As corporate networks continue expanding to meet business needs, with more devices connecting remotely, ensuring endpoint security remains crucial. Malware threats keep evolving, even targeting critical network components like DHCP servers. Robust prevention controls help, but organizations still need effective malware detection and removal capabilities as well. I outline the top 10 malware tools suitable for DHCP environments based on common criteria like impact on network availability, detection accuracy, usability, and automation integration.
DHCP servers manage dynamic IP address assignment so availability is critical. Any malware detection methods used must minimize associated network downtime. Accuracy also warrants emphasis since false positives interrupt operations unnecessarily. Meanwhile, security teams need usable interfaces when investigating alerts, and integrating detection tools with other systems like SIEMs enables automation possibilities. As DBAs evaluate options, they should prioritize solutions delivering optimal detection without hampering server availability or manageability.
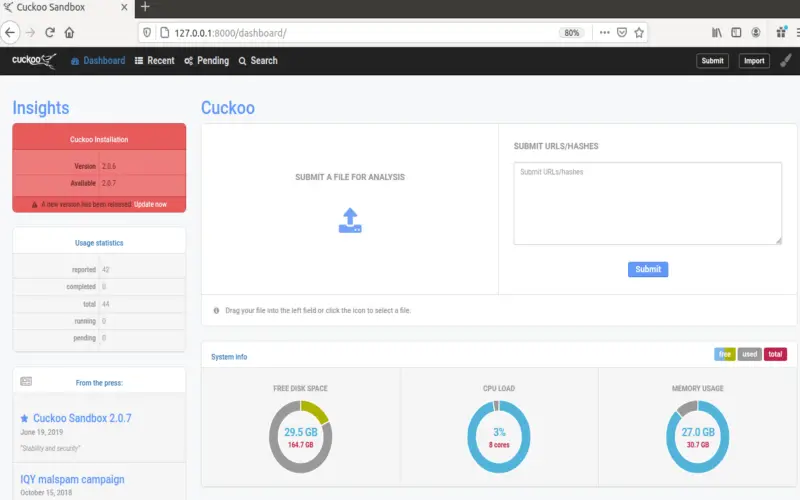
1. Cuckoo Sandbox
Cuckoo Sandbox offers dynamic malware analysis by executing suspicious files in isolated virtualized environments. It monitors system changes during execution to assess threat levels. The tool integrates with common anti-virus scanners to maximize detection accuracy. Cuckoo also automatically extracts activity indicators from testing to enable threat hunting across the broader network. Virtualization ensures malware has no impact on production DHCP servers during detection. Automated signature extraction also facilitates quicker identification of related threats. However, some malware detects sandbox environments. Evasion lowers detection rates, though Cuckoo still warrants consideration given minimal production downtime risk.
2. IDC Pro
Correlating event logs from multiple sources helps identify malware more accurately by establishing fuller activity timelines. IDC Pro aggregates events through built-in connectors for various network components, including relevant DHCP server solutions. Security analysts can visualize correlated event data to spot anomalies indicating potential threats. Useful dashboard views also simplify investigation and response workflows. Log correlation reduces dependence on anti-virus signatures alone, which malware frequently evades. Presenting consolidated data chronologically often highlights attack patterns even across partially obfuscated activities.
3. CrowdStrike Falcon Insight
Falcon Insight introduces agentless malware detection by analyzing network traffic flows from switches and routers using smart network sensors. The solution checks communication patterns against indicators of compromise detailing known attack types. Detected threats prompt recommended actions like isolating compromised devices. Admins also gain fuller network visibility to investigate security incidents. The network traffic analysis approach minimizes performance concerns associated with running detection tools directly on production servers.

4. Hybrid Analysis
Payload security company Hybrid Analysis focuses specifically on assessing suspicious files submitted by users across arrays of detection engines including customized machine learning models in safe environments. Admins access detailed reports with threat ratings and activity timelines to guide incident response. The tool even highlights file similarities to aid malware family classifications. By providing mass file testing capabilities, Hybrid Analysis helps security teams prioritize alerts from other systems that may lack sufficient context to evaluate independently, like when unusual network traffic spikes occur.

5. Limon
As a sandbox tool, Limon also analyzes file activities in isolated environments to gauge threat levels. It focuses specifically on hosting processes though rather than observing full system changes. The more limited scope enables faster performance and testing automation while still covering critical attack vectors like code injection techniques. An API-first architecture ensures straightforward integration with protective controls like PowerShell Constrained Language Mode as well. The DLL and code injection testing effectiveness aligns well with common attack types targeting networking components and servers. Limon also imposes minimal availability risks given simulations occur fully outside production environments.
6. VirusTotal
The VirusTotal malware aggregation engine compares submitted files against dozens of antivirus scanners and online sandboxes, collectively gauging threat levels. The solution incorporates multiple detection approaches to improve catch rates. Users access annotated reports highlighting activities observed across integrated tools with remediation recommendations. By aggregating outputs from various systems, VirusTotal delivers highly comprehensive malware assessments. Organizations avoid needing to invest in every commercial offering individually.

7. Wireshark
The network analysis tool Wireshark enables security teams to inspect network packet data for communication anomalies that may indicate malware. Useful warning signs include unfamiliar user agents, illegal protocol command usages, suspicious DNS queries, and unexpected data exfiltration attempts. Wireshark captures can even decode and display contents within encrypted traffic once session keys are extracted. Deep visibility into network communications facilitates early threat detection, often before malware executes attack stages impacting availability.

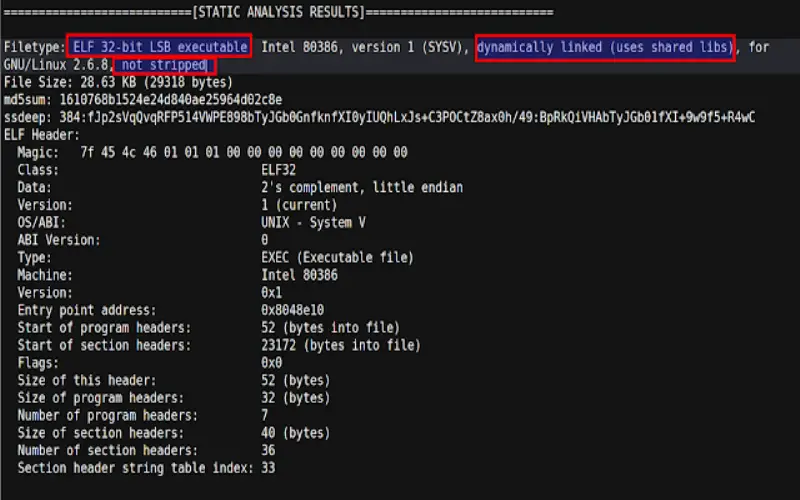
8. PeStudio
As primarily a static file analysis tool, PeStudio generates malware assessments by dissecting structure and coding characteristics without direct execution. The scanner profiles file properties across categories like entropy levels, packing detections, and security implementations to help classify threats. An API enables automation for large enterprises, while free licensing keeps the tool accessible for smaller organizations as well. Avoiding simulations during scans eliminates attack risks to DHCP servers from active malware. However, evasive malware leverages dynamic code implementations to disguise threats not apparent statically.
9. Fiddler
Fiddler stands apart as a web debugging proxy furnishing inspection capabilities for traffic between devices and servers. Unlike other tools that merely show network parameter values, Fiddler captures entire sessions. DBAs utilize it to troubleshoot connectivity issues and identify dubious security certificate validations during server requests made by some rogue application potentially attempting a breach. It warrants installing Fiddler’s root certificate as trusted to avoid breaking HTTPS encrypted data flows. Once configured, it decrypts sessions at the proxy before passing them to destination web servers. Fiddler displays detailed metadata like cookies, headers, parameters, and timings allowing review of individual transmissions flagged as mishandled by other monitoring systems.
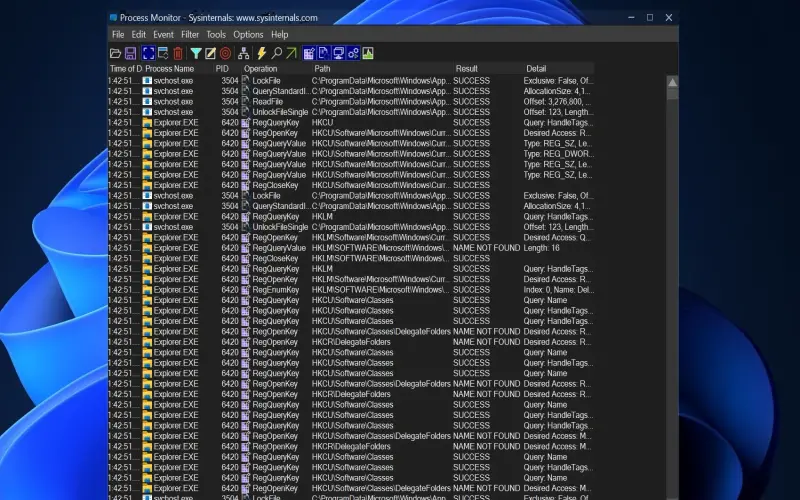
10. Process Monitor
As part of Sysinternals, Process Monitor supports dynamic real-time monitoring of process launches, file system access calls, registry key changes, and network connections drilling into activity initiated on DHCP servers by potentially infected programs. It avoids needing prior indicators of breach unlike other tools since Process Monitor looks at actions attempted by processes themselves. The Find option allows filtering huge data streams for anomaly assessment. For instance, unfamiliar executables strangely locating DLLs and mysterious registry modifications warrant inspection. Process Monitor furnishes comprehensive logging capacities with export options compatible for integrating with blocking tools. It offers built-in highlighting of suspicious patterns too.