As IT professionals administering networks and services for users, protecting critical infrastructure from disruption should drive us. DHCP servers that supply IP addresses enable users to connect their devices and utilize network resources. However, with widespread reliance on DHCP, servers face increasing threats of exploitation through malicious scans, traffic floods, spoofing attempts, and attacks disrupting service availability.
As the first line of defense, dialing in robust firewall policies ranks among our top responsibilities in safeguarding users’ ability to connect, while upholding integrity and resilience of services we maintain. Rightfully, those counting on the availability of your DHCP infrastructure expect their access and usability shielded through IT controls warranted in an environment facing regular threats. Outlined across sections below, I detail key schemes and measures available through firewalls to guard your DHCP servers.
Configuring these top 10 rules helps restrict vectors malware uses, spoofing we hope to prevent, and attacks attempted at scale which insidiously try bypassing perimeter checks otherwise in place.
1. Block Traffic By Default
As the name suggests, this configuration works by blocking all ingress connections on all ports and protocols by default – a crucial stance establishing the perimeter’s initial integrity. When tuning firewall settings, instead of reactively plugging gaps post-intrusion, work from the premise to permit only known, trusted sources, and specific scenarios of access. Doing so inherently limits what an external entity may meander through trying to circumvent existing rules or exploit overlooked vulnerabilities. Through permissions review cycles, refreshing explicitly declared connection paths to your DHCP server warrants part of regular reporting. As with any specialized server running unique services, risks compound on publicly exposed access.

2. Follow The Principle Of Least Privilege
As with user groups in general, access permissions for servers must strictly follow the principle of least privilege — permit only what is essential for its functioning. Expansive permissions may ease operations needs but invariably increase surface vulnerabilities by orders of magnitude. For DHCP servers, at minimum TCP and UDP traffic to ports 67 and 68 need allowance — resulting in lease assignments and renewals rides on them. However broad rules though convenient operationally, exponentially raise risks from malformed packets and vulnerability exploits.

3. Specify Source IP Addresses
Instead of general permissions, identity-based access limits ingress vectors significantly raising resilience. Define firewall rules restricting source IP ranges – narrow it to client subnets from which DHCP leasing is supported, specific switches or load balancers interfacing those segments. Ranges encompassing internet-wide scans certainly do not warrant access in any form lacking legitimate need. Spoofing attempts often ride on masking source IPs or pose as non-privileged resources hoping to bypass coarse filters.
4. Designate Specific Destination Ports
Use firewalls to limit destination ports on the DHCP server only to those essential for its functioning – 67 and 68, over TCP and UDP. Vulnerability scans often traverse default administrator ports like 22 for SSH or 3389 for remote desktops hoping flaws exist – removing those paths amounts to prudent posturing. Any legacy port no longer operationally warranted must be weeded out through reviews improving resilience against common exploits on those numbered endpoints. Tools like NMAP reveal open ports during scans – learn from those surface reports to consistently minimize the discoverable avenues available for access attempts.
5. Open The Firewall Ports That Users Expect
An extension of the previous point above, for user-facing systems firewall configurations should align with access conventions users rightfully expect by default for that service scenario. Much friction arises when firewall changes disrupt ingress paths they previously, intuitively could access. So carefully consider operational usage pre and post-changes – for DHCP, confirm TCP/UDP ports for lease requests and renewals remain open without throttling from internal subnets users reside in. Similarly, remote access methods IT staff may utilize to administer those servers should continue unhindered as policies tighten – reminders help avoid locked-out admin accounts.
6. Implement Rate Limiting
To protect against an excess of connections overloading server resources, use firewall rate-limiting features. Limits placed on DHCP work most effectively for external sources but may apply to internal clients as well. Define thresholds crossing which the firewall flags, drops, or alerts on suspicious traffic volumes – for example, lease requests exceeding 50 per second or 300 new MAC addresses noticed over 5 minutes could indicate scans or denial of service attempts. Support teams can start with conservative thresholds that capture anomalies while allowing flexibility for genuine usage peaks say during events with guests onboarding devices.
7. Use Port Security
Employ port security features on adjacent firewall interfaces or switches to limit MAC addresses able to use that physical port -Doing so protects from basic spoofing attempts using DHCP where an unauthorized system attempts to steal connectivity by mimicking a permissible MAC identity. Locking switch ports by MAC filters out bogus devices lacking the context of permitted systems expected on those switch interfaces through which DHCP connectivity extends. Interface data synced from firewall to switch secures DHCP connectivity path continuity – though MAC spoofing persists through virtual interfaces, locking switch ports to firewall hints adds one layer of stalling spoof attempts triggering alerts on topology anomalies between connected access systems.

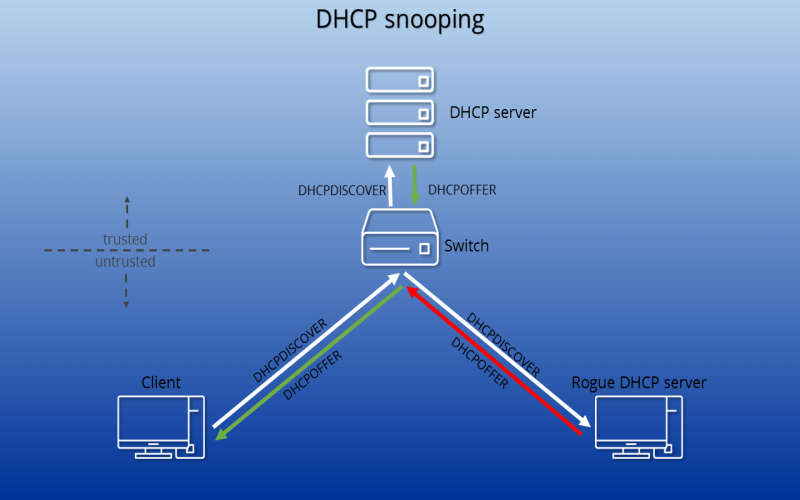
8. Use DHCP Snooping
Activating DHCP snooping uses firewall administration privileges controlling traffic flows to switch interfaces otherwise operating autonomously forwarding content using L2 addresses alone. DHCP snooping comprises a set of switch port validations introduced through firewall rules preventing basic spoofing attacks – for example, spoofing of DHCP responses from unauthorized locations are blocked using verifications against expected server source IP port tuple checks. REQUEST messages with mismatching MAC and IP pairings also stand filtered by DHCP snooping – blocking a common DoS attempt aimed at exhausting address leases through spoofed requests.
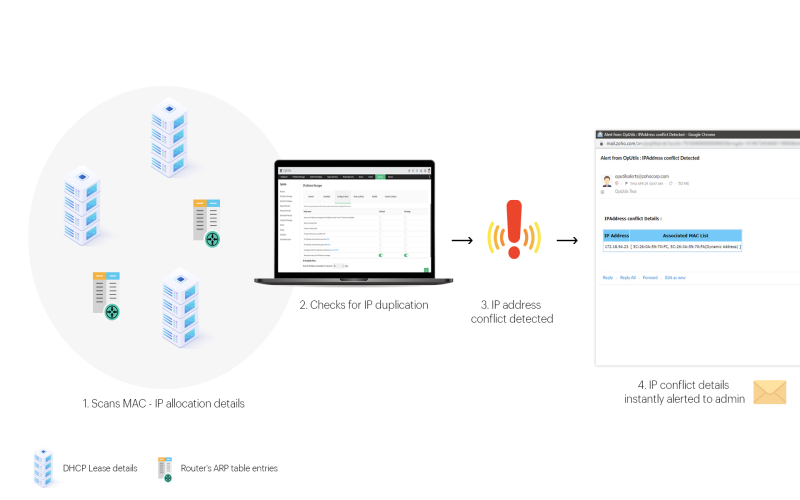
9. Use IP Conflict Detection
IP conflicts occur when the same address gets assigned inadvertently to multiple clients resulting in disruption for legitimate users allocated previously. Spoofing triggers such conflicts through forged DHCP requests extracting addresses already active leading to service faults. DHCP server-initiated conflict resolution revokes the lease from the unauthorized user with packet forwarding disabled for the impersonating device. Additionally, firewall monitoring the connected switch interface similarly identifies traffic sourcing anomalies when media access vis a vis IP address mismatches likely suggest spoofing attempts in progress.
10. Backup Your DHCP Server Configuration
An often overlooked yet easy-to-implement safeguard lies in maintaining periodic backups of the DHCP server configuration of the production server. This guards against malicious tampering or ransomware targeting business-critical infrastructure. Separated backups allow quick restoration streamlining availability through intact configurations and minimizing DHCP service downtime due to server outages. Additionally once compromised, backups prevent tainted systems from spreading across DHCP infrastructure restoring bespoke server baselines promptly.