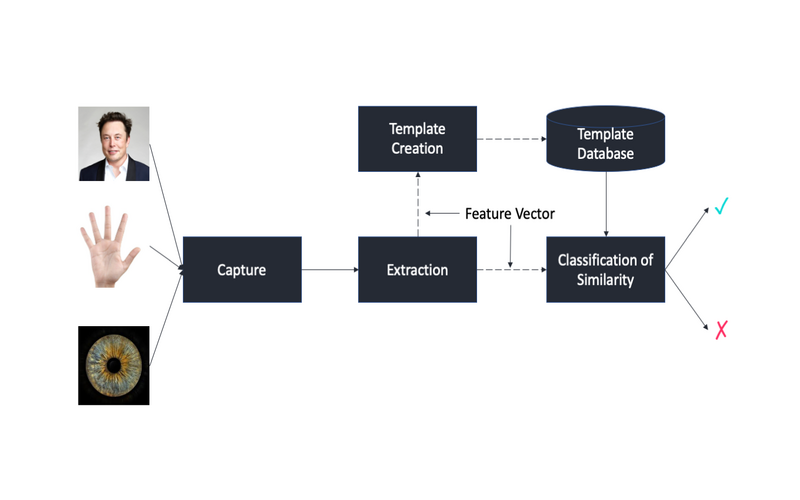
What Are Biometrics?
Biometrics are physiological or natural human characteristics that can be used to visually identify a person and grant access to systems, tools, or data.
For instance, these recognize are fingerprints, facial patterns, voice or typing measures. Each of these recognitions serves as a rare mediator for the individual, and they may be pre-owned in mergers to ensure greater recognition accuracy.
The latest access handle is based on three types of factors—something you have, something you know. Something you might involve an authorized card or key. Something you know would be a password or PIN.
How Reliable Is Biometric Authentication?
Authentication qualifications, such as scans of fingers or recordings of speech, may escape from tools, business servers, or the software used to compare them. There is also a massive potential for positive and false negatives. The Facial recognition technology may not recognise a consumer wearing makeup, or glasses, or who is unwell or weary. Voices also deviate.
People make distinct sounds when they first wake up, when they attempt to use their phones in a crowded public space, or when they are furious or frustrated.
Two Types Of Biometrics
Physical Measurements
They can be either morphological or biological.
- For biological evaluations, DNA, blood, saliva, or urine may be pre-owned by medical groups and police forensics.
- Morphological characteristics include fingerprints, hand shape, finger vein design, eye (iris and retina), and facial shape.
Nature Measurements
The general is:
- Voice recognition.
- Signature dynamics (speed of movement of pen, accelerations, pressure deploy, inclination)
- Keystroke dynamics.
- The way we use objects.
- Gait, the sound of steps.
- Gestures, etc.
The methods used are subject to continuing research and development and are constantly improved. To see how nature biometrics has acquired momentum in banking, visit our web designer. Anyhow, the distinct sorts of measurements do not all have a similar stage of flexibility. Physical measurements generally provide the benefit of remaining more secure throughout an individual’s life.
1. Biometrics And Recognize Access Management
Optimal IDM, a leader in institutional solutions for access management, places a high value on multi-factor authorizations, which may include biometrics. The most effective identity access management strategies for businesses, as well as the role of biometrics innovation in data protection.
2. Future Strategy For Payment
Biometrics are likely to eventually be the future of payments. It has already been seen in nations such as China, and the use of a biometric face identification system to create payments anywhere is in the experimental stage. This innovation will remove the requirement to carry any form of payment like cash, card, or smartphone. Just look at the software, enter the amount and the costs will be completed.

3. The Rapid Maximizes In Mobile Authentication
About 27% of smartphone consumers were using biometrics as authentication. Recently, it has jumped to 41% of consumers. Additionally, it is predicted to approach 66% by 2024.

4. One Of The More Extensive Biometric Data
India, through its Aadhaar (identify proof) has collected one of the more extensive biometric data around 125 crore people. The Aadhar card is essential for the people of India and it registers biometrics to monitor one’s individuality perfectly.
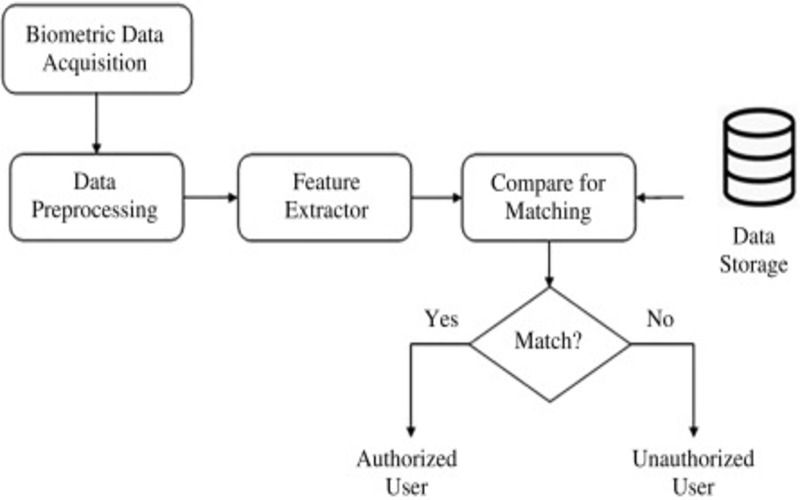
5. Not Limited To Fingerprint Or Face ID
Biometric recognition systems are not just based on fingerprints or face recognition. These systems can duties on many types of biometric identification ways like – vein identification, voice recognition, finger geometry, DNA related, and many more.

6. Biometrics – Not As New As You Would Think
The initial trading hand geometry identification system became accessible way back in 1974. This system was deployed for three main intentions – physiological access control, time and attending tracking, and personal recognition.
7. The First Smartphones With A Fingerprint Scanner
It is a minor known fact that the initial business to meet fingerprint scanners was not Apple or Samsung. It was Toshiba. Yes, Toshiba met this characteristic initially in 2007, which was chased by HTC.

8. Biometrics: Beyond Passwords And PINs
Biometrics are authorities processes that employ an individual’s physical and natural features such as face, fingerprint, voice, or other traits to recognize them and identify them precisely. In a world subjected to passwords and PINs, biometrics provide a stimulating alternative. Unlike standard authorized strategies that depend on something you know (passwords) or something you have (security tokens), biometrics authority what are – an individual with different physical or natural traits.

9. Tough Recognize Verification
Biometrics also play a crucial role in automatically confirming that a person is who they insist on being. This procedure occurs once, generally during the initial registration stage, and is critical for setting up future verification measures. Given the diversity of biometric traits, there’s an essentially greater assurance of correct confirmation. The flexibility of biometrics transfers recognizes confirmation into a citadel, laying the groundwork for unparalleled future authority quantity.
10. Improved Authentication
Biometrics take cyber security authority to an entire latest stage. Because biometric recognition is so rare – no two fingerprints or voice designs are the same – the likelihood of unauthorised entry is greatly reduced.

11. Healthcare And Subsidies
Other applications, primarily national recognition cards, are used in European and Middle Eastern countries, as well as Africa, for identification and health-care programmes, such as Gabon. With these biometrics I.D. cards, fingerprints verify the bearers recognize early available governmental services or healthcare. For example, even before the programme began, it was evident to everyone that command needed to execute all resources to prevent the health coverage programme from becoming a centre of interest for people in adjacent nations. This characteristic was crucial to ensure that the program’s kindness would not mislead the use of rights. Hence, a successor is separately recognized so that access to concern can be reserved for them. The access decided that the assured parties’ recognition would be nominative in executing an independent health insurance number.