In a Cyberattack, the attacker targets the computer or computer network of the victim in an attempt to destroy, alter, or steal any critical data present in it. The attack can be conducted by any individual or a process developed by any individual that can gain unauthorized access to the victim’s device. These types of attacks can be operated either by an individual or by groups. Mostly the main motive of such cyber-attacks is to get the data from the target system of an individual or management. The use of malicious code in cyberattacks makes changes in the computer logic or code. This further leads to compromise of data and cybercrimes such as information and identity theft.
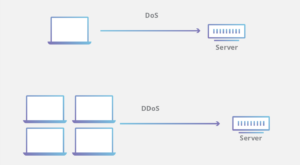
1. Denial-of-service (DoS) and Distributed Denial-of-service (DDoS) Attack:
A DoS attack may cause a significant amount of loss to a company. In this attack, the attacker targets the systems, servers, and many devices connected to the network. All the targeted devices are flooded with fake traffic so that their resources are exhausted. While in a DDoS attack the attacker uses several compromised devices to launch the attack.
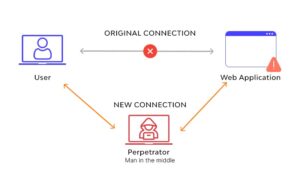
2. Man-in-the-middle (MitM) Attack:
A man-in-the-middle attack occurs when a hacker intercepts a communication between the two communicating hosts i.e. the client and the server. Different MitM techniques involve Sniffing, Packet Injection, Session Hijacking, SSL Striping, etc. Best practices to prevent these kinds of attacks involve using strong encryption mechanisms such as WEP/WAP on access points, changing the default router login credentials, using of Virtual Private Network (VPN), communicating over HTTPS, etc.
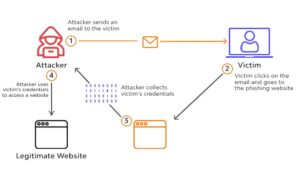
3. Phishing Attacks:
Phishing attacks usually involve sending fraudulent communications that seem to come from a legitimate source. Attackers use various phishing methods such as email phishing, phishing over phone calls to get victims sensitive data such as credit card, login information, or even try to install malware on their system. Protection against these attacks involves user education where employees of the organizations are taught to identify phishing emails, an inspection of URLs, etc.
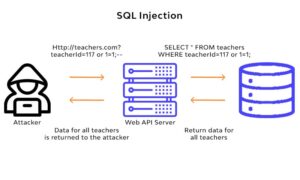
4. SQL Injection Attack:
SQL injection is a vulnerability in the websites where the input field such as textbox is vulnerable and the attacker inserts various SQL queries to exploit the vulnerability. It allows the attacker to get access to sensitive data such as emails, passwords, contact details, etc. In most cases, the attacker can even modify and delete the data. There are several effective ways to prevent SQLi attacks such as input validation (writing code that can identify illegitimate user inputs), applying web application firewalls (WAF).
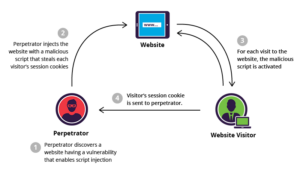
5. Cross Site Scripting Attack:
It is also known as an XSS attack. It is also an attack where the malicious code is injected into a web application. The attacker finds a flaw in the website and exploits it mostly using client-side JavaScript malicious code. It also comes under the OWASP Top 10 vulnerabilities which makes it a serious security concern. These attacks can be prevented by using secure coding practices and by ensuring that all the input by the user such as user forms, search fields, or submission requests is escaped properly while developing.
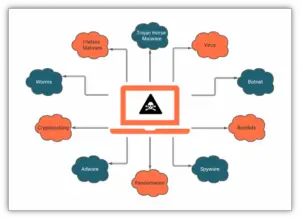
6. Malware Attack:
Malware is malicious software created by an attacker when executed performs unauthorized actions on the victim’s device. There are different types of malware such as a virus (a payload that performs malicious actions on execution), Trojan horse (, worms, ransomware (installs itself onto victim’s machine, encrypts their files, and then turns around and demands a ransom), adware (programs that push unwanted advertisement at users), spyware (program installed on your device without victim’s knowledge and captures personal data and sends to the attacker). To be safe from these kinds of attacks never click on an unknown link, use antivirus and firewall.
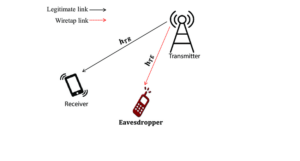
7. Eavesdropping Attack:
An eavesdropping attack involves secretly listening to someone else’s private conversation. It is also known as sniffing over networks. It involves VoIP interception due to the lack of encryption. The best way to prevent eavesdropping is to use 256-bit encryption to encrypt data in transmission, spread awareness, update and patch software.
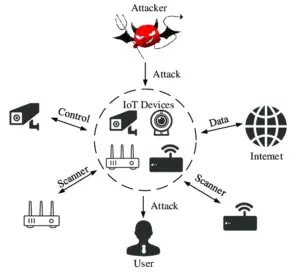
8. IoT Attack:
Currently, IoT devices are generally less secure than other modern devices so there are many loopholes in the IoT devices as compared to the other technologies. Hackers target many security systems, medical devices, and other smart home devices. They may also launch a large-scale DDoS attack. To prevent these attacks all the data gathered should be stored with proper security, each device should be configured securely.
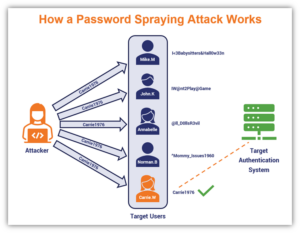
9. Password Attack:
A password attack occurs when a hacker tries to steal your password. It is the most common attack and also the severity is high because the attacker can perform multiple actions with the compromised credentials of the user. Various types of password attacks involve brute-force attacks, key logger attacks, dictionary attacks, traffic interception, etc. The best way to prevent these attacks is to create a password that contains a combination of alphanumeric phrases and special characters.
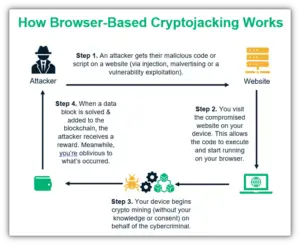
10. Crypto-jacking Attack:
Crypto-jacking is a type of cyberattack where the attackers get unauthorized access to the user’s device such as computers, tablets, smartphones, and servers and they mine cryptocurrencies. The main motive is to gain profit but without the acknowledgment of the victim. Criminals usually hack into the devices by installing crypto-jacking software. The software runs in the background and mines cryptocurrencies or steals from crypto-wallets. There may be lag or slow device performance on the victim’s device. Protection involves anti-crypto mining extensions on browsers, educating about the attacks, keep the firewall and antivirus updated.