In the day-to-day world, the IT threat is rapidly evolving. We can witness these in our everyday lives through malware attacks, viruses, rootkits, ransomware attacks, and other threats. As a result, the need for robust risk management has become a necessity. Organizations are often vulnerable to many vulnerabilities that can compromise their sensitive data, disrupt operations, harm their end-users, and damage their reputation. To avoid these challenges, IT risk management has become a critical discipline. Risk assessment tools have been developed to identify, analyze, and mitigate risks. This article will explore the top 10 assessment tools for IT risk management, their features, benefits, and significance in ensuring a secure IT environment.
1. NIST Cybersecurity Framework
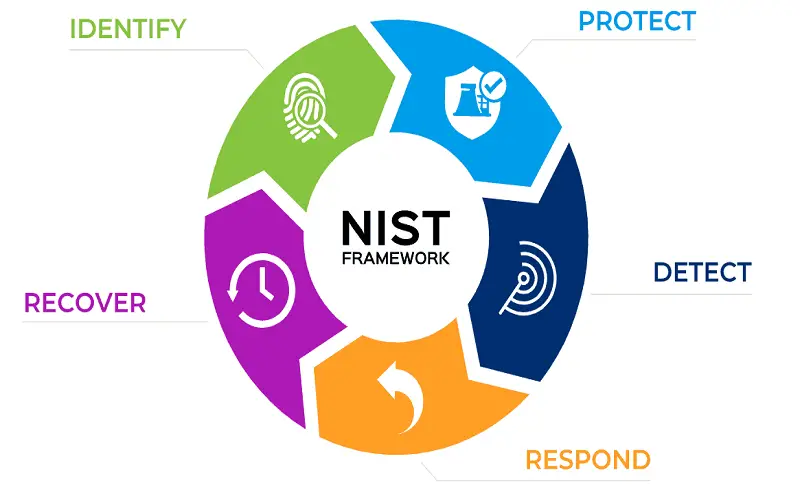
The NIST cybersecurity framework provides guidelines, best practices, and ways to manage and reduce IT risks. It offers a structural approach to assess an organization’s cybersecurity posture, identify gaps, and improve risk management. It is a self-assessment framework that helps to secure an organization’s infrastructure. The framework is intended for all organizations regardless of sector or size. To keep things running smoothly and deal with issues effectively, the framework has five important functions: Identify, Protect, Detect, Respond, and Recover. These functions work together. When considered together, it provides a broad view of the lifecycle for managing cybersecurity risks over time. Using the NIST Cybersecurity Framework, organizations can proactively manage IT risks, improve their current cybersecurity conditions, and establish a systematic risk assessment and mitigation.
2. OSSEC
OSSEC is a comprehensive open-source host-based intrusion detection system that combines HIDS, logs monitoring, and SIM/SIEM for real-time log analysis, intrusion detection, and alerting. Its key benefits are multi-platform, Real-time alerts, centralized management, and Agent and agentless monitoring. You can Integrate OSSEC with your current infrastructure without any issues. It provides file integrity checking, log monitoring, rootkit detection, and Active responses. It can detect and mitigate threats in real time, assisting with incident response. It can help an organization or an end user to monitor, assess, and manage IT risks.

3. Suricata
This open-source network intrusion detection and prevention system offers real-time traffic analysis, content inspection, and signature-based detection. It helps monitor and manage the incoming risks to the infrastructure by analyzing requests coming in and out of the infrastructure network. It can monitor small as well as extensive networks like an organization. Using Suricata in an organization’s IT risk management strategy can improve the ability to identify and mitigate threats, reducing the chance of a successful cyber-attack on the infrastructure. It captures and logs network traffic, which helps in network forensics after potential security incidents.

4. AlienVault OSSIM
AlienVault OSSIM is an open-source security information and event management (SIEM) tool that provides features such as asset discovery, vulnerability assessment, intrusion detection, behavioral monitoring, and SIEM correlation. An organization can improve its IT risk management, threat detection, and real-time monitoring by using OSSIM. It can perform a complete vulnerability assessment on a network to find its weaknesses and vulnerabilities. It can monitor a network to detect incoming IT threats and an event monitoring system that logs data and provides security visibility of the infrastructure to the organization. Organizations can use OSSIM to reduce IT risks and improve risk management, threat intelligence, and network monitoring in real-time, which leads to a secure and safe IT environment.

5. QRadar
QRader is a suite of tools developed by IBM Security. This is a new solution that helps security analysts work better and faster when dealing with security threats. It improves the experience by making it easier to detect and respond to incidents. It also consumes the power of A. I to improve the productivity of a security analyst. It offers integrated products like log management, SIEM, and SOAR with a familiar user Interface for ease of use. It provides benefits like Open platform and prebuild integration, cloud delivery, speed, and scalability. The key features of QRader are threat investigation, data collection, detection and response center, and unified user experience. An organization can improve its IT risk management, detection and response, and overall security posture.

6. Open FAIR
Open FAIR (Factor Analysis and Information Risk) provides a systematic way to analyze and quantify IT risk to an organization. It helps in risk assessments to comply with other industry and regulatory standards, frameworks & methodologies to build consistent and defensible risk management. It can help in risk identification, risk assessment, factor Analysis, risk quantification, risk treatment, Decision Support, and Communication and Reporting. An organization can understand its risk exposure, make good decisions about IT risk treatment, and allocate resources that suit its goals and risk tolerance. It enhances the organization’s overall IT risk management and risk assessment.

7. ZenGRC
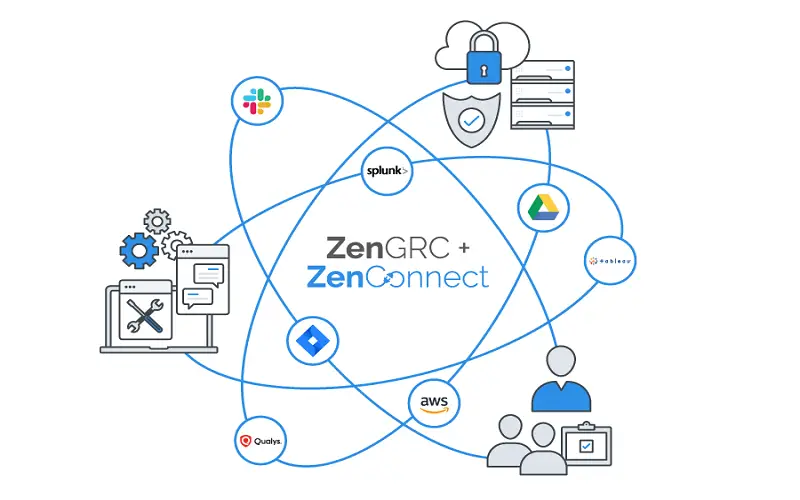
ZenGRC is a cloud-based platform that helps streamline compliance and risk management processes by offering centralized tracking of risks, controls, and assessments. It serves all sizes of industries regardless of the sectors. The primary features of ZenGRC are audit management, compliance management, contract and policy management, risk assessment, and reporting. It helps organizations with internal infrastructure auditing, which helps detect internal risks. It also automates the process of audit evidence collection and routine compliance and assists with new compliance programs. It provides various features for reducing IT risks, like role-based access, project management, import and export of resources, and a dashboard. ZenGRC can integrate with essential industry tools like JIRA, Google Drive, OneLogin, Active Directory, and more. It helps in improving security throughout the infrastructure and managing IT risks.
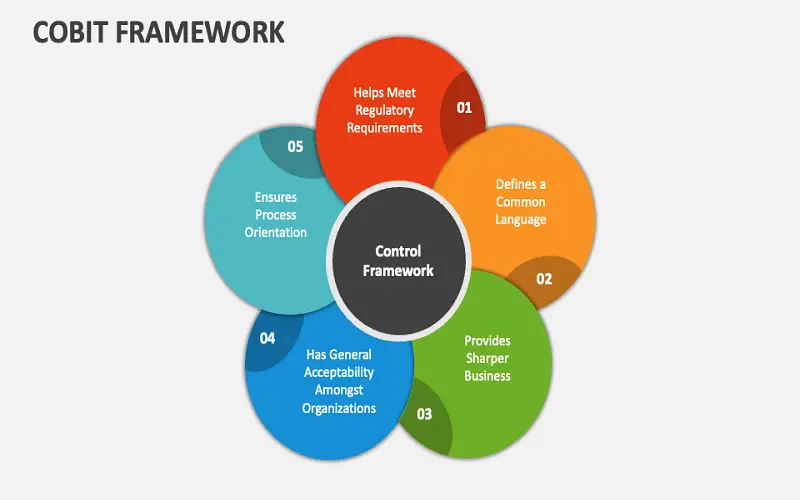
8. COBIT (Capability Maturity Model Integration)
COBIT is a framework that provides guidelines and control objectives for IT risk management for organizations. It offers effective administration of information and technology. The integration of COBIT is flexible and for all sizes of infrastructure. It guides you to integrate the industry standards, guidelines, regulations, and best practices according to your enterprise. It plays a crucial role in addressing the risks through identification, assessment, control objectives, control implementation, monitoring and measure, and risk reporting. It provides a systematic approach to IT risk management for organizations.
9. ISO 27001
ISO 27001 was created by the International Organization for Standardization (ISO), provides a model for implementing, operating, monitoring, reviewing, maintaining & improving the information security infrastructure of an organization. It helps in management responsibility, internal audits, continual improvement, and corrective and preventive actions. To protect their confidential information and comply with legal requirements, companies can take measures to ensure its safety. ISO 27001 is divided into 14 phases that help organizations develop and maintain a secure information security and management system. It plays an essential role in IT risk management by working from the top to bottom of an infrastructure.
10. Wazuh
Wazuh is a SIEM (security information and event management system) that provides features like system monitoring, threat detection, vulnerability assessment, security operations, cloud security, and intrusion detection in real-time. It can monitor desktops, laptops, and mobile devices. It is used in any industry regardless of scale and sector. It protects an organization by continuous monitoring and threat detection. It can deploy on Windows, Linux, the cloud, and most devices. The key features of wazuh are early threat detection, risk assessment, incident response, and compliance. Organizations can use wazuh to enhance their IT risk management strategies and improve their ability to monitor, detect, and respond to potential security risks.