A massive cyberattack that initially hits Ukraine has also spread around the world and causes major disruption. The attack, which was the biggest in the history of Ukraine, has also affected countries like India, Spain, and the UK, and may work like the enormous “WannaCry” cyberattack that damaged the NHS.
Petya or also known as Petrwrap is another ransomware that has caused massive turmoil in many large companies like WPP Plc, St Gobain, Evraz, Maersk, Rosneft, and Chernobyl Nuclear Power Plant. Victims around the US and Europe won’t be able to unlock their computers even if they pay the ransom.
Similar to the WannaCry attack, Petya also displayed a message on the infected computers, and demand a $300 Bitcoin ransom. The victims who already pay will be asked to send payment confirmation to a certain email address. However, Posteo, the German email provider of the said email address has already shut it down. Because of this, victims can no longer contact the intruder for the decryption key to recover their files.
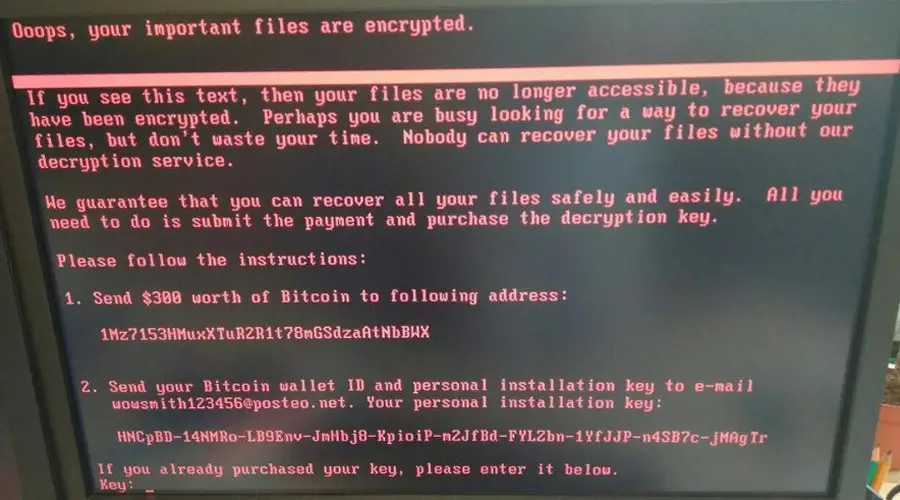
Unlike other popular ransomware that encrypted the files one by one, Petya will prevent the user from accessing their full computer system by infecting the low-level structures on the disk. Aside from the boot loader, the intruders also created a tiny kernel. The malicious code will be written at the start of the disk and will affect your computer’s Master Boot Record (MBR). The custom boot loader that holds this tiny kernel will overwrite MBR and will continue with further encryption. The ransom note on Petya’s warning message stated that they have encrypted the full disk, but it is not true. They have encrypted the Master File Table (MFT) so the file system will become unreadable.
Petya is capable of self-propagating by creating a list of target machines. Many companies have installed the patch to secure themselves from the WannaCry, but the Petya ransomware appears to have other ways of spreading themselves, and this is by aiming the administrator tools of the network.
However, according to the analysts from Kaspersky Labs cyber security, the new attack is not a variant of the Petya ransomware as reported, but it is something that has not been seen before. They called it the ‘NotPetya’ cyberattack and it affected over 2,000 users from Ukraine, the UK, the US, Poland, France, Germany, and Russia.
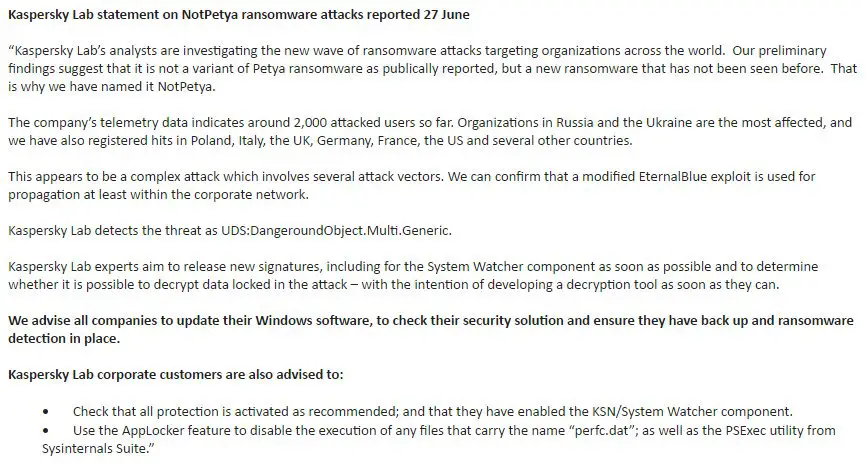
Researchers also believed that this attack is a modified version of Petya, but they found out that this was indeed a new strain that borrowed codes from Petya. Therefore, they started calling it Petna, NotPetya, or Sorta Petya, and because of its global outreach, the cybersecurity researchers started analyzing, hoping to find a kill switch domain or a dodge that would cease it from spreading.
While attempting to resort things, Amit Serper, a cyber security researcher from Cyber Reason company, has found a way to prevent the Petya (or the NotPetya) attack from infecting computers. He stated that when the malware started working, it checks if it already runs in the past and has encrypted the folders, to avoid encrypting them again. And then, it will locate the file name that activated it from within the Windows folder. When Petya finds the ‘perfc.dll’ folder, this will be a sign that the machine has already been attacked, thus it won’t activate the encryption.
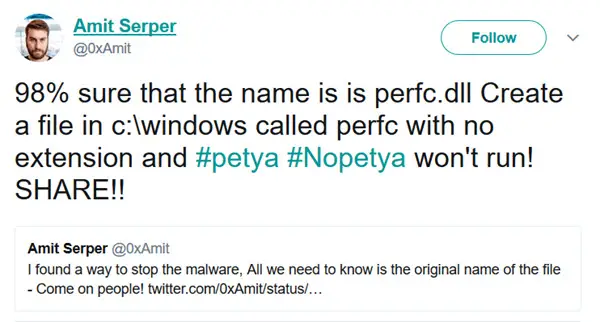
The kill switch for Petya is less pressing than it was with the WannaCry since Petya didn’t spread in the same rapid way. However, no matter what we call this new malware, the bottom line is, it still caused a major disruption to all affected companies and still, thousands of computer systems are still crippled.