If it needs to be configured correctly and used safely, Bluetooth poses several security issues, although it makes short-range wireless data transfers incredibly convenient.
1. The Loss Of Personal Data
An adversary can take advantage of existing Bluetooth vulnerabilities to steal personal and confidential data such as contacts, SMS (text messages sent via the Short Message Service), call logs, and other similar information over Bluetooth and use it for malicious purposes.

2. Hijacking
An adversary could entirely take control of a device using Bluetooth and carry out their actions independently of the user. This includes activities such as calling, recording conversations that are already in progress, and similar activities.
3. Sending SMS
An adversary can utilize a Bluetooth device that has been compromised to send SMS messages to any individual of their choosing while concealing their own identity. This is done for terrorist activity in the majority of cases.

4. Using Airtime
An attacker could cause significant financial damage to a victim by making international phone calls from a device that has been compromised using Bluetooth.

5. Malicious Code
An adversary can transmit malware to a device over Bluetooth, permanently infect the device and change, steal, or delete sensitive user data stored on the device.

6. Inherent Vulnerabilities
Flaws intrinsic to the Bluetooth stack It’s possible that the Bluetooth stack has specific inherent vulnerabilities that could be exploited.
7. Bluejacking
Bluejacking is forcibly transmitting undesired messages to the victim over Bluetooth. This technique is known as “jacking.” It is very similar to sending unsolicited emails. Even if it is not very dangerous, it might be an annoyance to the person who is affected by it. It is frequently employed in the practice of aggressive marketing.
8. Bluesniff
It is a tool on Linux that is used for Bluetooth wardriving. Bluesniff’s full name is Bluesniff, and it is handy for discovering Bluetooth devices, both those that are hidden and those that are discoverable.
9. Bluesmacking
Bluesmacking is a distributed denial of service attack that can be carried out over Bluetooth. In this attack, an overly large packet is transmitted to the victim’s device through Bluetooth, which ultimately makes the device unusable.

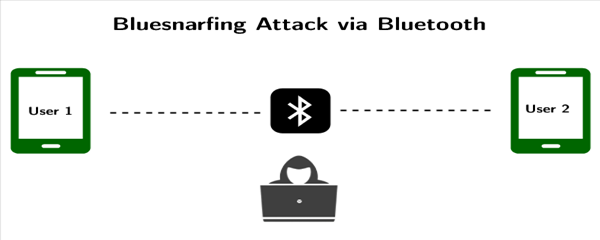
10. Bluesnarfing
Bluesnarfing is an attack that uses a flaw in the Bluetooth stack to get unauthorized access to sensitive data stored on the victim’s device. The attacker can access the victim’s address book and calendar entries.