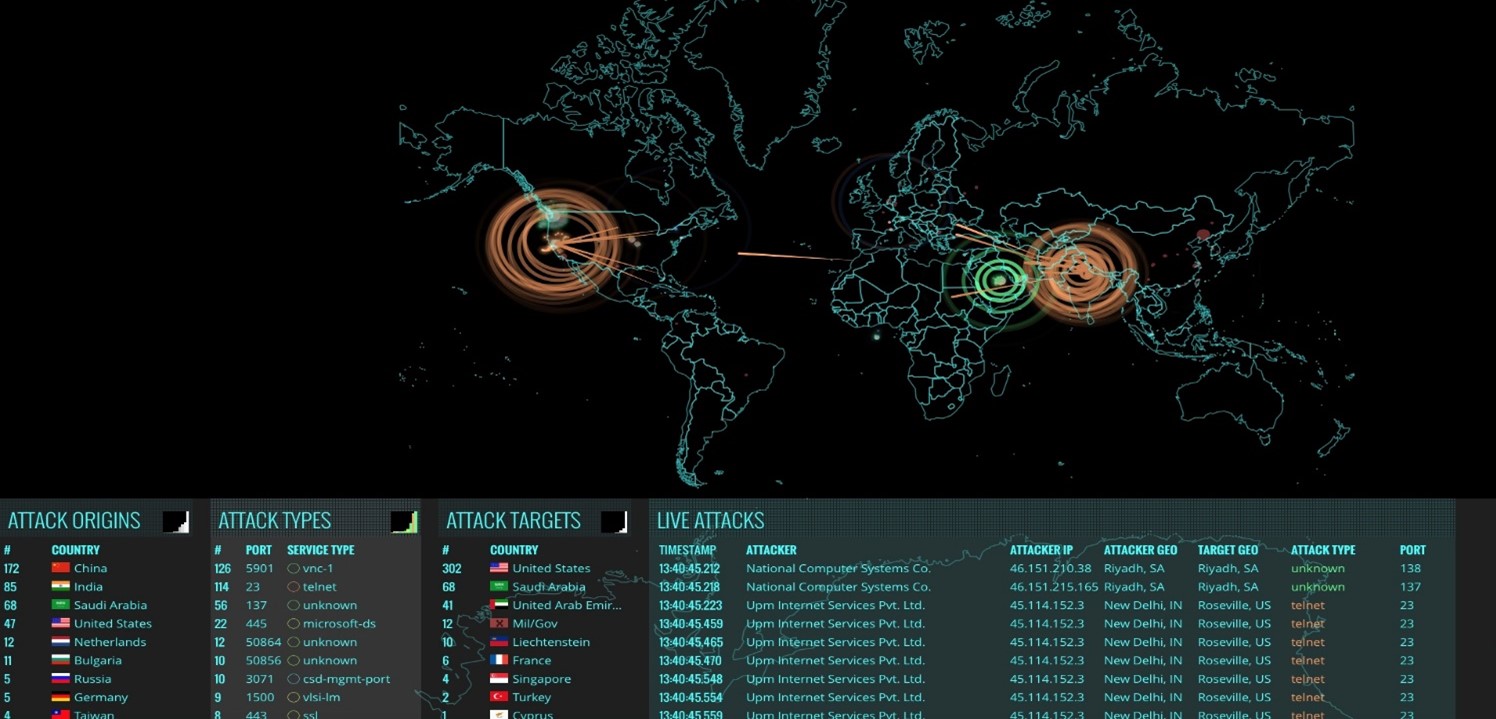
Few online criminal activities are more annoying and challenging to stop than distributed denial-of-service (DDoS) attacks. Because of the server overload caused by these attacks, even the busiest websites can go offline. Servers crash when they can’t handle the volume of junk requests, and it usually takes hours to fix them. Denial-of-service attacks can occur anytime, affect any aspect of a website’s functionality or resources, cause numerous service outages, and result in significant monetary losses. DDoS attacks were originally only for fun, but research reveals that hackers increasingly use them for profit or disruption.
1. Volumetric Attacks
Volumetric assaults use the available network bandwidth by saturating a target network with data packets. These attacks overwhelm the targeted network or server with massive traffic, severely disrupting service for authorized users attempting to access it. Seizures caused by volumetric phenomena are growing in size, sophistication, and longevity. They can bring down any corporate server in a matter of minutes. This network-level (layers 3 and 4) assaults aim to overburden a server’s network resources, internet connection, and other appliances that are unable to handle the increasing load.
2. SYN Flood Attacks
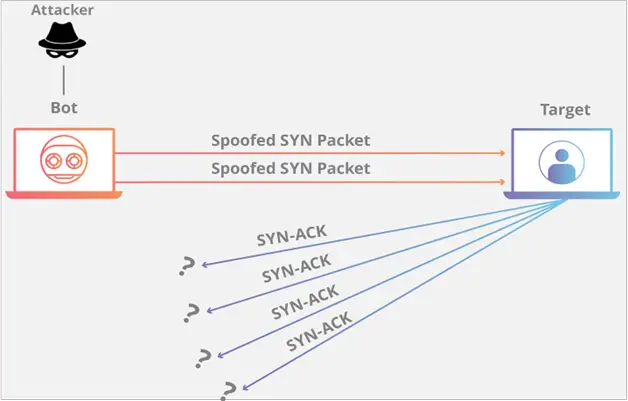
The requester initiates a TCP connection with a host by sending an SYN message first in the TCP connection sequence (also known as the “three-way handshake”). In response, the server issued an SYN-ACK, and they were followed by the requester acknowledging receipt of the ACK message. The network connection is now open. An SYN flood attack involves the requester sending several SYN messages to the targeted server without sending any ACK messages for confirmation. Additionally, the requester can send spoof SYN packets, prompting the server to send SYN-ACK answers to a fake IP address. Of course, since it did not send the SYN signals, it never replies. The SYN flood locks up server resources and prevents the establishment of any new connections, leading to a denial of service. A combination SYN flood combines two SYN attacks; one employs little SYN packets under 250 bytes and the other big SYN packets. The standard SYN packets drain server resources (such as the CPU), while the bigger packets create network saturation. Both assaults are carried out simultaneously.
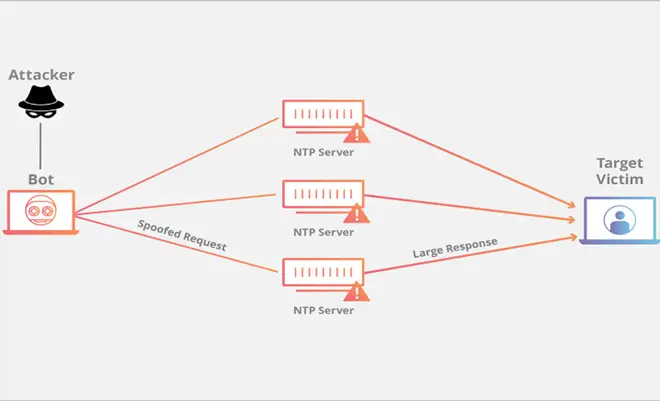
3. NTP Amplification Attacks
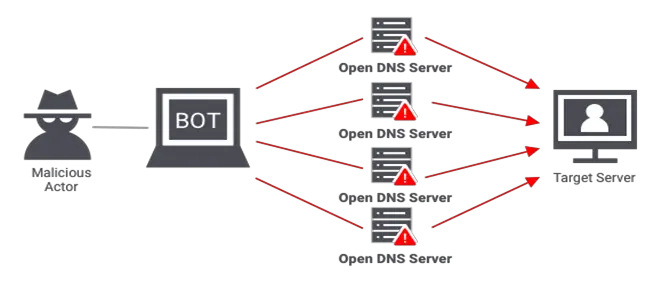
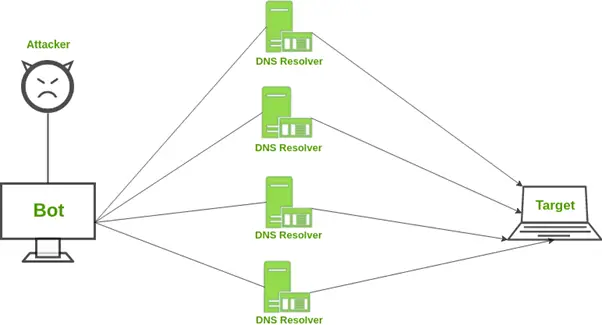
Computers use the Network Time Protocol (NTP) internet to synchronize their clocks via the network. An NTP server feature called MONLIST, which returns a list of the latest 600 IP addresses to contact with the server, is used in NTP amplification attacks. Attackers use a target server’s fake IP address to send MONLIST requests to NTP servers. As a result, the NTP server’s answer is considerably more significant than the first request. Attackers can swiftly take control of the target server by leveraging many vulnerable NTP servers and overwhelming it with many data packets. Large-scale NTP amplification attacks are possible partly due to the underlying UDP protocol’s lack of a handshaking requirement.
4. ‘ Hit And Run’ Attacks
As their name suggests, hit-and-run attacks are long periods with sporadic, brief packet bursts. What distinguishes these threats from other DDoS attacks is that episode might linger for several days or weeks. Additionally, they are not continuous like other attacks and are made expressly to take advantage of anti-DDoS systems that take a long time to respond.
5. Bot Attacks On Web Browsers
Malicious software code fragments executing inside a web browser make up browser-based bots. The bots operate while a user is actively exploring the web and shut down immediately when the browser is closed. By visiting a rogue website, browser-based bots are covertly installed on the machines of unwary users. Several bots can then use the infected devices to attack a targeted server at once. Some DDoS bot types mimic browser functionality, such as cookie support, to get beyond anti-DDoS safeguards. DDoS bot attacks are harmful since they don’t need large quantities to succeed; they target the application layer. A mid-size server can be brought down in under a second with 50 to 100 targeted requests per second. Bot assaults are challenging to spot and frequently become apparent after the damage has already been done.
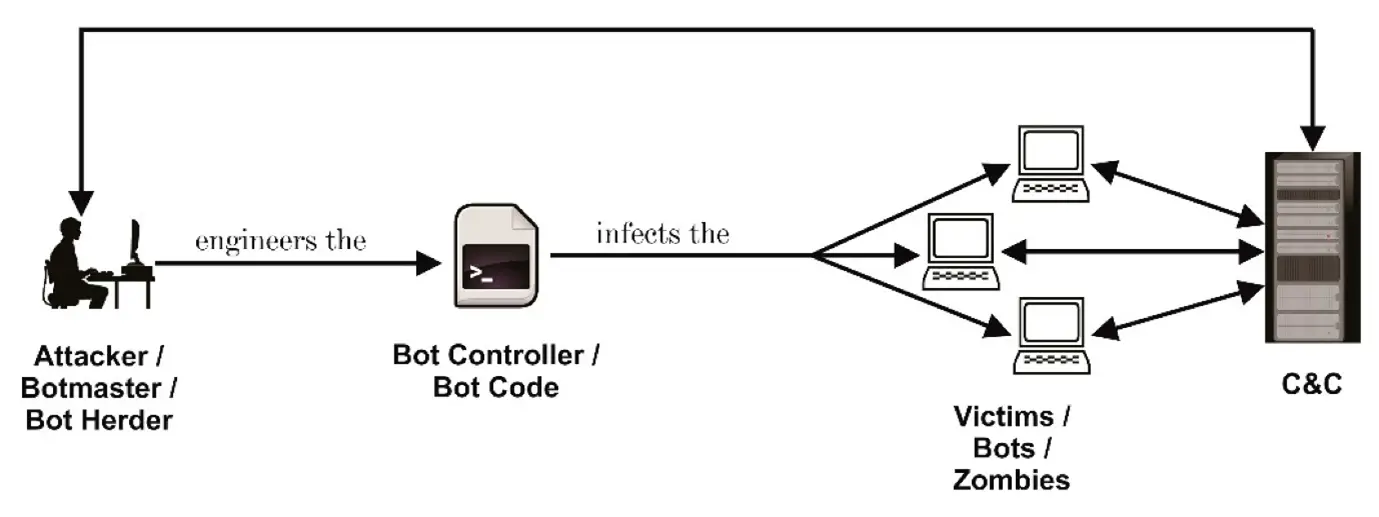
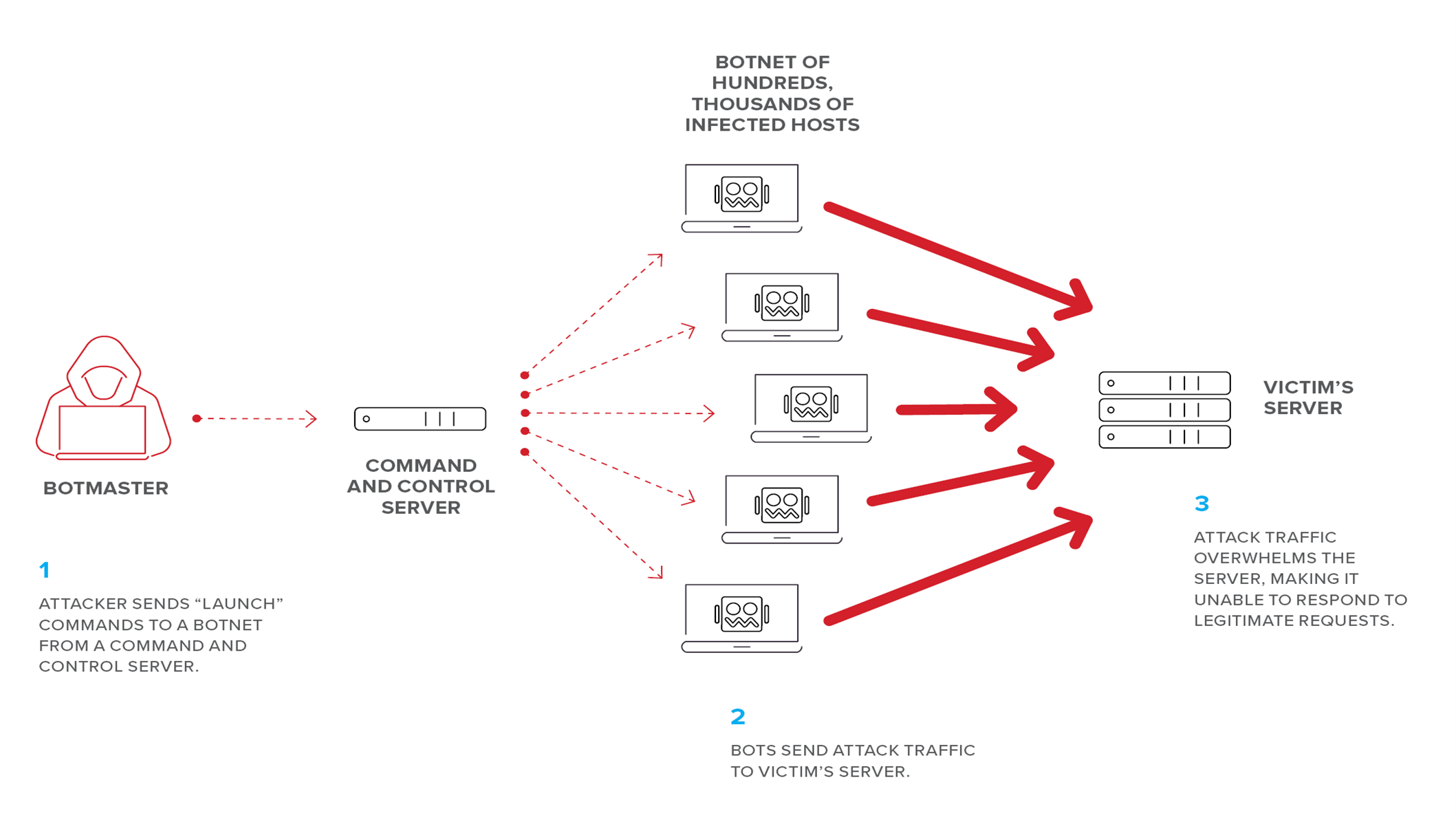
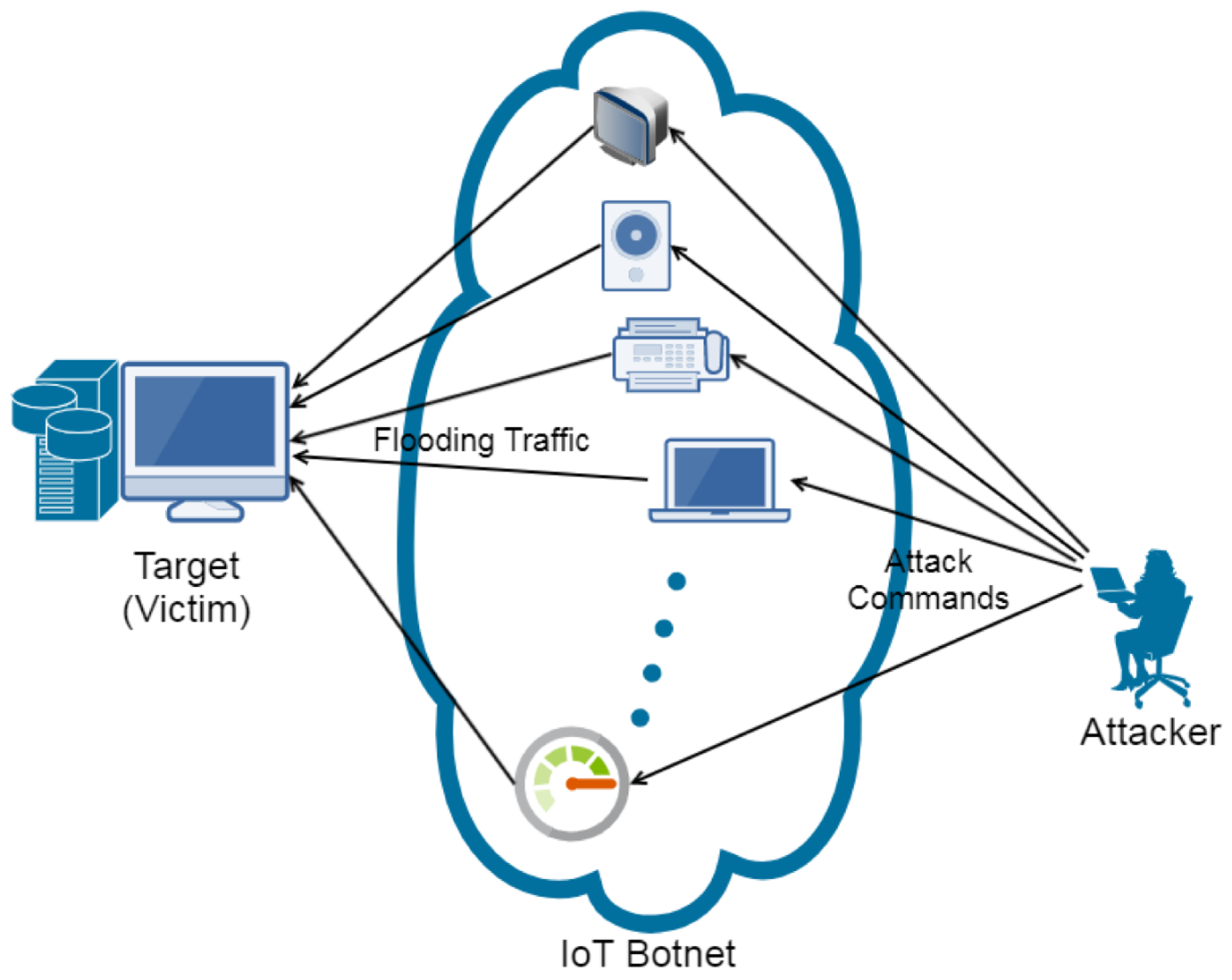
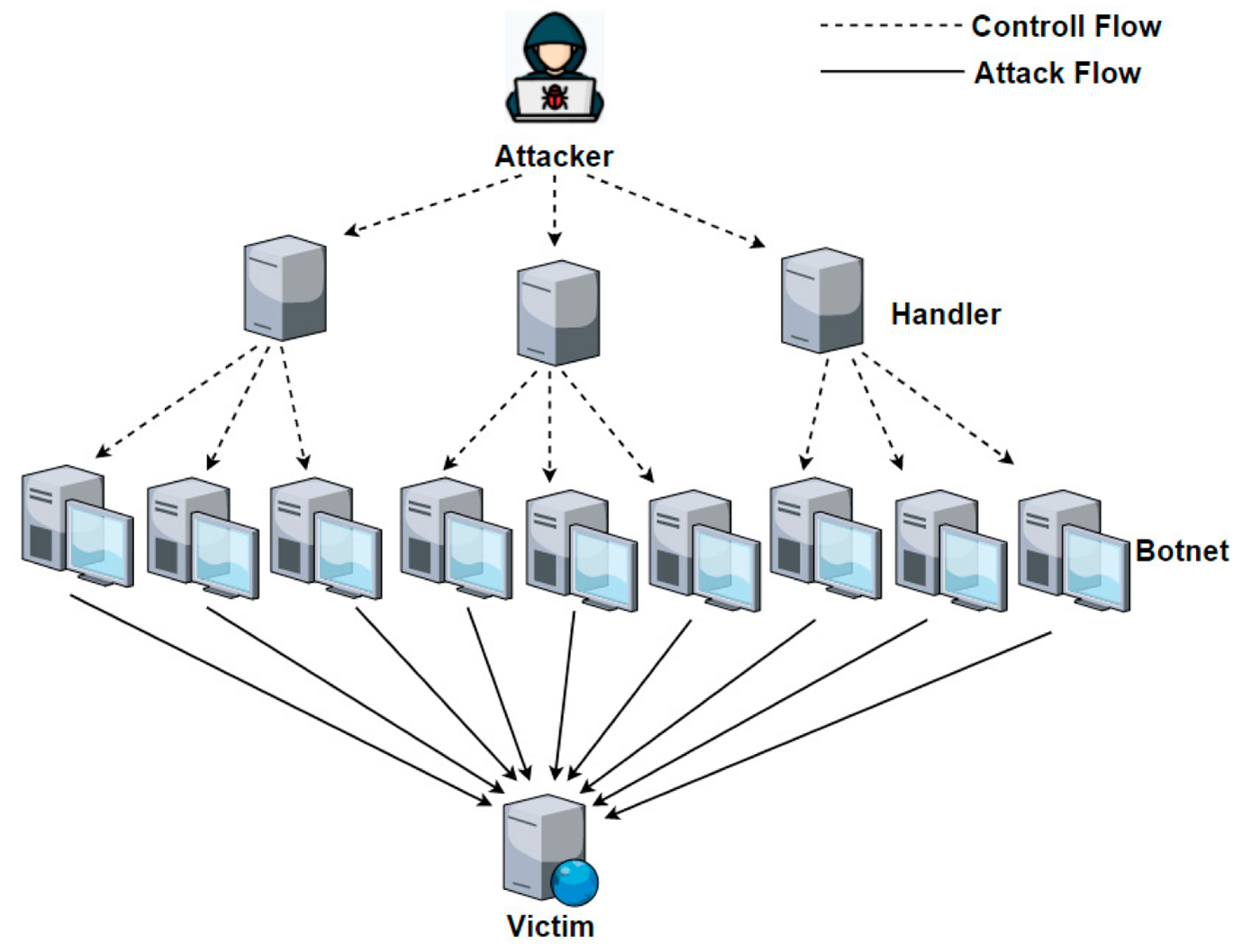
6. DDoS Botnets With Many Targets
A botnet is a collection of viruses computers hijacked online by software. Typically, machine owners aren’t aware that malicious software has been installed, which allows DDoS assaults can be launched by attackers using the remote control of their “zombie” machines. In addition to computers, botnets can also consist of other internet-connected devices (such as CCTV cameras, whose default passwords are frequently simple to guess) and hacked hosting settings. Hackers often share botnets or rent them out to other attackers. They can have many owners and use the same infected machines to launch attacks against several targets. Shared botnets are readily deployable by non-technical users and are available for hiring online.
7. Spoofed User-Agents
To ensure that webpages are correctly indexed by search engines, reliable bots, like “Googlebots,” are essential. Therefore, it’s crucial to avoid unintentionally blocking them. An attack method that is often employed is spoofing user agents. To avoid detection, the DDoS bots, in this instance, pose as “good” bots from trustworthy websites like Google or Yahoo. The bots can bypass low-level filters using this technique and then wreak havoc on the target systems.
8. Multiple Vector Assaults
DDoS attack operations have historically used a single attack type or vector. The use of various channels in DDoS assaults to take down a network or server is growing, nevertheless (s). They are known as multivector assaults and include a mix of the following: Volumetric assaults, state-exhaustion attacks, and application layer attacks are the three types of attacks. An attacker finds the multivector strategy particularly alluring since it has the potential to cause the most collateral damage to a company or organization. By focusing on a variety of network resources or employing one attack vector as a ruse while another, the more potent vector, is used as the primary weapon, these attacks boost their chances of success.
9. Mobile Device Assaults
Attacks have sharply increased as the market for mobile devices has become saturated. More internet capacity and faster connectivity offered by cellular networks have made it simpler for mobile devices to be taken over and unintentionally used to commit DDoS attacks. Malware can readily infiltrate smartphones and tablets without the owners’ knowledge because they are not immune to it. Combined with other similarly compromised mobile devices that are all secretly under the attacker’s control, they can be used to download malicious software and perform DDoS attacks. Compared to PCs, mobile devices offer less robust security measures. Most consumers don’t have any anti-virus software installed on their computers. On mobile devices, owners also download software more carelessly and without any security considerations. Because of this, rogue software can infiltrate mobile devices more easily.
10. Geographic Locations For Attack Origination
In areas with weak infrastructure, DDoS attacks are commonly directed through hacked hosting settings or internet-connected devices. Even if the attacks might have started in another nation, they spread to other places. These nations typically have less robust IT infrastructures, which explains why the computing resources there are more commonly employed in assaults.