic between security zones based on application infosec models frustrate adversary efforts to broaden a breach internally after gaining an initial foothold. Overall, operations teams that revisit rules and policies through regular test cycles fare better in preventing and containing threats.

7. Antivirus Software And Updates
Though prevention remains ideal, signature-based malware detection with antivirus stays relevant in part due to continued reliance upon file-based attacks. When coupled with application whitelisting, antivirus acts as a secondary guardrail stopping nearly all known threats dead in their tracks. However, some advanced malware now operates solely in memory without local file artifacts. Still, keeping antivirus updates reduces the overall attack surface area.

8. Backup And Recovery
Despite extensive efforts, data breaches still occur even in sophisticated networks. To counteract this, implement secure remote backups with the ability to efficiently restore configurations and data at alternate sites. Orchestrating cyber incident recovery exercises helps validate operational readiness. Response teams should strive for quarterly crisis drills including scenarios focused on DHCP, DNS, and IP address management restoration. Having effective contingency plans that facilitate quickly reactivating core networking services minimizes business disruption impacts from even the most advanced attacks. This aspect of defense readiness reduces dwell time which correlates to cost, investigation difficulty, and reputation damage.
9. Monitoring And Auditing
Expanding visibility through enhanced platform and traffic logging further improves prevention as well as faster incident response. Forward logs from endpoints, network devices, and services into a centralized cloud SIEM for retention and analysis. Properly configured, this enables suspending suspicious activities as they occur rather than after the fact. Equally important, intelligence-enriched monitoring better uncover anomalous patterns indicative of advanced malware. Auditing focuses on high-value components like privileged credential usage, sensitive data access, and unauthorized configuration changes. Rapid analysis speed here directly reduces dwell time and breach impacts.

10. Education And Awareness
Given the prevalence of social engineering, an aware workforce marks a critical last line of defense. Providing regular simulated phishing campaigns facilitates measurable improvement. Quarterly education should cover the latest threat trends and cyber best practices – for example secure password guidance or detecting suspicious emails. Furthermore, create self-service cybersecurity resources covering protection areas aligned to business risk priorities and controls.