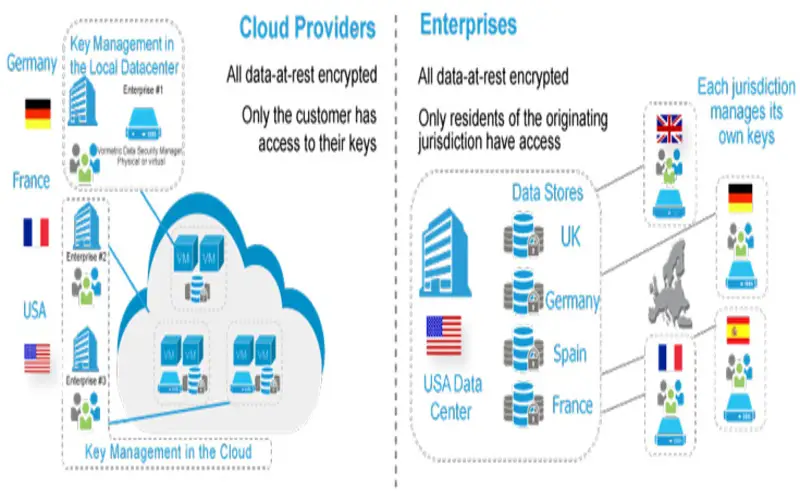
What Is Digital Sovereignty?
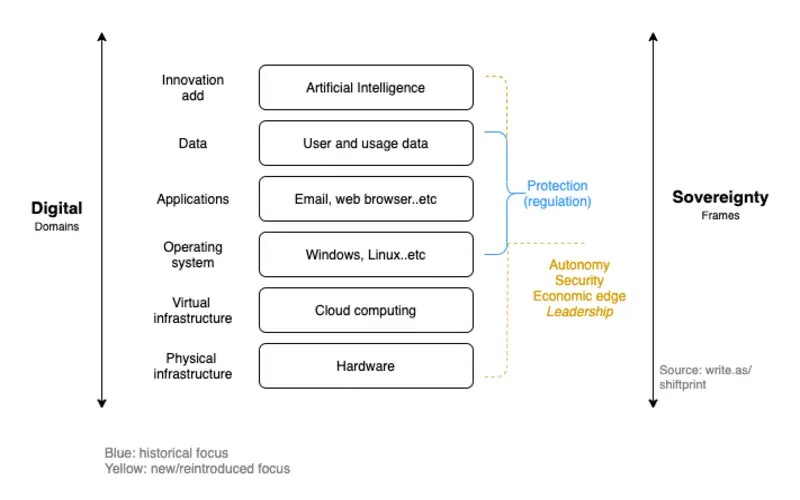
Digital Sovereignty expresses a party’s right and capabilities to control its digital data. It involves control over a company’s digital surroundings, user and employee data, software, hardware, and digital property.
Importance Of Digital Sovereignty?
Organisations are evaluated on their ability to innovate, go-to-market quickly with new solutions, deliver a better user experience, and embrace digital transformation. They are operating, in the cloud is the way forward. Hence, there is an upward fashion of more public sections shifting IT workloads to the cloud. Attending this fashion is concerned about data security and resume optimisation.
Benefits Of Data Protection Rules
It is recognized that the trust of companies throughout the globe in protocol solutions has never been higher. For instance, pre-COVID data shows that Office365 and G-Suite assumptions were at an all-time high. After the epidemic broke, many SMEs had no choice but to acquire video meeting tools such as Zoom, Google Meet, etc. Many of these platforms were unfit for the traffic stream leading to various data violation and issues. It has unresolved consumer data privacy, and many businesses violations GDPR and other data security laws.
1. Better Services And User Support
Digital sovereignty also enables SMEs to offer better services and user support. When SMEs have authority over their digital structure, they can customize their services to meet the particular needs of their users. They can also provide more personalized service and support.
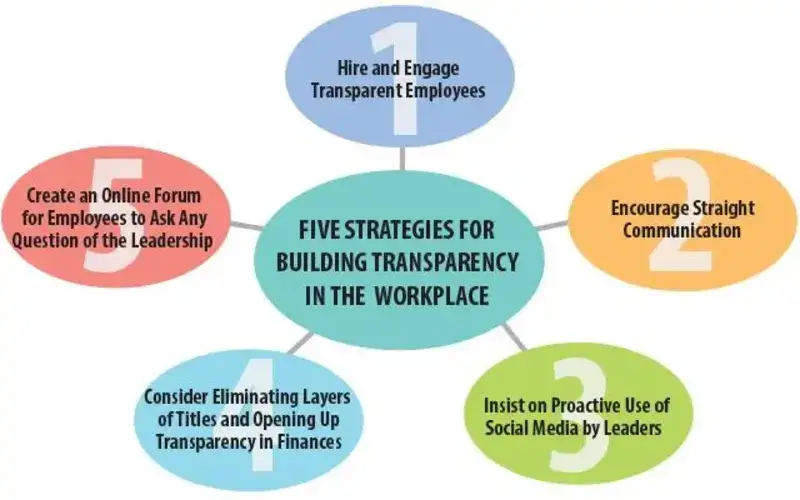
2. Construct Trust And Transparency
SMEs with digital sovereignty can also construct trust and transparency with their users and staff. For instance, users are more likely to trust a company that is transparent about its data-catching method and has control over its digital structure.
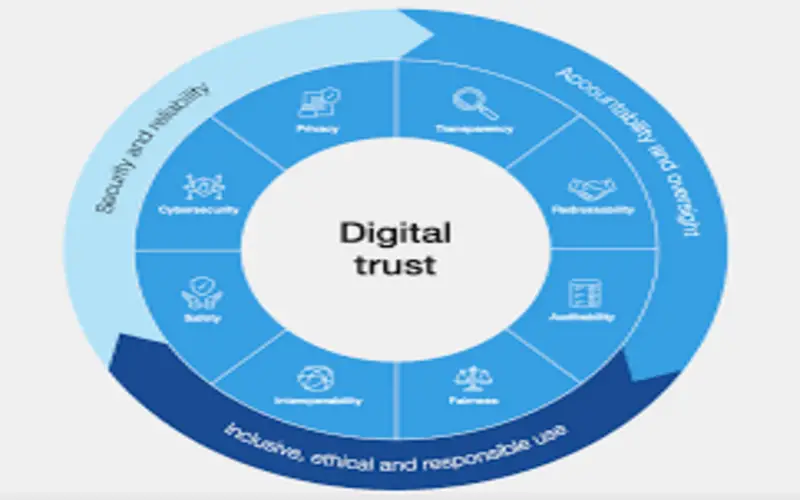
3. Minimize Shadow It And Facilitate New Ways Of Working
Digital sovereignty can help to reduce Shadow IT, which is the use of innovation (software, cloud services, and gadgets) within a corporation that has not been permitted by its IT department. When SMEs control their digital structure, they can more easily offer employees the tools and applications to work efficiently. They can also better collect and observe employee activity to ensure that delicate data is not approached or shared without authorization.

4. Control And Regulate Data
Being a digital sovereign means managing your data. You have command over the data you gather, where you store it, and how you collect it. It is favorable for companies because you can retain better tabs on your data, you’re never locked out of acquiring it, and you can see when it’s entirely deleted from the system. You will remove what information your business keeps in the dataset. Not only will this assist you in better structuring and managing your survival data, but it will also assist you in remaining on top of compliance with data security rules.
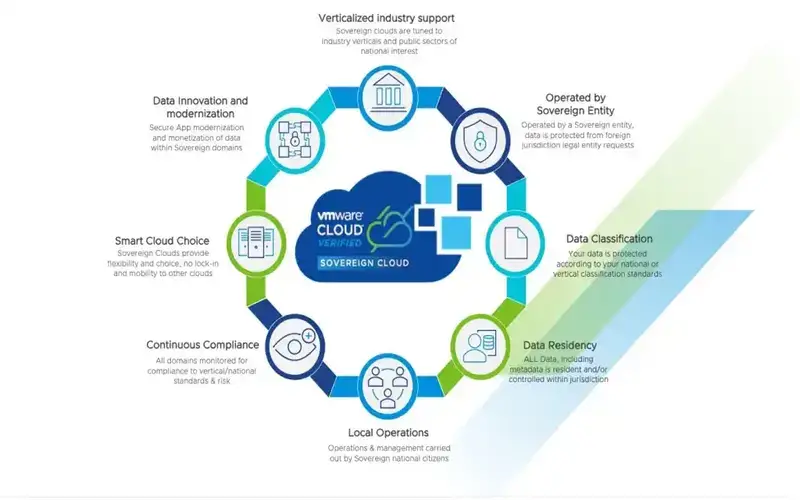
5. Guarantee Compliance With Data Security Rules
Risk is assured when controlling and managing your data. Since you are the controlling command on user information, it’s down to you to ensure you effectively secure that data.If the companies don’t follow the rules, they have to face risks like penalties, fines, and losing trust with users. When data is accommodated externally, it’s resistant to detecting immoral activity, poor data security procedures, outdated storage systems, etc. Using a local server or cloud provider makes it simpler to ensure local data security rules.

6. Construct Certainty And Transparency With Workers And Clients
The general public is well aware of the growing influence of a few tech companies, as well as the risks associated with data security and undefined hosting operations. It has directly reduced trust in well-known and constructing tech providers and more belief in local ones. In business, for example, 56% of respondents said they don’t believe GAFAM and are concerned about data security. The remaining 44% is approval of local owners. Mentioning sovereign solutions may assist companies in building trust with both workers and clients.
7. Improved Services And User Support
Software execution tech owners offer a vast range of services through solutions professionals, technicians, and support agents to assist throughout the numerous stages of a given project. Accessibility and rapid response times are critical for offering optimal services and ensuring user satisfaction. It also includes post-project posture, such as sending a thank you email. Depending on a sovereign tech offered can help companies gain valuable time when employing solutions as the professionals that might require can be available on the website and in record time, thus limiting the requirement for remote operations and endless back and forth by emails.
8. Limit Shadow It And Allow New Ways Of Working
The impact of large technology suppliers on businesses that do not rely on shadow IT. Shadow IT presents the use of devices, applications, and platforms with the permission and knowledge of the IT department. If the workers don’t find any value in the solutions they have in location, then they will watch to use their own to get things done. Harmful in all stages: security, data privacy, costs, etc. The key is not essentially in the solutions themselves but around the entire method vision of business and government alike. Improving local solutions and IT infrastructure is critical to limiting workers’ trust in alternative and foreign tech owners.
9. Data Residency And Compliance
With Emma’s numerous cloud management platforms, organizations can refer to rules to ensure the data stays within particular geographical regions. Its localized cloud structure supports these data residency needs, benefitting compliance with local data security rules and improving data sovereignty.