SNMP: Simple Network Management Protocol
Introduction
What does Network Management mean?
If you have a network of computers, hardware devices like switches, routers, database servers and workstations, surely you will have to:
- Keep track of the settings of each device and its functioning.
- Check whether the network is running smoothly and if it can handle the current workload.
- Deal with problems and emergencies in the network.
Definitions
SNMP is Simple Network Management Protocol. It was defined by IETF RFC1157 in 1989. SNMP is a protocol which allows networked devices (called Agents) and a management workstation (called Manager) to communicate with each other.
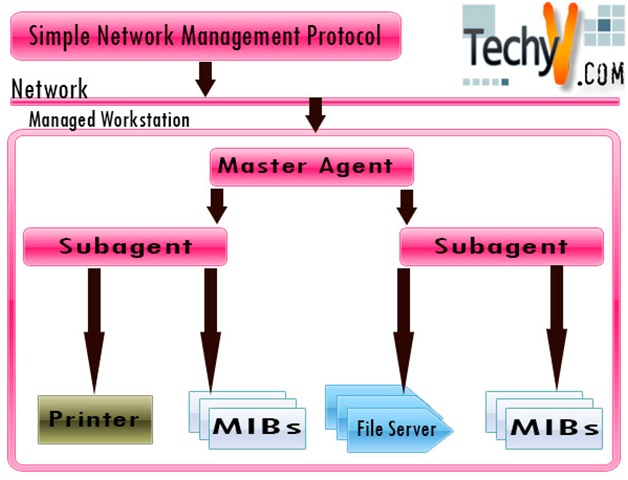
- A ‘Manager’ process runs on the management workstation that requests information about the devices on the network.
- The ‘Agent’ process runs on each of the managed device and transfers the collected information to the ‘Manager’. The information is in the form of key-value pairs called Object Identifiers (OIDs).
The Manager requests the Agent for specific information by sending the key of the specific OID. The agent analyzes the key and provides the information to the manager.
In the OSI model, SNMP defines standards for the application layer protocol and commonly uses the connectionless UDP (User Datagram Protocol) for the transport layer.
The available information (database schema and data objects) is defined by Management Information Bases (MIBs). MIB maps the complicated Object Identifiers to a human readable form and stores their values in a flat file.
The SNMP agent receives requests from the Manager on the UDP port 161 and the Manager receives the notifications on the UDP port 162.
All data fields in an SNMP message must be a valid ASN.1 (Abstract Syntax Notation One) data type, and encoded according to the BER (Basic Encoding Rules).
SNMP can be used in two ways:
- Polling – Polling is an active form of monitoring. A GET request is sent by the Manager asking for a specific value with a view to send a command or even just check if there are any problems with the device.
- Traps – Traps are used for passive monitoring, where an agent can contact another agent in the event of some action (trigger). For instance, if a link breakdown occurs, a trap message is sent to a trap host, that will process the trap message and probably send an email to a pre-configured email id.
PDU:
A PDU is a protocol data unit, that is, the data units defined by the SNMP protocol for exchange of information.
It consists of:
- IP header
- UDP header
- version
- community
- PDU-type
- request-id
- error-status
- error-index
- variable bindings
History of SNMP:
The history of SNMP goes back to 20th century.
- 1983 – TCP/IP replaces ARPANET at U.S. Dept. of Defense, effective birth of Internet
- 1989 – Marshall T. Rose heads up SNMP working group to create a common network management framework
- Aug. 1989 – “Internet-standard Network Management Framework” defined (RFCs 1065, 1066, 1067)
- May 1990 – IAB promotes SNMP to a standard protocol with a recommended status (RFC 1157)
- Mar. 1991 – format of MIBs and traps defined (RFCs 1212, 1215)
- 1999-2002 – SNMPv3 defined by RFC 3411–RFC 3418.
Versions
SNMP has moved from first version (RFC 1157) to third version with RFC 3411–RFC 3418.
- SNMP v1 specifies five core protocol data units (PDUs) namely GetRequest, SetRequest, GetNextRequest, Response and Trap, to set or retrieve OIDs and send trap messages.
- SNMP v2 added two more PDUs – GetBulkRequest to decrease the iterative GetRequest and GetNextRequest calls and InformRequest for acknowledged notification.
- SNMP v3 – Since UDP is a connectionless protocol, it is vulnerable to IP spoofing attacks. The earlier versions had a mechanism for authentication of clients that involved transmission of clear text passwords, but the current version of SNMPv3 has some security enhancements. It provides some important security features like Confidentiality, Integrity and Authentication and also Remote configuration and administration capabilities.
Usage and Implementation
Most Network Management Systems (NMS) like Sun Management Console, IBM Tivoli NetView, HP OpenView and OpenNMS use SNMP as their base.
An NMS provides a single point of monitoring and administration of all the SNMP enabled devices. So the entire environment can be monitored and controlled using NMS. Managed devices might include routers, access servers, switches, bridges, hubs, IP telephones, IP video cameras, computer hosts, and printers.
Advantages of SNMP:
- Interoperability
- Flexible
- Extensible
- Standardized
- Universally supported
- Portability
- Allows distributed management access
- Lightweight Protocol
- SNMP provides the ONLY way to efficiently manage large networks.
Disadvantages:
- Complicated to implement
- Inefficient protocol – Bandwidth is wasted with needless information like version headers and data descriptions
Usage:
- Environmental Monitoring: Server, rack and appliance operating temperatures and room humidity could be monitored and controlled remotely for SNMP-enabled devices
- Traffic Monitoring: Amount of traffic flowing through a network device
- Monitor CPU usage
- Device voltage and attributes
Vendors have different products implementing SNMP on different types of networks, namely
- IBM Nways Workgroup Manager
- InterWorking Labs SNMP test suite, SilverCreek 6.0
- Bay Networks – Optivity NMS
- AdventNet – SNMP for Java
- Hewlett-Packard HP OpenView Network Node Manager
- Cisco – 2500 and 4500 routers.
- Liebert Corporation – Uninterruptible power supplies.
Example explaining Implementation of SNMP
Let us take an example of a network of say Windows Servers. Each server is defined as a Manager or an Agent.
Windows Server 2003 has some SNMP components like Microsoft SNMP Service (Master Agent), SNMP Trap Services and SNMP Manager Application. The components can be accessed at Control Panel – Administrative Tools – Computer Management – Services and Applications – Services – SNMP Service.
Security:
An Administrator uses the Traps tab and defines these devices as members of a single SNMP community. A community name acts as a password that is shared by multiple SNMP agents and one or more SNMP managers. An SNMP agent only accepts requests from SNMP managers that are on the agent’s list of acceptable community names. Trap destinations are also specified here.
SNMP security is configured on the security tab. Here, the administrator specifies accepted community names (case-sensitive) and also whether or not to accept SNMP packets from a host. To limit the number of hosts that may accept SNMP packets, an administrator can even specify host names or their IP addresses.
These agents can then be managed by the Manager. Data gathered depends on disk space remaining on each disk drive, CPU utilization and server temperature. And in turn, using SNMP’s trap call, the Agent can proactively notify the Manager of problems before they can become fatal and downtime occurs. Say, disk drives being near capacity can trigger a trap message so that administrators can clean-up space before a potential lockup of a production server.