Comprehending Spammers and Email Flow
Avoiding spam or unwanted commercial emails is undoubtedly an increasingly significant matter, but it really gives IT professionals a tough time. A lot of work has been worked on the development of some urbane content filters that could recognize as well as mark messages to settle on their spam echelon. At the same time, these schemes kept on improving with the presentation of tactics like “Bayesian” filtering.
Besides, their effectiveness will always be negotiated by the spammers, with a financial reason that will remain consistent to alter their content to use such filters. There are few senders of unwanted commercial emails who have gone one more step ahead of avoiding content filters.
The reason is that they have started utilizing far and wide accessible software to scrutinize their messages via famous anti-spam packages before they’re forwarded. So, it has become quite easier for them to transform their content to ensure its survival.
Apart from all this, the majority of global businesses and networks have started joint ventures to work in a fast paced environment. As a result, they require swift ways of communication, so that they can easily communicate as well as transport data to their desired destinations. Keeping this intention in vision, different new media giants like Google, Hotmail, Yahoo, Round Cube and other Exchange Servers have well-established high volume electronic mail addresses to facilitate their consumers.
All of us have only been using these mail addresses, but we never thought of ‘when an email is sent from Yahoo, Hotmail or any Exchange Server, how is it directed towards the accurate mailbox?’ This is an interesting question everybody wants to know these days. Well, actually, it follows a secure system that analyzes accuracy of information and then by locating its desired destination, it forwards to the relevant mailbox.
The Controlling Mechanism of Reputation-Based Mail Flow Control
The purpose of this controlling mechanism has always been to prevent you from the extensive Spam and to decline ‘False Positives.’ Following are some of the top order guidelines to make you understand the process of an email that is widely used by almost all the servers to provide you a pretty much secured environment, where you can easily manage things you desire:
What Steps are involved in this Process?
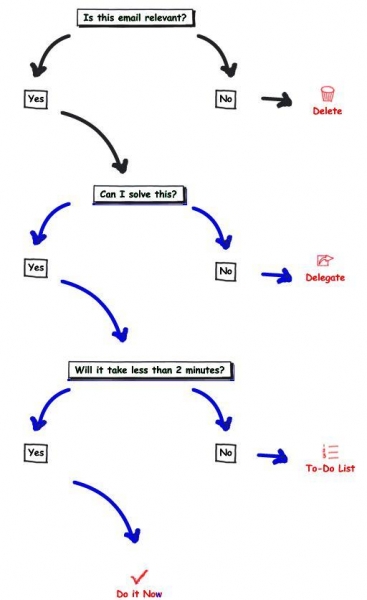
There are three main processes any mailing server can follow when sending an email to the relevant mailbox. It has been said that Yahoo, Hotmail, Google, and even Exchange Servers use the same patterns of recognizing and sending emails to the relevant recipients. These three procedures may do the following things to your message:
- Delete– if the information is incorrect or irrelevant; commonly known as spamming.
- Delegate– if the server is unable to solve the issue, it passes on the mail to the other server.
- To-Do List– If the server doesn’t take less than 2 minutes, you message may go to the to-do list.
Well, when it comes to the flow of emails from one server to another, different processes and procedures are followed to verify email, authenticate it and then to deliver it. Following are some of the easiest steps that will let you know how this system works today:
- A person sends an email to another person.
- First, the email is analyzed by the concerned server just to get to know whether it is a relevant email or not? This process verifies integrity of the communicated message. It not only checks the message for spamming and unwanted information, but it also authenticates it. If this server finds that the communicated message is irrelevant, it automatically deletes it on its own. On the other hand, if it the message is found relevant, it transfers the message as it is to another server for resolution.
- In this very step, the final server receives a resolved copy of the originally communicated message from resolving server. When it comes to the final server for approval, if it fails to accomplish it, the mail is automated towards the to-do list. On the contrary, if it remains successful in achieving approval from this server too, it is then directed towards the relevant mailbox.
This is how the mechanism of email flow works properly. You can have this process well-understood with the following diagram:
Conclusion:
Conclusively, it can be said with no hesitation that all the mail servers including http, smtp, pop and others like what are used by the mailing giants such as Yahoo, Hotmail, Exchange servers and many other are really worth-using. All of them are secure and efficient at the same time.
Moreover, keeping in vision the needs of their consumers, they have established high-spaced mailboxes and FTP servers to facilitate them with the swift receiving and delivery of data and information, which may include, images, software, videos, documents and many more. Finally, the enhancement of mail related delivery codes makes it all the processes further easy.