Since most of our everyday tasks and activities are automated and accessible via the Internet, we must exercise the same level of vigilance that we did when we were younger, such as crossing the street whenever we spotted a strange stranger. This precaution is even more necessary now that some alarming data have emerged, according to which about one-third of all computers worldwide are infected with malware.
1. Computer Virus
Each of us has heard about them and is afraid of them. Computer viruses are one of the most prevalent network dangers to cybersecurity for regular Internet users. According to statistics, almost 33% of home PCs have malware installed, more than half of which are viruses. Software programs called computer viruses are designed to spread from one machine to another. They’re frequently obtained from specific websites or provided as email attachments to infect your computer and the computers on your contact list using systems on your network. Viruses have been known to wipe everything on your hard drive, corrupt and steal data from your computer, including personal information like passwords, disable your security settings, and send spam.

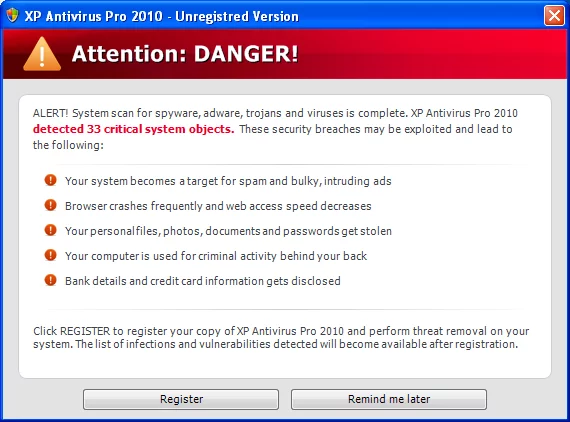
2. Rogue Security Software
Scammers have discovered a new method for committing Internet fraud by capitalizing on people’s fear of computer viruses. Rogue security software is malicious software that tricks users into thinking that their security measures are out-of-date, that they have network security difficulties, or that they have a computer virus on their machine. They then make the option to install or update security settings for users. Either they’ll demand you purchase a tool or download their program to get rid of the purported viruses. In both situations, your computer gets malware placed on it.
3. Trojan Horse
A “Trojan horse” is a metaphor for deceiving someone into allowing an assailant into a securely guarded place. A Trojan horse, sometimes known as “Trojan,” is a harmful piece of attacking code or software that deceives people into running it freely by disguising itself as a trustworthy application. It has a very similar meaning in computing. They frequently spread by email; they could look like emails from people you know, but as soon as you click on the email’s attachment, malware is quickly downloaded to your machine. Additionally, when you click on a deceptive advertisement, Trojans propagate. Once on your computer, a Trojan horse can steal any sensitive information you may have stored there, take control of your webcam, and log keystrokes to capture your passwords.

4. Adware And Spyware
Any software that tracks your browsing behavior and uses that information to serve you pop-ups and advertising is referred to as “adware.” Adware is software that gathers data with your permission and can even be a good source of cash for businesses offering users free trials of their software in exchange for showing advertising. Adware clauses are frequently concealed in linked User Agreement documents, but you may check for them by carefully reviewing everything you agree to when installing software. Only those pop-ups indicate the presence of adware on your computer, which can occasionally impede the speed of your computer’s processor and internet connection. Adware is regarded as malicious when it is downloaded without permission. While spyware is installed on your computer without your awareness, it functions similarly to adware. Because of the significant risk of identity theft may contain keyloggers that capture personal data, including email addresses, passwords, and even credit card numbers.
5. Computer Worm
Computer worms are malware programs that duplicate quickly and spread from one computer to another. A worm spreads by sending itself to every contact on an infected computer, then instantly to the contacts on the other systems. It’s interesting to note that not all worms are created to be harmful; others are only meant to propagate. Exploiting software flaws is another standard method of worm transmission. Computer worms are among the most frequent hazards to computer networks, even though we don’t hear much about them these days.

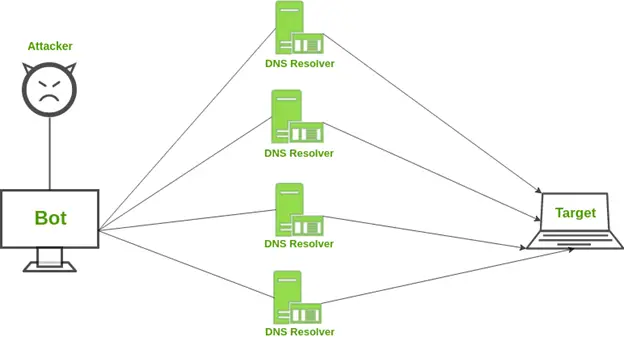
6. DOS And DDOS Attack
Have you ever found yourself impatiently awaiting a product’s online debut when you’re excited to buy it? You keep refreshing the page while you wait for the product to go live. When you hit F5 for the final time, an error message reads, “Service Unavailable.” There must be a burden on the server! Sometimes, after a news story breaks, there are instances like these where a website’s server becomes overburdened with traffic and abruptly fails. However, this is more frequently what happens to a website during a DoS attack, also known as a denial-of-service attack, when attackers maliciously overload a website with traffic. A website cannot offer its content to users when it receives excessive traffic. By flooding a website with packets and preventing authorized users from seeing its content, a single machine and its internet connection carry out a DoS assault. You can no longer overload a server with just one additional server or PC. It was rare in previous years, if at all, due to protocol issues. While a distributed denial-of-service assault is comparable to a denial-of-service attack (DoS), it is more severe. A DDoS attack is brutal to defend against. It is launched from several computers, and the number of machines involved may be in the thousands or the millions. Not all of those computers are likely attackers, so malware compromises them and adds them to the attacker’s network. “botnet” refers to a network of infected computers found worldwide. A DDoS assault is significantly more challenging for the victim to find and defend against since it originates from so many IP addresses simultaneously.
7. Phishing
Phishing is a technique of social engineering used to acquire sensitive information, including passwords, usernames, and credit card numbers. Attacks frequently take the form of phishing emails or instant chats that are made to look official. The email recipient is then duped into clicking a malicious link, which causes malware to be installed on their computer. It can also get your personal information by sending you an email that purports to be from a bank and requests that you confirm your identity by providing your data.

8. Rootkit
A rootkit is a group of software programs that allow remote control and administrative access to a computer or network of computers. The rootkit has keyloggers, password stealers, and antivirus disablers, and once it has remote access, it may carry out a variety of evil deeds. When you allow a legitimate piece of software to modify your operating system, a rootkit hides inside it. It installs itself on your computer, waiting for a hacker to activate it. Phishing emails, infected links, and files and downloading software from dubious websites are additional methods of rootkit dissemination.
9. SQL Injection Attack
We are aware that SQL is used by many servers that store data for websites nowadays. SQL injection attacks have emerged as network security threats have developed along with technology. SQL injection attacks target data-driven applications by taking advantage of security flaws in the application’s code. They can even go as far as to cancel website transactions using malicious code to obtain sensitive data, alter it, or even destroy it. It has quickly elevated to the top of the riskiest privacy concerns for data security.

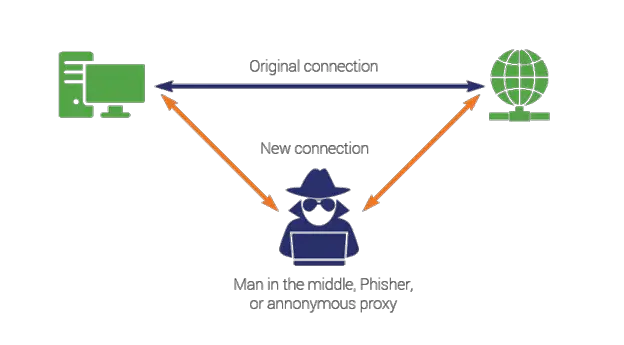
10. MIM Attacks
Cybersecurity man-in-the-middle attacks allow the attacker to eavesdrop on conversations between two targets. It is capable of listening in on a conversation that ought to be private in most circumstances. As an illustration, a man-in-the-middle assault occurs when the attacker wishes to eavesdrop on a conversation between A and B. When person A gives person B their public key, the attacker intercepts it and sends person B a forged message that purports to be from person A but contains the attacker’s public key. B encrypts the message using the attacker’s public key and sends it back to the attacker, believing it to be from person A. However, the attacker again intercepts this message, opens it with their private key, potentially modifies it, and re-encrypts it using the public key that was initially provided by person A. Once more, when the message is returned to person A, they mistakenly believe it is from person B. In this fashion, we have an attacker in the middle who eavesdrops on the two targets’ conversation.