Can you recollect when was the first time you got your hands on a computer- try delving into the lanes of your memory?
If you are born in the last decade of the millennial years, possibly in the 3rd or 4th standard, isn’t it? But were you taught how you should use the computer: No I’m talking about your primary lessons like “Switch on the CPU, Switch on the Monitor…..”


Do you know there exists a set of rules that have to be kept in mind and mandatorily followed while using computers? Such rules and regulations are called ‘Computer Ethics.’
Computer Ethics essentially impose the principled enforcement and application of computer-based resources. It prescribes the methods and layout of actions to be taken to prevent unauthorized distribution of intellectual property and avert infringement of copyrighted products, trademarks, and plagiarism of digital content which may be in a soft copy or on the web. It aims to govern the procedure of consumption of technology without violating the conscientious beliefs of an individual or an organization at large.
In 1992, the Computer Ethics Institute, a Washington DC-based nonprofit organization that focuses on the issues and challenges drawn by the rapid advancement of technology that is happening in leaps and bounds in the recent years, constituted and gifted the globe an abridged code of ethical conduct which is called, ‘ The Ten Commandments of Computer Ethics ‘.
The Ten Commandments of Computer Ethics:
Here are the explanations of the ten commandments of computer ethics in brief:
- A computer should not be used to inflict harm on other people by any means.
- You should prefer minding your own business and not interfere with someone’s computer-based work.
- You should not meddle in someone else’s computer files without their proper consent.
- A computer should not be used to embezzle or steal someone’s assets.
- You should never use a computer to deliver concocted, untrue and fictitious testimony.
- You should completely avoid cloning or using any software which belongs to someone else and proper settlement has been done.
- You should not use other people’s computer resources without permission or proper authorization.
- You should never circulate or distribute someone’s intellectual property without compensating them or letting them know.
- You should always think and be extra careful about the results of the program or system you are creating on a social scale.
- You should always use a computer in methods that may bring positive outcomes and safeguard the interests of your fellow beings.

It is a subject of grave concern that people aren’t well aware of these ethics and at some point, are either involved or have fallen prey to cyber crimes, at an age where young teenagers and adolescents have free accessibility to the World Wide Web. They are the same folks who happen to be both the prime targets and perpetrators.
It is true that the Internet has no restrictions for exploring information because of its vague and imprecise borders, but this should not become a passport of encouragement to trespass and encroach into someone’s privacy with the deliberate intention of harming them in any manner whatsoever and thus breach the basic ethics of computing.

Cyber Awareness Programmes:
The month of October which is associated traditionally with cooling weather, Halloween festival, Autumn Fall and leaves changing color from leafy green to yellowish red, but the United States celebrates it as the National Cyber Security Awareness Month (NCSAM) nationwide, an initiative that aims to raise cyber awareness among the general public. It was originally constituted as collaboration between the Government and the Information Technology Industry to encourage vigilance among all communities of users.
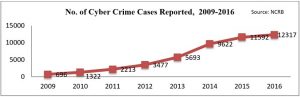
Such an initiative, if launched by Government of India, would be highly appreciated and will have to demand massive acceptance among the citizens, with the nation facing a rapid surge in the cyber-crime rates since 2014.