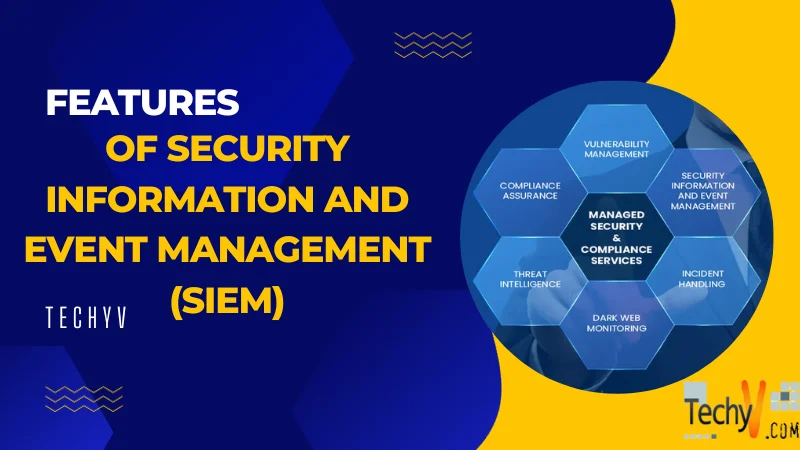
What Is A Security Information And Event Management System?
SIEM stands for Security Information and Event Management System. It is a device that gathers data from multiple endpoints/network devices across the network, restores them in a centralized place, and operates associations on them. This room will seal the primary concepts needed to understand SIEM and its workings.
How Does SIEM Work?
At the primary stages, all SIEM solutions operate some stages of data accumulation and sorting features to recognize vulnerabilities and adhere to data assent needs. While some solutions vary in ability, most provide the same core functionalities.
Importance Of SIEM
We know about the multiple types of logs. It’s time to appreciate the importance of SIEM. As all these tools create hundreds of events per second, analyzing the logs on each tool one by one in case of any occurrence can be a tiresome task. That is one of the benefits of having a SIEM solution in location. It not only takes logs from multiple sources in actual time but also offers the capabilities to relate between events, find through the logs, examine incidents, and respond immediately.
- Actual-time log Ingestion
- Alerting against abnormal actions.
- 24/7 observing and visibility.
- Secure against the new vulnerabilities through early observation.
- Data insights and imagination.
- Ability to research past incidents.
How To Implement A SIEM Solution
Management of all sizes uses SIEM solutions to reduce cybersecurity risks and meet executive compliance—the best practices for implementing an SIEM system.
- Define the needs for SIEM employment.
- Do a test run.
- Collect sufficient data.
- Have an event response plan.
- Have an event response plan.
- Keep enhancing your SIEM.
1. Automated Tracking Of Lateral Movement
By examining past events and the MITRE ATT and CK structures, we know that over 80% of assaults include lateral movement. It is where assault attempts to avoid observation or acquire access to higher liberty by changing credentials, continuous liberty, and then operating too high-value IP addresses and benefits. To efficiently follow such relevant incidents from distinct log sources together.
2. Incidents Relation Observes
Incident relation is an accessory part of the SIEM solution. Employing advanced evaluations to recognize and understand complex data patterns and incident relations offers insights to place and reduce potential vulnerabilities to business security rapidly. SIEM solutions outstandingly enhance the meantime to observe (MTTD) and meantime to respond (MTTP) for IT protection teams by unloading the manual workflows combined with the in-depth observation of protection incidents.
3. Incident Observing And Security Alerts
SIEM incorporates its evaluations into a single, centralised dashboard from which security personnel may monitor activity, group alarms, identify vulnerabilities, and respond or improve. Most SIEM dashboards also involve actual-time data observations that help protection evaluate spot spikes or currents in suspicious action. Using personalised, established relation rules, directors can be informed at the same time and take appropriate actions to eliminate vulnerabilities before they become more serious security problems.
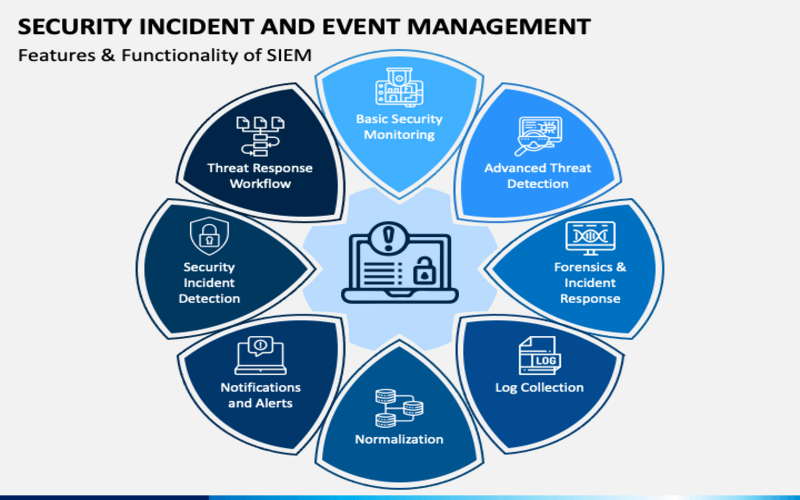
4. Gather And Manage Data From Available Sources
Current-day vulnerabilities usually span various data sources. To be efficient, every data source must be accessible to advanced SIEM to evaluate and relate the data. It involves cloud service data, regarding log data (security controls like recognize, databases, and application logs), and network data (interruption protection, endpoint, flows, packets, etc.)
5. Predictable Costly For Log Ingestion
Log retention settings are critical as they allow for evaluating spending by impulsively minimizing unnecessary logs. By explaining a particular period to retain identical logs by type and source, managing can free up restored capacity, ensuring forecasting spending. Certainly, logs are cleared, avoiding the collection of excessive data and combined storage costs.
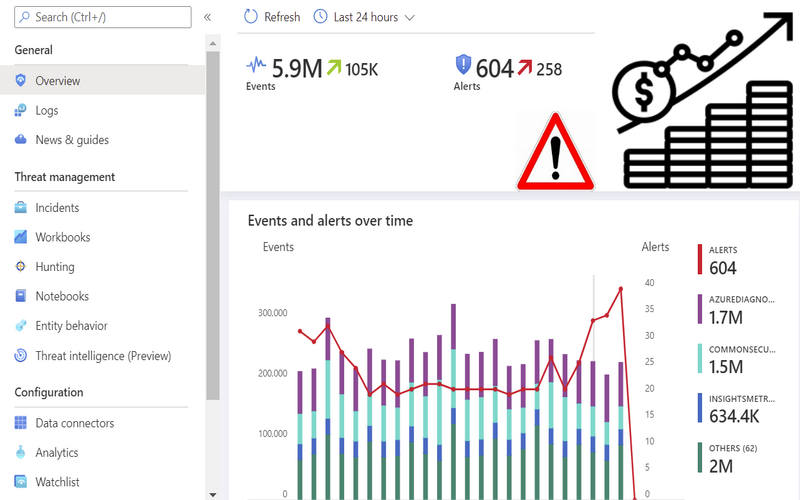
6. Altering
Evaluating incidents and helping increase alerts to verify security staff of simultaneous errors, either by email, other types of messaging, or between security dashboards.
7. Compliance
Automates the collection of compliance data and the production of reports that conform to established security, governance, and inspection processes such as HIPAA, PCI/DSS, HITECH, SOX, and GDPR.

8. Retention
Stores long-term factual data to allow evaluation, tracking, and reporting for compliance needs. This is especially essential in forensic examinations, which can happen long after the fact.
9. Event Response
Offers case organization, collaboration, and knowledge sharing around protection incidents, enabling protection teams to rapidly accompany the critical data, communicate, and respond to a vulnerability.
10. Well-vetted, Significant Data Architecture
Many heritage SIEMs were structured in the 2000s and use exclusive innovation. There is an essential technological distinct between then and now. Platforms such as Hadoop, Mongo, Elasticsearch, Big Query, and Flame are not easily accessible. With the burst of security data accessible and being gathered, what’s now needed is a vast data structure that can scale data, revolve within it, and take benefits data science algorithms for quick queries and observation.
11. Enrichment Of Consumer And Assets Context
The big-level enhancement that submits helpful results from all the data you are gathering. Moderns in data science offer many perceptions that earlier had to be related by experienced evaluates, such as:
- Free vulnerabilities intelligence integration and relation
- Dynamic peer collecting.
- Merging IP addresses with consumer expertise, devices, and timelines.
- Tracking advantage ownership.
- Combining consumer and machine types with action.
- Recognizing service accounts.
- Relation personal email addresses with employees.
- Combining embalming station log action with consumer accounts and timelines.