Dynamic Host Configuration Protocol (DHCP) seamlessly facilitates the allocation of IP addresses across enterprise local area networks, vastly reducing the need for tedious manual configurations while circumventing the possibility of disruptive address conflicts. Alongside the benefit of centralized control, DHCP offers system administrators an extensive range of customization options around scopes, exclusions, lease durations, and reservations to meet specific business goals. However, DHCP malfunctions or suboptimal configurations carry the risk of severe network connectivity issues and even security breaches if unauthorized devices can grab addresses.
Meticulous planning, monitoring, and optimization remain essential for companies to truly unlock the immense potential of DHCP services while avoiding nasty surprises. As an integral network service touching all connected endpoints organization-wide, any neglect or deficiency in the DHCP architecture leaves enterprises exposed from both employee productivity and customer experience perspectives. Based on many years of first-hand troubleshooting experience across exceptionally intricate and multipronged global corporate networking infrastructures, I outline 10 vital best practices for promoting seamless DHCP configurations that reliably offer dynamic yet conflict-free IP addressing capabilities spanning locations and subnets.
Both senior infrastructure leadership and Level 3 severity engineers should proactively gather detailed DHCP performance telemetry and capacity forecasts as part of their regular operational reporting cadences back to executive technology oversight committees.
1. Use A Dedicated And High-Availability DHCP Server
Strategically allocate all DHCP serving capabilities onto dedicated, high-availability server instances separate from other critical networking hardware like switches, routers, or next-generation network firewalls. As the overall count of connected client assets and BYOD devices scales rapidly upwards within the modern digitally-transformed enterprise, overloaded network hardware like basic routers or cable modems will fail disastrously to handle the extensive DHCP processing requirements and ever-growing address pool properly under peak loads.

2. Carefully Validate DHCP Scopes Align To Business Requirements
The DHCP scope outlines the applicable pool of IP addresses available for allocation within a given subnet including all the key lease parameters like lease intervals that directly impact client renewals. Improper or incompatible scope configurations relative to the greater network frequently spark frustratingly cryptic client-side connectivity errors so administrators must validate DHCP settings match intended usage requirements and traffic profiles. Define DHCP scope ranges thoughtfully based on estimates of expected peak utilization rates derived from historical patterns, benchmarks, or simulations rather than rules-of-thumb.
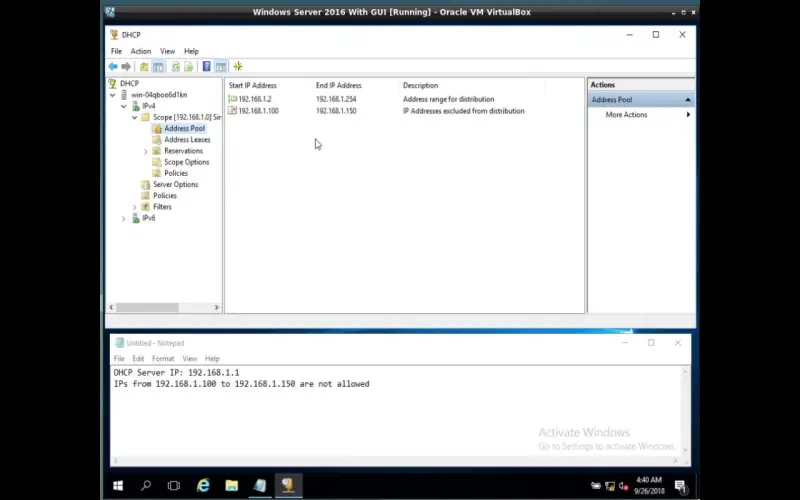
3. Allocate Exclusion Ranges To Protect Static Assignments
Proactively designate protected IP address exclusions encompassing the full range of specialized hardware, servers, and clustered applications that require fixed static assignments outside the DHCP-managed scopes. Common examples include critical network printers, managed Power-over-Ethernet switches, VPN gateways, Wi-Fi controllers, the DHCP servers themselves, and certain clustered server applications that rely on precise static IP addressing for communications. While permanently fixed IP assignments skip the risk of random address changes leading to conflicts, defining exclusions keeps the primary DHCP scope intact as a single continuous range rather than necessitating multiple smaller disjoint scopes.
4. Employ Multiple Scopes For Simple Administration
For exceptionally expansive enterprise networks with thousands of client assets dispersed across countless geographic zones, leverage multiple logical DHCP scopes for simpler administrative partitioning example by department, building, or floor. But strictly validate the scopes have no overlapping or duplicated address assignments. Define descriptive scope names and tags facilitating policy assignments as devices inevitably roam across different physical network segments. Multiple scopes also constraint troubleshooting blast radii when connectivity issues or cyberattacks arise. Some advanced network hardware expects your scope naming conventions to match device profiles for automated network-wide configuration so check interoperability thoroughly before rollout.

5. Minimize Static Assignments To Reduce Administration
Actively minimize the default tendency to statically assign fixed IP addresses manually despite the perceived benefits of greater control since the overhead of managing static IP inventories grows exponentially as networks scale up. Thoroughly investigate and challenge any justified business needs for static IPs through in-depth root cause analysis discussions with both infrastructure teams and application owners. Explore shifting towards leveraging DHCP reservations capabilities which assign addresses to specific whitelisted hostnames or MAC addresses as a more dynamic alternative.

6. Automate DNS Synchronization Via Dynamic Updates
Promptly enable DHCP servers to dynamically inject their IP addressing changes including registrations, renewals, and de-provisions for connected clients directly into upstream DNS zones which accordingly update and synchronize changes in real-time automatically. Manual periodic synchronization of DNS records tends to gradually desynchronize and fracture across client devices continuously joining or departing the network over time. Secure dynamic DNS updates prescriptively configured align DNS to reality more accurately while allowing smooth DHCP recoveries after any server outages without entanglement risks of disconnected IP and DNS data.
7. Allocate Reservations To Designate Approved Static Clients
In those exceptional scenarios where URL team business partners demand fixed IP assignments to select specialty assets remain utterly mandatory due to arcane application constraints, leverage DHCP-based reservations which assign desired addresses uniquely to only those specific preapproved hostnames or MAC addresses rather than broadly opening exclusions which are vulnerable to exploitation.
8. Choose Lease Durations That Balance Performance And Security
Since the DHCP lease interval which dictates when connected clients must renew their granted addresses has major implications on perceived network reliability as well as cyberattack containment strategies, selecting lease duration parameters warrants thoughtful evaluation of performance and security tradeoffs. Excessively short lease intervals below one hour needlessly overload clients and servers alike with constant renewal chatter and processing overhead which hampers productivity.

9. Enable Oversight Protections Via Conflict Detection
Address conflicts occur when the DHCP infrastructure inadvertently assigns an identical IP address already actively leased out to another current client, typically following a cascade of faulty or missed renewals. Turning on conflict detection triggers the DHCP server to explicitly ping any tentative new IP grant before the final assignment to doublecheck the absence of existing occupants, then deliberately issue different addresses upon collisions. While not completely foolproof in every intricate scenario, active detection controls significantly reduce the risks of overlap errors which often fly under the radar yet still completely break connectivity for two or more hosts simultaneously causing severe yet challenging troubleshooting complexity.
10. Monitor Performance And Utilization Trends Closely
Actively track and graph essential DHCP health metrics across all server instances over time to spot emerging problems proactively while also right-sizing capacity including critical indicators like current scope consumption percentages, typical expiration rates, abandoned leases, and fault volumes like conflicts or bad requests. Historical monitoring readily reveals cyclical utilization and renewal patterns aligned to business calendars while sudden unusual spikes in conflicts or precipitous declines in lease renewal rates loudly indicate brewing server resource constraints or software issues warranting urgent intervention.



















