Cryptography or Cryptology is an art of either making a code or solving one. Cryptography is used to convert a given piece of information into a secret code that only sender and receiver can know.

Overall Process:
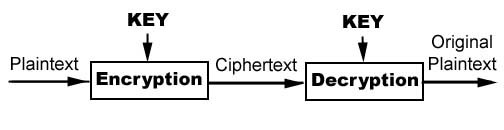
Given a plaintext (Text to be converted to code), a function is applied to that plaintext with a unique key that only sender and receiver have. The function transforms the given plain text into cipher text (Unintelligible Text).This process is known as Encryption. Now further, this cipher text is transferred to the receiver end where decryption process is performed using the same key. The following figure gives you an overall idea:
Types:
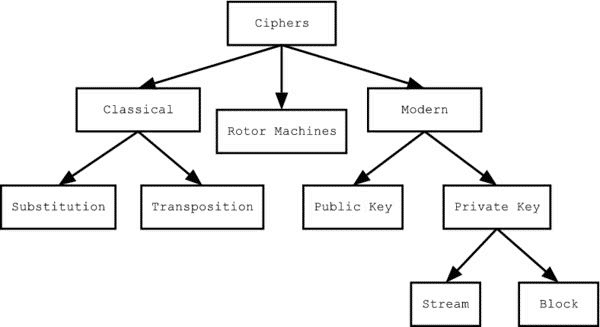
Based on the key distribution and encryption algorithms, Cryptography is divided into many kinds. There is Symmetric Key Cryptography wherein the key used at the encryption and decryption ends are the same. There is also an Asymmetric Key Cryptography where there are different public and private keys available for the encryption and decryption process and to make it stronger.
With the advent of cryptography, there also comes security which matters a lot. No encryption algorithm is foolproof and given enough time and computing power any strong encryption shatters and decodes quickly. Cryptanalysis is a term used an invader eavesdrop wherein on the network and causes harm my modification of content or more harm by a DOS (Denial of Service) attack.
Classified according to its type of intention, Attacks are of two kinds. One is wherein the attacker is happy by viewing (eavesdropping) of private information and the other where the attacker tries to manipulate the information.
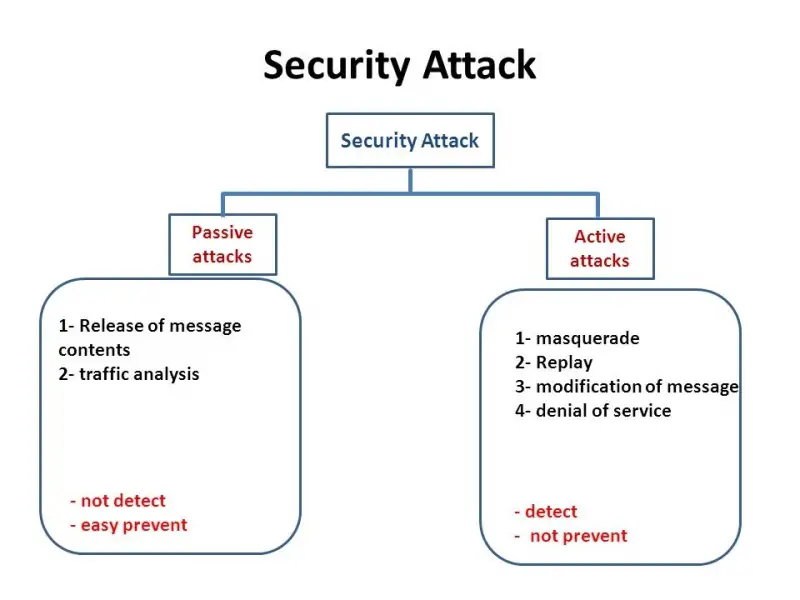
As we can see, passive attacks are not easy to detect. Active attacks, on the other hand, quickly identified as the message changes. In Passive Attacks, the sender and receiver might not have a hint of eavesdropping too.
Active attacks:
- Masquerade
- Modification of Message
- Replay
- Denial-Of-Service
Various ciphers are available. Some of them are:
- Block Ciphers
- Stream Ciphers
- Ceaser Cipher
- Playfair Cipher
- Rail Fence Cipher and much more.
The most widely used Encryption Algorithm is DES(Data Encryption Standard). Now a version of DES – Triple DES or 3DES is primarily used. It uses a ‘fiestel’ structure which involves ‘Confusion’ and ‘Diffusion’ by Claude and Shannon. AES(Advanced Encryption Standard) is also much widely used but understanding the working of AES is more complex.
Cryptography and Network Security has its flaws and advantage. Given the rate of development there is more to come in the next years, but on the same hand, cryptanalytic attacks are increasing day by day.