TEN TOOLS TO ENHANCE SECURITY OF COMPUTERS IN A NETWORK
What is security?
In an information technology setting, security encompasses so many aspects. Some of these aspects are:
1. Data privacy and confidentiality
This is where organizations make sure that private data of its customers of employees is kept safe and safeguarded against unauthorized access or use. Data privacy enhances data integrity. Data confidentiality is where an organization makes sure that its data and information about its daily transactions and other important data about the organization is also safeguarded against unauthorized access and use. Data should only be accessed and used by authorized personnel.
2. Protection from viruses, malware and spyware
Viruses affect computer programs, files, and documents and corrupt them. The infected files, when opened, affect other files and programs and when the rate of infection is high, the computer slows down or even crashes. Malware are and spywares are mainly passed through the internet. Malware affects the normal functioning of the computer and corrupts files. Malware and spyware may also be used to forward information about your computer to internet intruders.
3. Unauthorized access
This is where the network data or resources are accessed by an unauthorized person(s). The person may use the data for his or her own interest that are not suited to what that data what meant for by the organization. The person may also change the organization’s data. Unauthorized access of network data compromises the data security, privacy, and confidentiality.
4. Data availability
Data availability simply means that the data needed in order to process some transactions should be readily available when required.
5. Other security issues
These include other strategies that should be employed in order to enhance the security of the organization’s data and information.
Due to the above reasons, data should be protected. Data is protected because it is very expensive and very important for the day to day operations of an organization. There are many tools that Information Technology experts use in order to better enhance the network security of their organization’s data. Some of these tools are:
Nessus
Nessus is a premier UNIX tool for assessing the vulnerability of a network. Before 2005 the software was free. However, the open source license was closed in 2005 and later in the year 2008 the use of the software was at some cost. Organizations currently pay around $1200 per year to use the software. The vulnerability scanner has very high speed in discovery, auditing configurations, profiling assets, improving data recovery and analysis of vulnerabilities for a network. The software can be distributed in an organization’s network even if the network is divided into physically separate networks. Nessus is managed and maintained by a team of very experienced Information Technology experts. It has the largest vulnerability database and it is most suitable for complex networks. The most interesting thing about Nessus is that it runs on Linux, Windows, Mac OSX, and BSD. Its user interface is easy to use and very presentable. Below are Nessus screenshots from my computer.
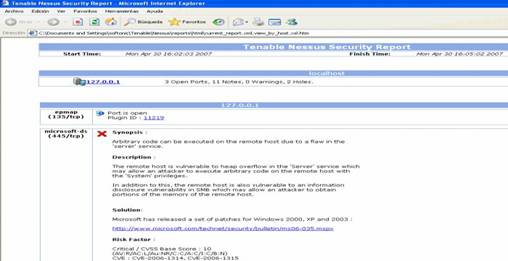
Screenshot1
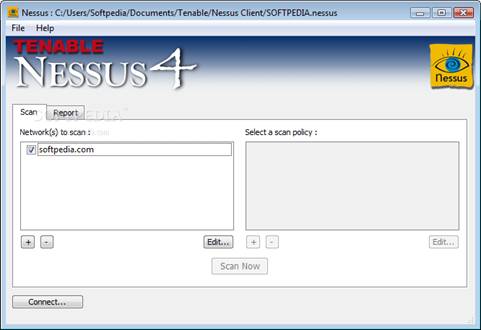
Screenshot2
Wireshark
Wireshark, which was previously called Ethereal, is a packet sniffer. It is among the most renowned open source software for protocol analysis in both Linux and Windows networks. This utility can be used to analyze data from a live network feed or from a captured file, or disk from a computer. The data is analyzed up to the packet level of the details that are required. It has a much filtered language that has very rich display with the capability to reconstruct streams of Transfer Control Protocol sessions. Wireshark is also able to support many types of media and protocols.
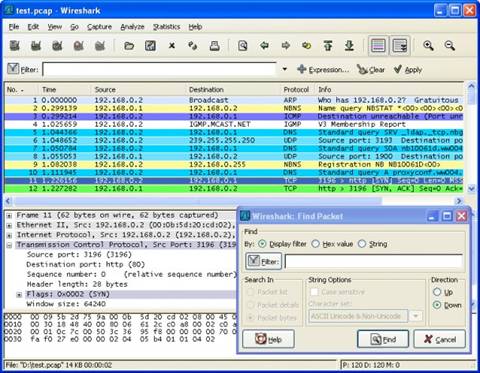
Wireshark screenshot 1
Snort
This is the most-used IDS (Intrusion Detection System). It’s a system or application that monitors the network in order to detect any activities or processes which are either malicious or do not follow the network policies set out. Snort runs on all major types of Operating Systems including Windows and Linux. Here are some screenshots of the application:
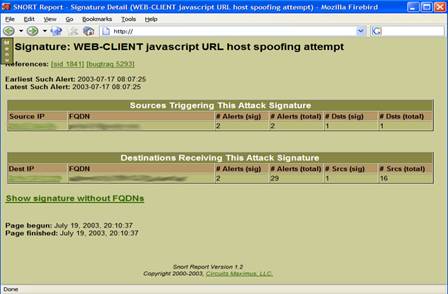
Snort screenshot1
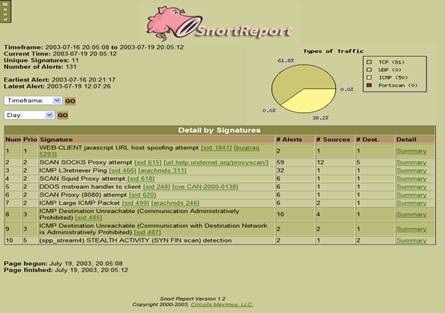
Snortscreenshot 2
Netcat
A network utility used to write data and information on the Transfer Control Protocol and User Datagram Protocol network connections. It can be used to create any type of network connection and because of this; it can also be used for debugging and network exploration. Below is a screenshot for the utility:
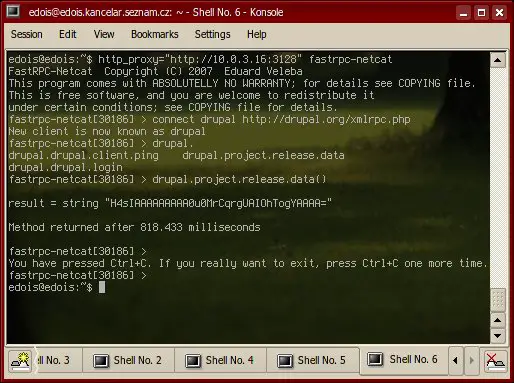
Netcat screenshot
Metasploit Framework
Metasploit Framework is a tool that is primarily used to exploit codes. This advanced open source platform application is also used for developing and testing exploit codes. Below is a screenshot for Metasploit Framework:
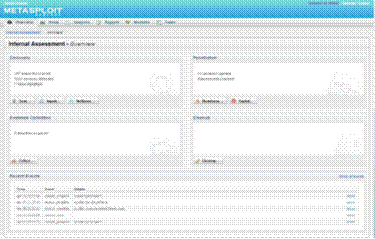
Screenshot
Hping2
This utility was inspired by the well-known command, ping. It packages and also sends the normal custom Internet Control Message Protocol, User Datagram Protocol, and Transfer Control Protocol message packets and then waits for the replies. This utility also enables fragmentation of IP addresses and mapping of firewall rule sets. It runs on all major types of Operating Systems.
Hping 2 screenshot
Kismet
Kismet is a command-based wireless detector that works at the 802.11 layer 2. Apart from being a wireless network detector, Kismet also works as a sniffer and an Intrusions Detection System (IDS). The utility identifies networks by simply sniffing and can even unblock non-beaconing (hidden) networks. It works on all the major Operating Systems.
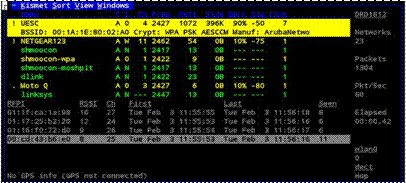
Kismet screenshot
Tcpdump
Tcpdump is a utility that is mainly used for sniffing, monitoring networks, and acquisition of data. It can be used as an alternative to Wireshark (Ethereal) utility. It is a very useful utility for tracking and monitoring network operations. It also does not require many system resources to run. It runs mainly on Windows Operating Systems. Tcpdump is a command-based utility. Here is a screenshot courtesy of http://www.FreeDownload32.com/
Tcpdump screenshot
Cain and Abel
This is, by far, the most used and effective password recovery utility for Windows systems. It has a Graphical User Interface which is very easy to use. Cain and Abel can modify or recover network passwords by sniffing or even altering those passwords that are encrypted.
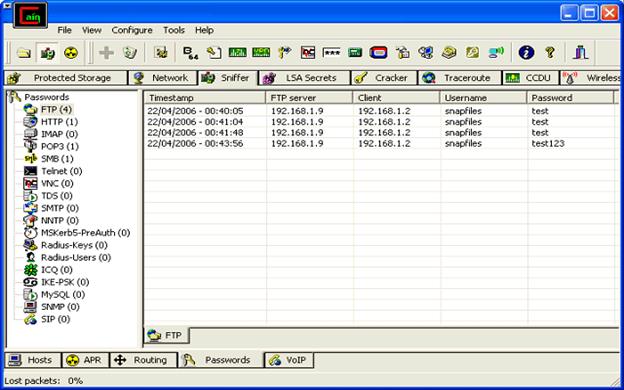
Cain and Abel screenshot
John the Ripper
John the Ripper is a very effective, flexible and powerful password modifier. It operates under all known major Operating Systems. Its source code is readily available on the internet. This utility is command-based.
Conclusion
For the very basic of utilities or tools to manage and secure networks, the Information Technology personnel charged with this task should know the uses of these tools and how to get set and configure them for the best results in protecting networks. It should be noted that there is no single utility or tool that can ensure network security by itself. Therefore, one should know the combination of these tools which will provide the best and cost-effective mechanisms for securing a network.