Firstly, I will start with what is Database Security? , It refers to collection of data and protection of data from unwanted threats. There are so many methods or tools are used to protect the data. We have some aspects of Database Security. There are three main aspects i.e. Secrecy, Integrity, Availability.
1. Secrecy
It protects the database from those users who may be at some time illegally uses the data and it ensures that the user is allowed or not to do such things which he or she wants to do. For ex. Employees are not allowed to see the salaries of other employees as well as other managers.
2. Integrity
In Integrity those who are legally allowed to use the data, it ensures that whatever they are doing with the database it is correct or not. An employee should be capable while modifying his or her own information regarding the data.
3. Availability
There is, users should be able to access data for legal purpose if it is necessary. Payment will be given to the employees according to time as decided or mentioned in the tax policies.
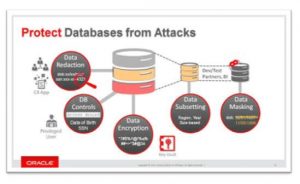
Now, let’s discuss other aspects of Database Security:
4. Monitoring and Auditing of Database
It is the important part of database for the solutions. This is because monitoring and auditing of data leads to address the correct or genuine problem faced by company and it is must to notice that causes, otherwise ignorance of such problem is not good for company.
5. DAM i.e. Database Activity Monitoring
This is the major part of Database Security as it identifies all the activities in database. It creating reports or sometimes gives necessary alerts related to such activities. By using Database Activity Monitoring we will be able to recognise that who is responsible for such accessing of database or why.
Every database protection must include tools or technologies which helps us to detect the cause. These alerts also helps us to manage the issues in real-time. Monitoring of Database is required at every level as we need to keep on check on daily basis.

6. Access control and Separation of tasks.
From access control, it prevents us from mischievous attacks in the organization. By separating works or assigning duties according to the users need we can limit the damage causing in the organization. Separation of task is really very important as it plays such a useful character in the organization as it leads to minimum wastage of time. Every database protection must include function like this.
7. Masking of Data
Administrator of database may need to use particular information or details in certain ways within the database, but they are not able to see it. For other testing or such purposes which are necessary to happen for the development of the organization there is implementing of masking for system upgrades – generally testers and developers.
Data Masking regarding to Dynamic purpose allows users to see the data storage format on the database, without reading or knowing the real data.
8. Encryption of Data
In data encryption we have different levels of encryption for different levels of the database. This will protect the data from theft.