As cyber threats become increasingly sophisticated, organizations must implement robust cybersecurity awareness and skills training programs. Immersive cyber ranges provide hyper-realistic virtual environments that mimic an enterprise network, enabling cybersecurity professionals to hone technical skills through hands-on simulations of real-world attacks and defense scenarios across IT infrastructure and critical business systems. Configurable cyber ranges empower infosec teams to customize training programs to their unique risk profiles. I outline the top 10 cyber range platforms that offer leading-edge simulations for cybersecurity training across IT, ICS/OT, cloud, and other environments. The platforms provide structured learning paths that build job-relevant cyber skills through interactive hands-on labs as well as competitive team exercises that test crisis response capabilities. DBAs need to leverage cyber ranges as part of mandatory ongoing education across security, infrastructure, and development teams to counter rapidly evolving threats.
1. EdApp
EdApp delivers one of the most flexible and easy-to-use cyber range platforms with broad environment support spanning IT, OT, ICS, and cloud. The cyber range includes pre-built labs and simulations for training cyber skills through realistic attack-defense scenarios. Learners can hone skills in vulnerability assessment, penetration testing, digital forensics, malware analysis, and incident response across diverse systems from Windows and Linux servers to critical infrastructure. As part of regular reporting, EdApp provides actionable insights into individual and team proficiency levels across different simulated scenarios to pinpoint specific capability gaps. This enables CISOs to tailor training programs to build targeted strengths.

2. Infosec
The Infosec cyber range provides over 850 hands-on cybersecurity labs that progress in difficulty from beginner to advanced skills training. Learners can develop technical expertise across penetration testing, ethical hacking, malware analysis, forensics, cryptography, and other domains through self-paced interactive labs modeled after real-world systems and threats. Infosec Skills cyber ranges also include competitive team exercises called CyberSparks that require participants to apply their skills collaboratively to investigate and respond to unfolding cyber-attack scenarios in a race against the clock. CyberSparks sharpen skills in threat hunting, monitoring, analysis, containment, and remediation while testing crisis response coordination capabilities. Infosec provides dedicated support to help organizations set up and facilitate these team crisis simulations.

3. Coursera
Coursera partners with leading universities and companies to deliver a wide catalog of hands-on cybersecurity courses, Professional Certificates, and master track programs. Learners can develop in-demand skills through real-world projects and simulations on industry-relevant tools and systems provided through Coursera Labs and Projects. For example, a Google IT Automation with Python Professional Certificate program includes a capstone project where learners utilize Ansible and Kubernetes to automate the deployment, management, and monitoring of a cluster of Linux containers in the cloud to run a simple web application. Such applied learning develops expertise in infrastructure automation and cloud-native development while testing abilities to troubleshoot issues across systems.

4. FutureLearn
FutureLearn partners with top schools like Deakin University, Chalmers University of Technology, and The Open University as well as technology leaders like Amazon Web Services, IBM & Cisco to deliver free online introductions to cybersecurity programs. Learners can explore beginner courses to gauge interest and aptitude before pursuing advanced technical programs. For example, an Introduction to Cyber Security course from Deakin University provides a solid base by building foundational knowledge covering key concepts, systems, and trends in the cybersecurity landscape. This self-paced course takes about 24 hours over 4 weeks. Learners who complete optional assessments can earn a certificate to validate basic security skills and knowledge.

5. SafeTitan
SafeTitan focuses exclusively on cyber safety educational content for schools and youth. The video-based lessons coached by expert instructors overlay game interfaces to promote engagement. Students can practice skills like cracking passwords, identifying malware, and responding to cyberbullying scenarios in the integrated simulation environment. SafeTitan offers flexible implementation whether as a mandatory course, integrated curriculum, or self-driven training. The central dashboard allows teachers visibility into proficiency benchmarks across cohorts. Given constantly evolving digital threats, the interactive modules prepare the next generation to exercise caution and responsibility early on.

6. Hook Security
The cloud-hosted Hook Security cyber range platform emphasizes offensive security training via labs focused on reconnaissance, weaponization, delivery, exploitation, installation, command & control, and actions on objectives. While Hook Security caters extensively to red teams with attack simulations, blue teams can benefit by strengthening vulnerability assessment and hardening skills. The technology-agnostic scenarios provide flexibility for Windows, Linux, or hybrid environments. Hook Security also offers customized private platforms for organizations to configure proprietary network topologies, sensitive data, and staged adversarial access. The subscriptions are moderately priced for individuals although organizational pricing necessitates further discussion.

7. KnowBe4
The KnowBe4 platform focuses strongly on security awareness powered by machine learning to continually test employee responses against evolving phishing and social engineering schemes. The fully managed service provides setup assistance, content building, a phishing simulator, and detailed analytics on susceptibility rates. KnowBe4 dedicates resources to keep curating clever phishing templates mapped to timely issues like crypto fraud. For technology leaders overseeing non-technical departments, investing in KnowBe4 yields multi-fold returns by significantly improving human firewall resilience. Budgets need to account for sizable licensing costs although organizations can start with monthly subscriptions.

8. Phished
Phished offers free cybersecurity awareness games targeted at regular employees to recognize phishing attempts and minimize security incidents. The platform catalog incorporates browser plugins, mobile apps, and VR training targeted at varying audience preferences. Phished partners with IT teams to customize simulations mirroring actual threats observed at the organization. The automated training workflow includes single sign-on integration, user management, simulation builder, delivery, and reporting. The cost advantage and innovative delivery formats make Phished a compelling value addition for most organizations although tiny startups may benefit from more handholding.

9. Ironscales
The Ironscales platform focuses on email and cloud application security powered by AI-based behavioral analysis to identify complex social engineering attacks. Dynamic classifiers profile typical communication and trigger alerts for anomalies in patterns. The self-learning algorithms help discern malicious emails from unusual but legitimate messages to minimize false positives. Ironscales offers comprehensive filtering, detection, response and awareness capabilities for organizations to securely embrace cloud communication channels. While the tool proves worthwhile for enterprise-grade mail environments and shared drives, small businesses may find the feature set overwhelming.

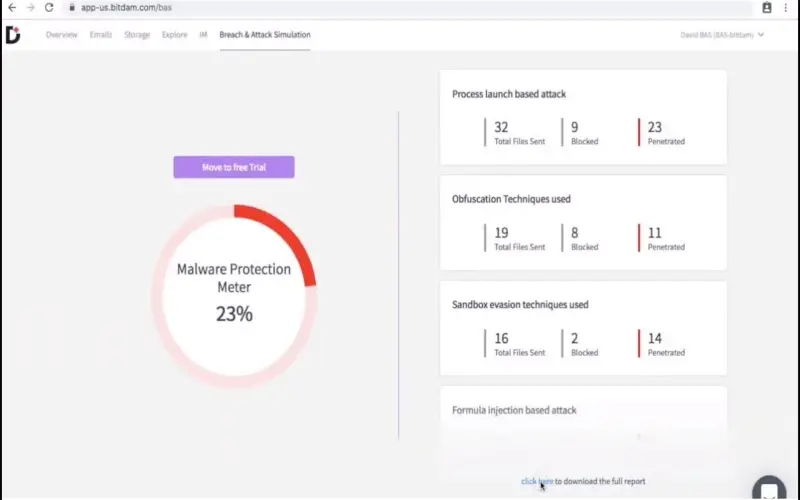
10. BitDam
Israel-based BitDam provides advanced threat protection for enterprise mail systems via deep content inspection. The platform detects weaponized content including malicious attachments and embedded links through algorithmic processing and machine learning. BitDam offerings are available as cloud-based services or on-premise solutions depending on infrastructure preferences. Automated remediation and detailed forensics improve SOC efficiency. BitDam consolidates core capabilities for mail threat defense albeit at relatively premium pricing, hence prudent evaluation of specific organizational requirements and returns on investment bears importance.