What Is Kubernetes?
Kubernetes is an open-source system used for the proportion of container employment. With this device, you can automate the employment, scaling, and organization of all your containerized apps and services.
Kubernetes can help you be more active, save money, use any cloud host, and keep your company’s apps buzzing. Kubernetes is demanding. Once you get beyond the basics of employ the collection and an east application or service, the learning bend gets very vertical. To make situations bad, the Kubernetes documentation unique keeps up with the new version’s releases.
Kubernetes automates container management operational tasks and includes built-in commands for employing applications, revolving out to your applications, scaling your applications up and down to meet changing needs, evaluating your applications, and more–making it easier to structure applications.
What Is Kubernetes Used For?
Kubernetes comes pre-configured to produce applications that are easy to maintain and deploy anywhere. When offered as a managed service, Kubernetes provides a variety of alternatives to fulfil your requirements. Here are some daily use cases.
How Kubernetes Works?
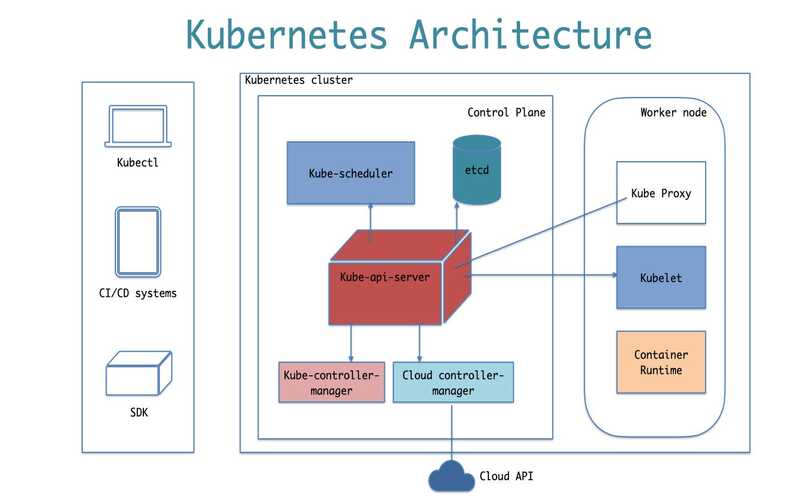
Kubernetes has a distinction for complicated because it has various moving parts. Comprehensive the primary of how they fit jointly will assist you in running out on your Kubernetes journey. A Kubernetes surrounding is known as a cluster. It involves one or more nodes. A node is easy a simple that will start your containers. It could be physical hardware or a VM.
As well as nodes, the collection also has a control plane. The control plane integrates the whole cluster’s operations. Its agenda new containers onto accessible nodes and offers the API server you collaborate with.
Why Should You Use Kubernetes?
Kubernetes’ structure enables you to employ IT resources to their sufficient.
The Kubernetes framework provides a highly accessible (HA) service and, more importantly, saves a significant amount of money.
Containerization innovation is quickly converting the patterns of IT structure of application growth, and Kubernetes retains its flag-bearer. The answerer organizations have used or planned to use container symmetry tools. Therefore, in every probability, the popularity of Kubernetes is all set to evolve in the future.
1. Kubernetes Cluster Architecture
As containers get utilized and updated with new software, the control plane ensures that such changes are pushed to all nodes. The node also admits these changes from the handle plane and pushes them to the collection. The root reasons for any errors with the handle plane are generally something that the handle plane has to work around. It might be the holder runtime engine or a bug in the holder networking carter. By starting on a collection of nodes, the handle plane is much more contributes and is less likely to cause errors.
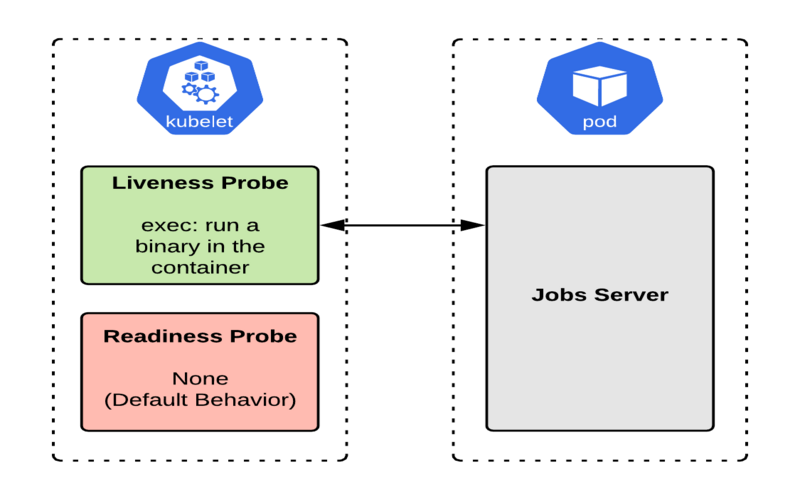
2. Use Readiness And Liveness Probes
It would assist if you exploited Kubernetes to confirm probes like readiness and brightness probes to remove pod failures forwardly. For instance, Kubernetes uses an aptness probe to verify whether the application can control the traffic before going to a pod. With a liveness probe, Kubernetes does a health check to validate the application’s compassion and that it will start as expected.
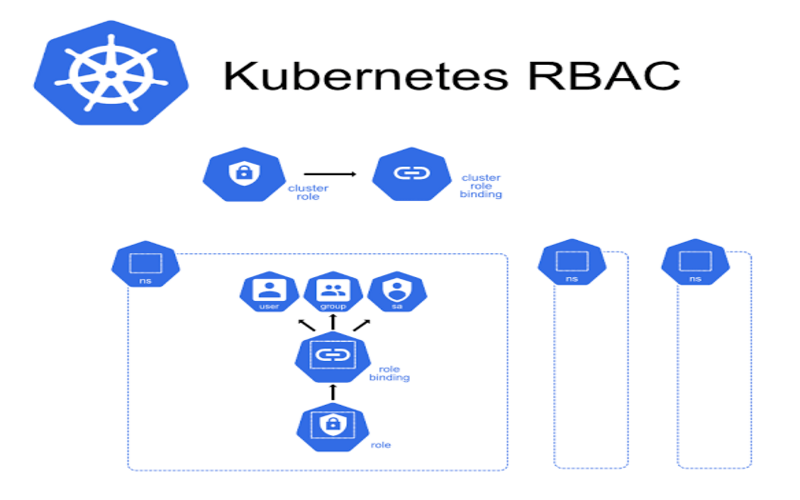
3. Deploy RBAC
Role-based access controls (RBAC) assist you a operate access rules that define who can do what on the Kubernetes collection. To enable RBAC authorizations on Kubernetes resources, Kubernetes offers parameters such as a role for a namespace resource and a collection role for a non-namespace resource. RBAC also improves the security of the structure.
4. Kubernetes Exploitable Threats
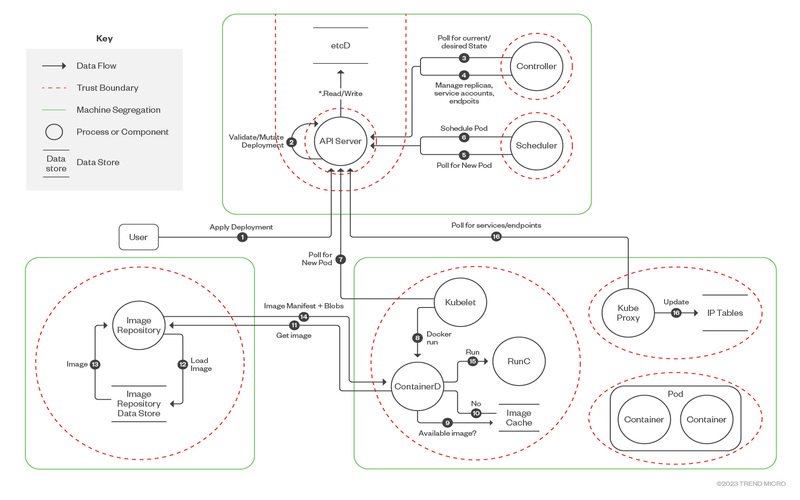
Kubernetes is a container organization field that is pre-owned by many businesses as a way to organize their applications. Though Kubernetes also has various exploitable threats that can hinder the cyber security of management. A current survey shows that 46% of contributor to organize, scale, and automize computer application employment. Given the widespread deployment of Kubernetes by businesses worldwide, Kubernetes risks can increase the attack surface, putting management at risk. The first of these threats is the lack of verification services in Kubernetes, which implies that anyone with access to the Kubernetes controller server can access any consumer account, potentially resulting in data violations.
5. The Cloud-Level Security Of Kubernetes
Kubernetes is a rugged device for organizing containers and their trust. Kubernetes has been patterned to be highly accessible, self-healing system that can be start on any cloud structure or even on physiological servers. Kubernetes is at the heart of any organisation or startup’s cloud-native application development processes, but it’s also important to understand how threats to Kubernetes’ cloud-native protection might jeopardise cybersecurity.
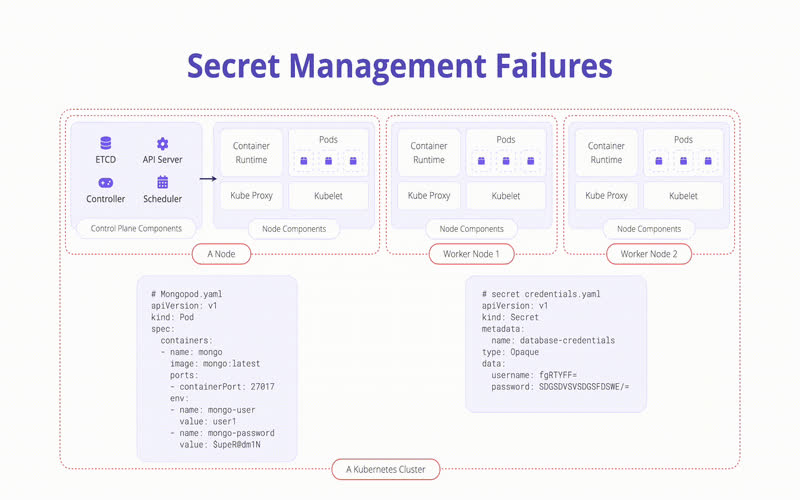
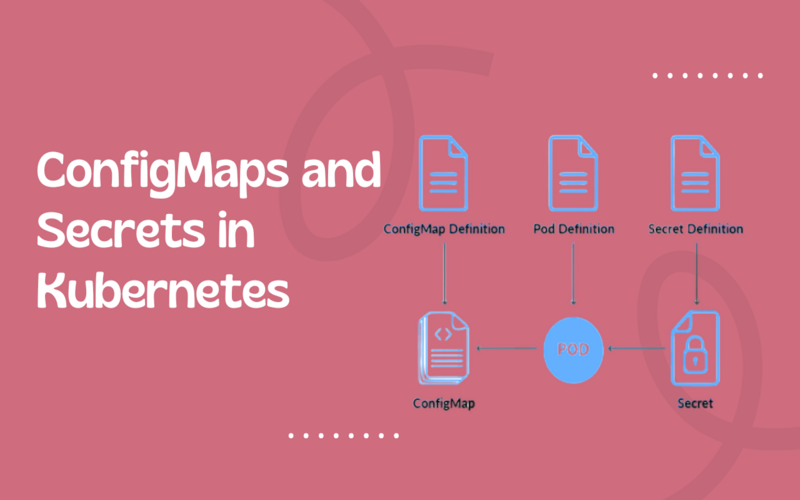
6. Secrets And Config Maps
Secrets are pre-owned to insert sensitive information such as API keys, certificates, and other kinds of credentials. They can provide Pods as surrounding variables or files mounted into a volume. Config Maps are a parallel theory for non-sensitive information. These objects should store any general settings your app needs.
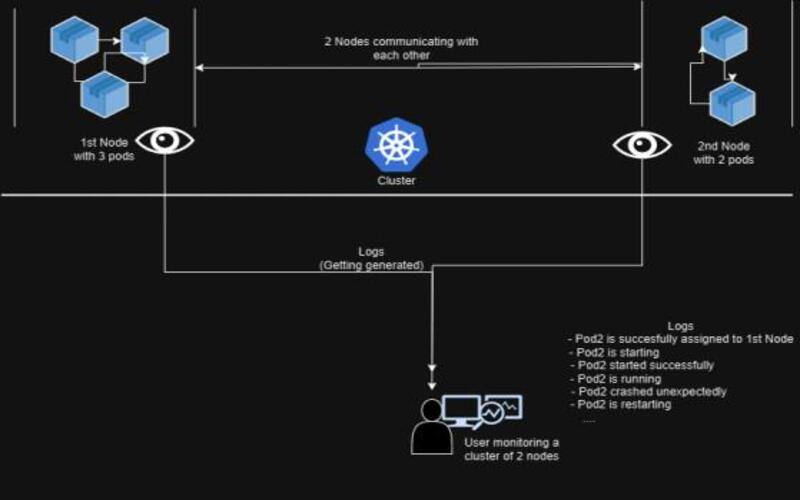
7. Observing And Centralized Logging
Kubernetes is a stable field. Its self-healing abilities will solve many errors and if you don’t know where to look you wouldn’t even regard. However, that does not mean observing is unimportant. I have look groups starting manufacturing without proper evaluation, and suddenly as certificate expired, or a certificate extinct, or a node memory commit caused an outage. You can simply avoid these failures with proper evaluation in place.
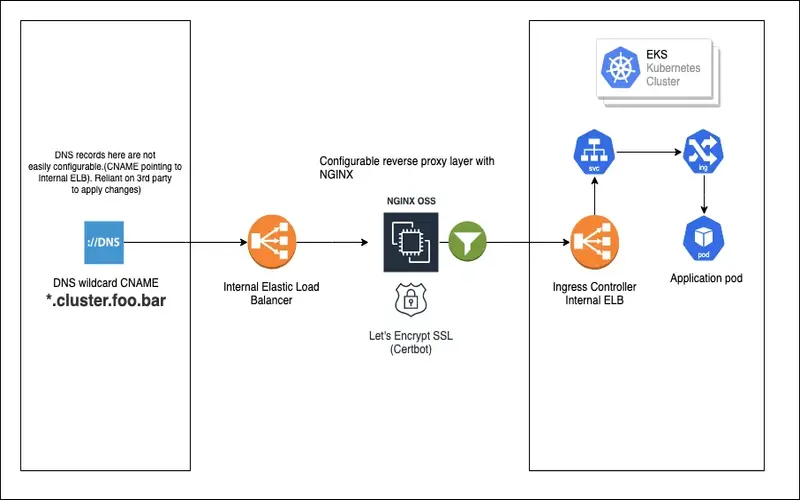
8. Centralized Ingress Controller With SSL Certificate Management
Kubernetes has a theory of accession. An easy configuration that explains how traffic should go from outside of Kubernetes to your application. A necessary access controller (for example, Nginx) can be launched in the collection to organize all incoming traffic for every application. When an accession Controller is connected to a private cloud load balancer, all traffic is instantly load balanced among nodes and delivered to the appropriate pod IP addresses.
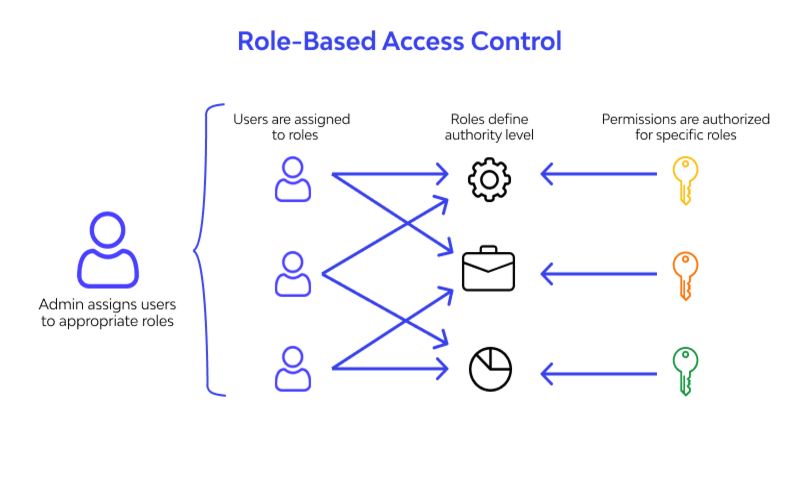
9. Role-Based Access Control
Not everyone should be a Kubernetes executive. We should always supply the rule of Least advantage regarding Kubernetes access. Role-Based Access Control should be enabled across the whole Kubernetes stack. When we merge Kubernetes with a solution like essential cloak, Azure AD, or AWS Cognito, we can centrally organize permission and authorization using OAuth2 / OIDC for both platform devices and applications.
10. Secret Management
Kubernetes secret evident are pre-owned to insert secrets into your containers, as surrounding adaptable or file mappings. Ideally, not everyone should be able to authorize all secrets, especially in manufacturing. Using Role-based Access Control on secrets for group members and applications is a good security practice. Secrets can be inserted into Kubernetes using a CI/CD device or by a local development surrounding, but this can result in arrangement state wander. It is not accountable and not simply manageable.