Encryption in all likelihood isn’t something that you spend quite a little time wondering about; however, it’s an essential component of your online safety. A variety of encryption kinds such as 3DES, AES, and RSA algorithms and others are utilized in a lot of our stable protocols, inclusive of TLS/SSL, IPSec, SSH, and PGP.
How does encryption work?
The encryption software program converts big volumes of statistics into cryptic textual content or numbers the usage of algorithms. Only the one’s human beings or structure with the decryption key can decipher the encrypted statistics. A four-bit key makes use of 2^4 (i.e., 2 to the electricity of 4) combinations. That approach a four-bit key most effective has sixteen feasible combinations, which makes the important thing smooth to do. That’s why the contemporary-day fashionable is a 256-bit key that makes use of 2^256 feasible combinations, a 78-digit wide variety that outcomes in very robust encryption.

Four most used encryption strategies
Different encryption strategies are primarily based totally on the form of keys used, key length, and the length of statistics blocks encrypted. Here are a number of the not unusual place encryption strategies which you would possibly see utilized in diverse encryption tools:
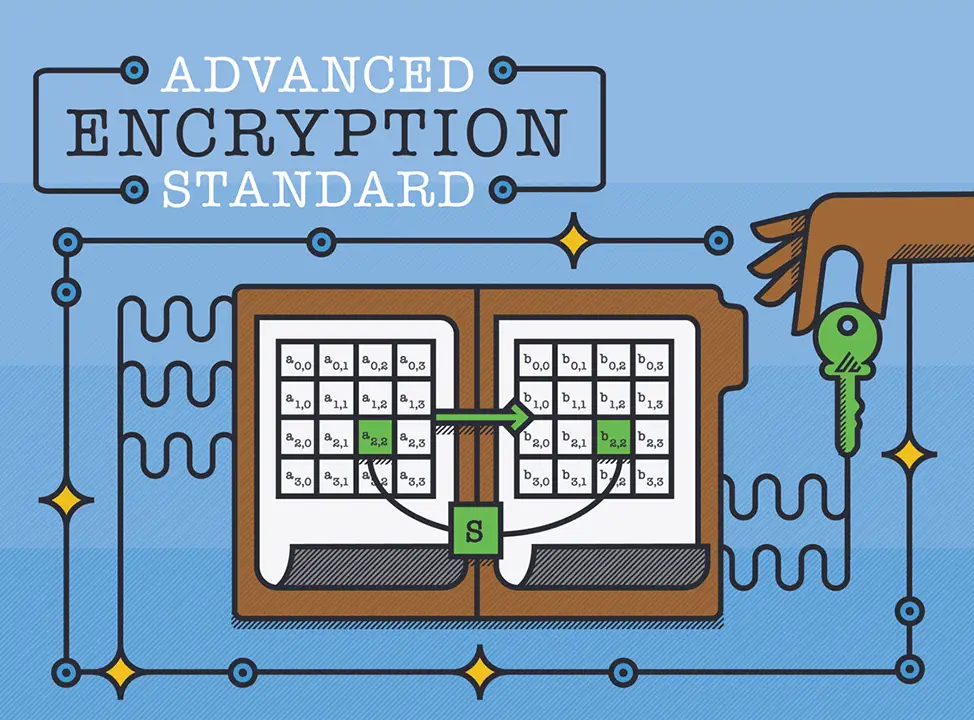
1. Advanced Encryption Standard (AES)
Advanced Encryption Standard is a symmetric encryption set of rules that encrypts constant blocks of statistics (of 128 bits) at a time. The keys used to decipher the textual content may be 128-, 192-, or 256-bit long. The 256-bit key encrypts the statistics in 14 rounds, the 192-bit key in 12 rounds, and the 128-bit key in 10 rounds. Each spherical includes numerous steps of substitution, transposition, the blending of plaintext, and greater. AES encryption requirements are the maximum generally used encryption strategies today, each for statistics at relaxation and statistics in transit.
2. Rivest-Shamir-Adleman (RSA)
Rivest-Shamir-Adleman is an uneven encryption set of rules this is primarily based totally on the factorization of the made from big high numbers. Only a person with an understanding of those numbers may be capable of decoding the message successfully. RSA is regularly used whilst transmitting statistics among separate endpoints (e.g., internet connections), however works slowly whilst big volumes of statistics want to be encrypted.

3. Triple DES (Data Encryption Standard)
Triple DES is asymmetric encryption and a sophisticated shape of the DES approach that encrypts blocks of statistics the usage of a 56-bit key. Triple DES applies the DES cipher set of rules 3 instances to every statistics block. Triple-DES is generally used to encrypt ATM PINs and UNIX passwords.

4. Twofish
Twofish is a license-loose encryption approach that ciphers statistics blocks of 128 bits. It’s taken into consideration the successor to the 64-bit Blowfish encryption approach and greater flexibility than its specialized successor, Three fish. Twofish continually encrypts statistics in sixteen rounds irrespective of the important thing length.

What is the maximum stable cryptography?
The solution is Advanced Encryption Standard. AES encryption is one of the maximum stable encryption kinds; Advanced Encryption Standard (AES) is utilized by governments and protection groups in addition to regular agencies for labeled communications. AES makes use of “symmetric” key encryption. Someone at the receiving stop of the statistics will want a key to decode it.

Has AES-256 been cracked?
The distinction between cracking the AES-128 set of rules and the AES-256 set of rules is taken into consideration minimal. In the stop, AES has in no way been cracked but and is secure in opposition to any brute pressure assaults opposite to perception and arguments.

Can NSA crack 256-bit encryption?
In the present day world, there are numerous assaults to be had to get admission to encrypted content, and the NSA or different country actors have the sources to do maximum of them. The actual brute pressure 2^256 mixture checking out is silly and impractical and could essentially in no way be feasible. The NSA is doing studies on whether or not a cryptographic assault primarily based totally on tau statistics might also additionally assist to interrupt AES. At present, there may be no recognized realistic assault that could permit a person without an understanding of the important thing to study statistics encrypted through AES whilst efficaciously implemented.

Why is AES higher than DES?
AES statistics encryption is a greater mathematically green and stylish cryptographic set of rules; however, its important electricity rests within the alternative for diverse key lengths.
Why AES is maximum stable?
AES brings extra protection as it makes use of a key growth technique wherein the preliminary keys are used to provide you with a sequence of recent keys referred to as spherical keys. These spherical keys are generated over more than one round of modification, every of which makes it tougher to interrupt the encryptions.