Why the concept of 3D passwords evolved?

Security has become a major aspect of concern nowadays; be it net banking, social media accounts, and anything that requires authentication. Present authentication systems have ample of loopholes. The choice of password made by the user is always something related to their personal life such as the name of parents, birth dates, etc.
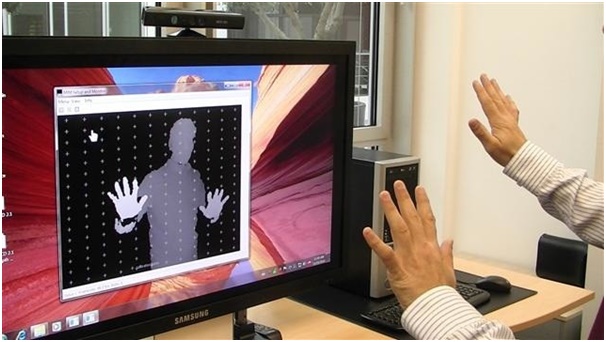
They are also using words from the dictionaries, which makes it vulnerable to brute force attacks causing privacy invasion that can lead to a long-term chronic damage. Passwords are of various types such as:
- Textual passwords: This type of password is the easiest to guess and crack. Users easily forget their passwords, so they tend to create a difficult one.
- Token based passwords: The type of password used in credit cards, ATM cards,, which are vulnerable to thefts.
- Biometrics: This type of password includes fingerprint or thumb impression, retina scanning, etc. Biometric is not only costly to implement, but people are not that willing to go through strong infrared eye scanning procedure or any privacy invasions.
- Recognition based that includes a graphical password, face recognition,, which are easy to reproduce if recorded while the password is being reproduced.
All these types of systems lack some or the other kind of authenticity, which makes them vulnerable. Hence, it has become very essential to introduce a new system, basically, a combination of all these that will negate the loopholes and create an extremely powerful security system such as 3D password, that ensures the highest degree of security.
What does 3D password exactly mean?
The 3D password is a multi-factor authentication technique that combines all the above-mentioned types of password (Textual, Token-Based, Biometrics, and Recognition). The basic concept is to create a 3D virtual environment where the user virtually moves across or navigates and interacts with the objects present in that particular environment. Based on the virtual movements and interactions inside the 3D environments, a 3D password is constructed.
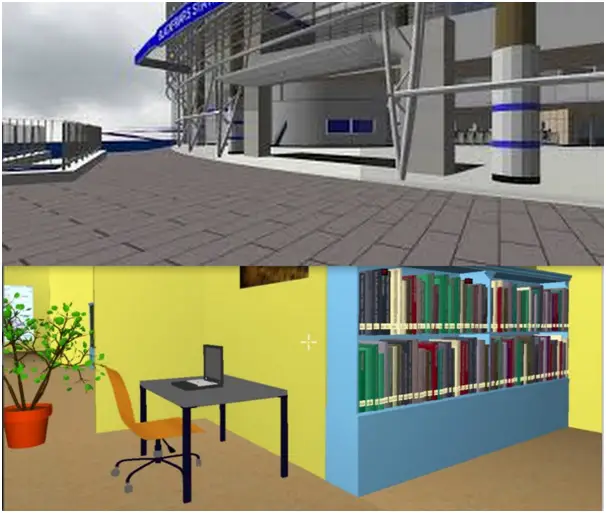
How does 3D environment work?
- The first thing that a user has to do is to authenticate the normal textual password, which includes the username and password. Once this authentication is successful, the user navigates in the 3D virtual environment, and a virtual computer with a keyboard appears on the screen on which the user will have to provide a password that is stored in a text file in the form of encrypted coordinated like x1, y1, z1.
- On the successful completion of this authentication, the user enters into the virtual environment where he/she has to do certain activities inside that particular environment like opening or closing the door or perform any activities related to the objects inside the virtual environments.
- The sequence in which these activities are performed by the user is recorded and analyzed in the form of a sequence of points, which are then stored in a simple text file but in an encrypted form. Hence, a 3D password is created this way for a respective user by designing and analyzing various algorithms.
- The next time the user needs to access the account, he/she will have to select the objects in the same sequence that he/she had done when the password was created. This sequence is then compared with the coordinates stored in the text file.
- If the user is successful in fulfilling the conditions, access is granted to the authorized user.
3D passwords can be implemented and incorporated in many other ways, which are currently being developed.
The degree of convenience and advantages:
The construction and use of 3D passwords are assured to be extremely user-friendly and easy to understand. Research and development are still required to put it in complete use since it’s still in its early stages. Presently, graphical and textual passwords are in use, which is highly vulnerable security keys. Hence, more powerful authentication schemes are under development, and one of them is the 3D password. The foremost factor of convenience is that users can design and create the password of their choice.
3D password is considered to be the safest authentication method because it negates every security threat, well almost. Some of the common security breaches are as follows:
- Timing attack: A timing attack uses statistical analysis on how long a program requires to accept a given authentication key.Based on this statistical information, it is easy for an invader to crack the password. Timing attacks are not effective in 3D passwords.
- Brute force attacks: In such attacks, the attacker tries to crack the password using certain possibilities. 3D password is a sequence of activities in the virtual environment, which is nearly impossible to guess and also creating a 3D virtual environment is costly.
- Well-studied attacks: In these types of attacks, the attacker studies different attacking schemes and tries the combination of these schemes. Since 3D password is based on multi-factor and combinational techniques, it becomes difficult to implement these attacks.
- Keylogger: Software called keylogger is installed where the software stores the texts entered through the keyboard on a particular computer or system, making the attack more effective. But 3D password, as a combination of different types of password, this attack also remains ineffective on 3D passwords.
- Shoulder surfing attacks: Here, attacker captures and records the passwords using the camera. This attack is known to be the most effective attack amongst others. The only way to avoid this attack is to create the password in safe environments. Methods to fight against shoulder surfing attacks are under development.
Hence, this makes the 3D passwords the safest method till date, and research is still being carried out to make them even effective. Some of the major applications of 3D passwords are in fields like networking, nuclear and military security, airplane and jet fighters, etc.


















