Secure Socket Layer And Its Uses
- Today, applications like online banking, financial transactions during shopping using credit card and electronic stock credit, all require a secure connection. SSL fulfills these requirements by giving a secure connection. It is used to provide security at the level of Application layer.
- SSL builds a protected connection between two sockets, including 1) Parameter recognition between client and server; 2) Check the authentication for both client and server; 3) Secret communication; 4) Data reliability protection. SSL widely implemented HTTP connection. HTTPs mean a secure connection which is used by SSL.
SSL was developed by Netscape. Let’s check how its works:
- SSL divides the data into blocks of bytes or less which is known as fragmentation. Then each fragment of data is compressed by using one of the compression methods negotiated between the client and server. This service is optional. SSL uses a key hash function to create Message Authentication Code (MAC) for message integrity. After that, the original data and MAC are encrypted using Symmetric key cryptography. At the final stage, the header is added, encrypted, pay loaded and payload is then passed onto a reliable transport layer protocol.
- SSL consists of two sub protocols. One to establish a secure connection and another to use it.
The security parameter used in SSL is Cipher Suit and cryptographic secret. Cipher Suit is a combination of key exchange, hash and encryption algorithm for each SSL session. For example SSL_RSA_WITH NULL_SHA meaning key exchange algorithm is RSA, encryption algorithm is null and Hash algorithm is SHA. And the second part of security parameter is cryptography secret. To achieve security, it requires four secret keys and two IVs. Client needs one key for message, one for authentication and one IV for block encryption. And the server needs the same.
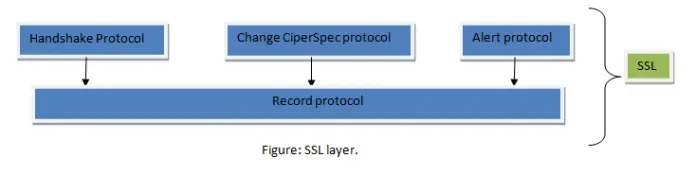
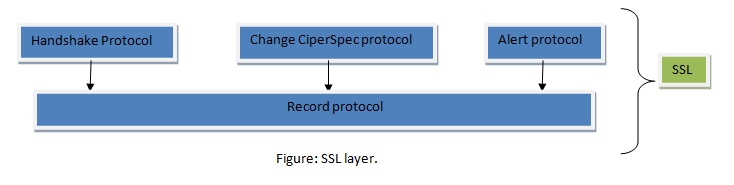
- In lower layer, SSL uses Record protocol and Upper layer uses Handshake protocol, Change Cipher Spec protocol and Alert protocol.
- Let’s discuss all this briefly. First one is Handshake protocol which provides the security parameter for the record protocol. Handshake protocols coordinate the state of the client and server. The SSL handshake protocol allows the client and server to find out the required parameters for an SSL connection such as protocol version, cryptographic algorithms, optional client or server authentication, and public key encryption methods to generate shared secrets.
- Change Cipher Spec protocol determines when two parties use parameter secret which is done as Handshake protocol. SSL prohibits the parties from using these until they have sent or received a special message i.e. Cipher Spec message. Suppose, at any time, the client wants to change the current cryptography -parameter like the handshake key exchange; at that time following the Cipher Spec notification, the client sends an exchange value and if it is available, send a verifying message and then the server sends a change Cipher Spec message after processing the key exchange message. And new (changed) key is used onwards.
- The Alert protocol is used to report unusual conditions. It is used for reporting errors and abnormal conditions. It has only one message type, the alert message, which describes the problem and its level.
- Record protocol is one type of carrier. It carries message from the upper layer which are the handshake protocol, Cipher Spec protocol and Alert protocol as well as data coming from the application layer. The message is fragmented and might be compressed. And MAC is added to the compressed message using a hash Algorithm. After that the MAC and compressed message is encrypted using the encryption algorithm and finally the header is added.