1. Egress Email Encryption
Egress Email provides full audit logs and allows give up customers to revoke admission to introduced emails, supporting to prevent security breaches. The carrier makes it smooth for Office 365 users to encrypt emails and ship and receive large encrypted documents without leaving their e-mail inbox. Users are also capable of upload watermarks with the recipient’s email address and restrict printing to prevent information leakage.
2. Virtru
Virtru permits cease users to encrypt emails immediately from their electronic mail clients. From here, they also can see who has opened emails they’ve sent, revoke access to the e-mail they have got sent, control e-mail forwarding, or even add watermarks to encrypted attachments. Virtru deploys quickly and offers admins the capacity to see where emails and files are shared. Admins can also set, put in force, and configure security rules throughout the corporation from the admin dashboard.
3. Zix
Zix implements content filters, which mechanically encrypt emails.Zix to ship an encrypted e-mail; users virtually create a message and hit send. When you open the encrypted email, recipients genuinely open the encrypted e-mail like an ordinary email.
4. Mimecast
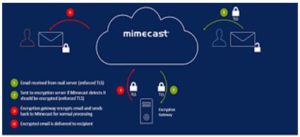
Mimecast offers a range of stop user controls. Mimecast consists of being capable of seeing when an e-mail has been read and putting regulations. End users can also revoke admission to if an e-mail was sent accidentally. All of those controls are reachable from the users’ current electronic mail service, making them smooth to use.
5. Proofpoint
Proofpoint Essentials permits IT, teams, to create filters that robotically perceive outbound emails that ought to be encrypted. End customers can also manually encrypt emails they are sending, to ensure that their emails are secure if needed, with an Outlook plug-in for PC customers. Recipients can examine encrypted emails using the Proofpoint stable internet portal, from where they also can reply with an encrypted response.
6. EchoworxOneWorld Encryption
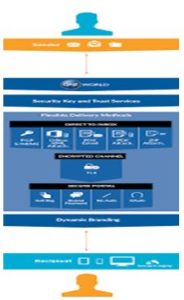
Echoworx offer brilliant get entry to and audit reports, so that you have visibility over who is gaining access to encrypted e-mail. They also offer additional capabilities, for example, large record encryption.
Echoworx gives a large number of features and policies.
7. Cisco Registered Envelope
Cisco allows customers to govern the ability to cease users to forward and respond to emails. These controls are available with the users’ regular e-mail client, making them clean to use. Admins get access to reports, detailing while those controls were used. Customers like this service for the variety of quit person controls on offer.
8. PreVeil’s enterprise encryptions
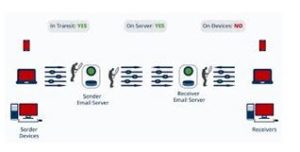
PreVeil’s enterprise encryptions solution permits IT administrators to create, change, and delete users and groups, also, to set organization-wide statistics and recuperation policies. Device management controls let admins disable misplaced or stolen devices quickly. PreVeil’s Approval Group technology allows in privileged activities handiest after cryptographic approval from a hard and fast of predetermined administrators or leaders.
9. DeliverySlip
DeliverySlip provides a sophisticated manage panel to give up customers to manipulate their encrypted emails. With DeliverySlip, users can use a song while a message has been received, read, answered to, or forwarded. End users can also remember, even after they are open. They can manipulate whether emails can speak back to,or maximum security, users can set passwords for emails, to make sure that best the meant recipient can open them.
10.) Microsoft Office Message Encryption
Microsoft Office Message Encryption is straightforward to use inside O365. It gives some useful features; customers can send stable email both internally and externally. It’s also very reasonably-priced and smooth to implement. Admins can create custom policies.