How is Algorithms Used in the Technology Business?
For problem-solving operations performed by a computer, a set or process of protocols is to be followed in performing the calculations, which is known as Algorithms. To shift between computer programs and mathematical problems, we have simple functions in Algorithms.
Algorithms’ design techniques provide solutions to problems in different fields such as giving your credit card details in an online store for any purchase made in a secured way, other consumer technologies, or dealing with network issues. This is the reason why Google has changed its search to Google Hummingbird.
Here are some of the Algorithms used in Tech business nowadays:
1. Google calculates the results of the search using PageRank.
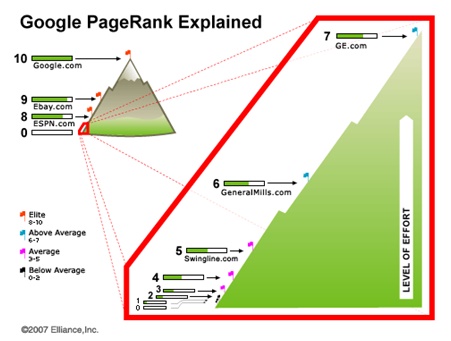
Algorithm used by Google for its search results has always been open to all, but the way the search result is organized by the Algorithm is put as a secret by the company.
The key invention of Internet search used by Google is PageRank. Several competitor industries used the web pages index, which people maintained for many years. The value of the websites is assessed by the company automatically. This has become a massive advantage to the industries that relied on websites. Through this, the web has grown rapidly.
Visiting each and every link from the Internet is the Algorithm strategy of PageRank. Some of the visitors may look at any website and may feel that the content and links of the page are worth sharing. The validity of the page increases if there are links to that page. The visiting rate of the website will grow high if it has many inbound links.
2. To keep the details of credit card secure, public-key cryptography is used.
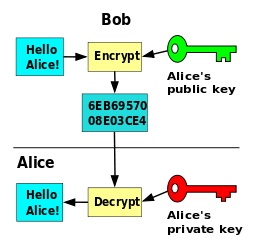
Every online site that includes business transactions, which involve entering of credit card or debit card details must use some set of Algorithm design principles to keep those credentials secured from the intruders. Set of such Algorithm designs is called public-key cryptography that exists in every online site that needs security; it is also termed as magic maths. The functionality of the public-key cryptography is to encode the data into a key and that data cannot be decoded using that certain key.
If someone wants to do any transaction and they don’t want anyone to see the credit card credentials, they need to encrypt it, or otherwise, it will become an open invitation to all intruders to access your account without your knowledge. This algorithm analysis and design are basically done by the web developer while designing that site. You don’t need to worry about it.
3. Protecting the passwords of the users.

We enter passwords on our systems, or may be on other’s systems while accessing our emails, online transactions, etc. But the entered values must be encrypted so that they won’t be misused. This is done through hashing and algorithms. It will take the data and split it out into units.
The input taken and the output given must be the same in a good cryptographic hash function. If the message or data is changed, then the hash is also changed. It is impossible for any two messages to have the same hash; each has its unique key. All of these techniques are used in password protection.