Tools for hunting threats function much like computer virus detectors, they look for potential threats in the programs and network of your computer. They accomplish this by analyzing data, observing behavior, and consulting with other human specialists. These devices can establish their guidelines and alert you to anything they find suspicious and untracked. To keep you safe from online threats and attacks, they provide their statistics for thread measures. Consider them the superheroes of computer security they constantly watch out for the safety and security of your private digital data and information. Now let’s look at the Top 10 Cybersecurity threat-hunting tools.
1. SolarWinds Security Event Manager
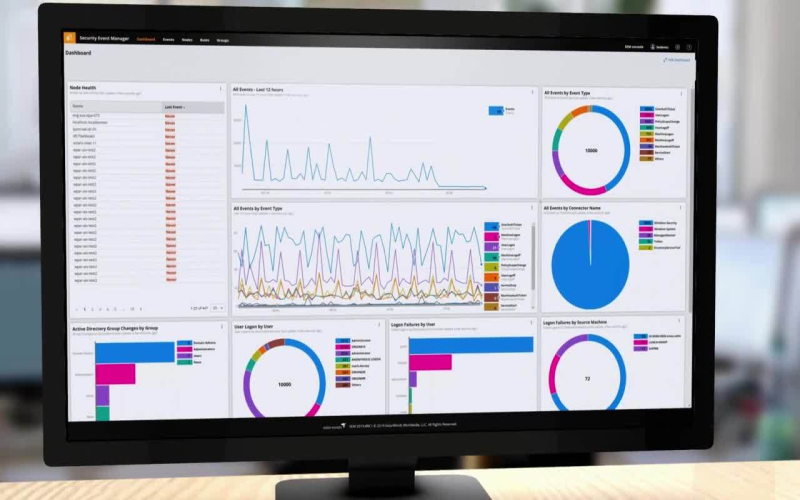
One great tool for keeping your computer secure is SolarWinds Security Event Manager. It recognizes malicious activity in real time, gathers relevant data, employs rules to detect issues, automatically prevents malicious activity, verifies that all operations meet the rules and regulations of the organization, allows customization of the interface, and provides threat intelligence. You can test it and find if, it’s the right fit for you by taking a 30-day free trial. For your data, it functions as a watchdog, constantly monitoring and safeguarding your virtual environment.
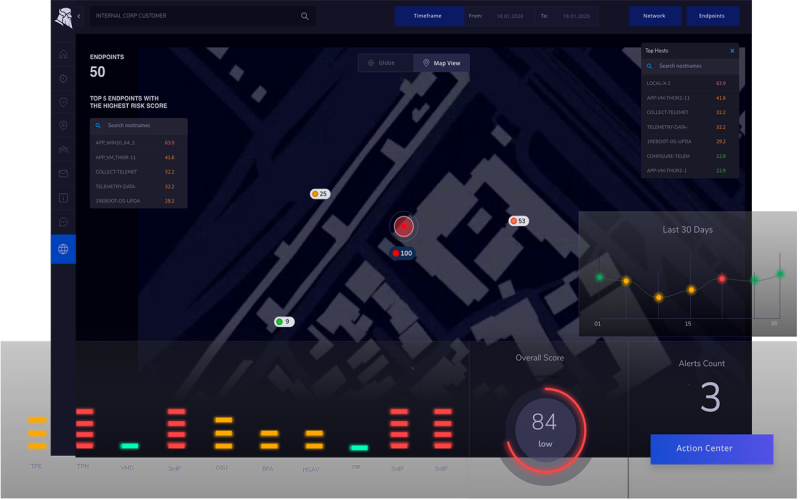
2. Heimdal Threat Hunting and Action Center
Heimdal Threat Hunting and Action Center is a brilliant tool that stops malicious software from running on computers when used with other Heimdal protection products. You can test out the demo by clicking on the link. This electronic device is incredible. It guards against malware by scanning the computer for it. With a single click, you may resolve problems in real time. Like a super team of computer security, it always keeps an eye on everything. If you want to learn more, check it out with a demo.
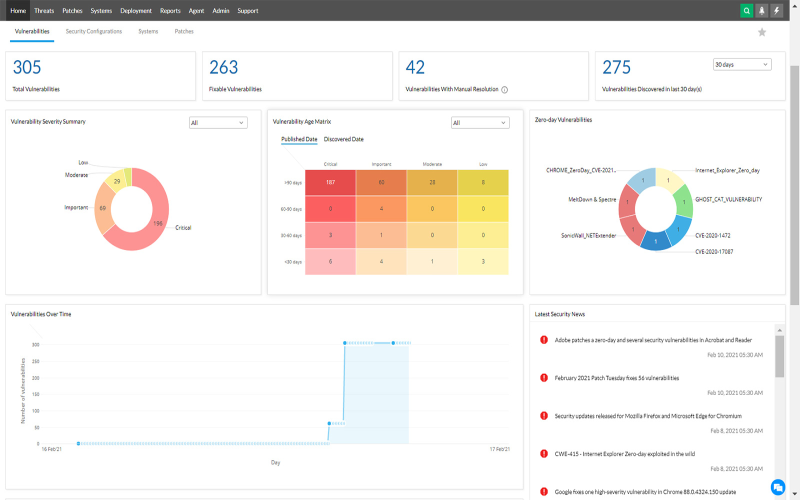
3. ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus helps you secure your devices by looking for security flaws. This software is brilliant and compatible with Windows Server. It’s similar to always having a personal security advisor on hand. It identifies potentially hazardous weak points and gives you advice on how to address them. Everything is in one location, making it simple to use. They also provide a free 30-day trial so you can test out the features.
4. ManageEngine Log360
ManageEngine Log360 is a computer assistant that monitors and protects your logs. This software is from the same company as Vulnerability Manager Plus and is available for testing for free. This tool collects logs (records) from various sources, such as computers, servers, and even security systems. This information is presented with graphs and reports. It detects and notifies you of significant changes in real time. It can even react quickly to any suspicious activity. It also keeps an eye on your cloud storage to ensure that everything is secure.
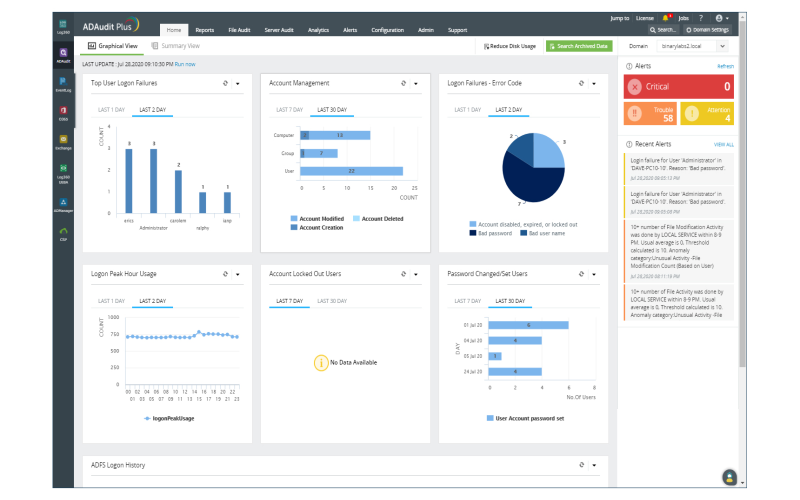
5. VMWare Carbon Black Endpoint
VMWare Carbon Black Endpoint is a powerful NGAV (next-generation antivirus) and EDR (endpoint detection and response) solution for enterprise and regular customers that protects against cyber-attacks. VMWare carbon black endpoint has several features such as protection of organization and customers data from malware infections, a platform to remotely monitor and respond to minimize system downtime, monitoring events related to ransomware outbreaks, a centralized console that gives alerts and information on endpoints and containers, creating policies for endpoint protection, and more. It’s a one-stop solution for organizations that they can combine with other tools for even better protection.
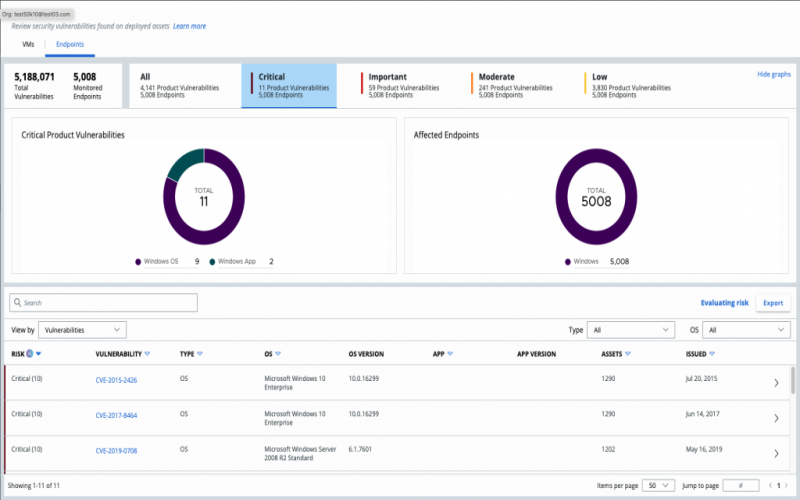
6. CrowdStrike Falcon
CrowdStrike Falcon is an all-in-one security operation center that includes a SaaS EDR system (endpoint detection and response) called Falcon Insight, technicians to run the software, and security analysis for manual threat hunting. It provides features such as using artificial intelligence to analyze endpoints, stopping attacks that target software, scalable cloud-native platform, easy to deploy and manage, and uses power native automation and generative AI workflows. The company uses artificial intelligence and manual experts to hunt the threats and attacks.
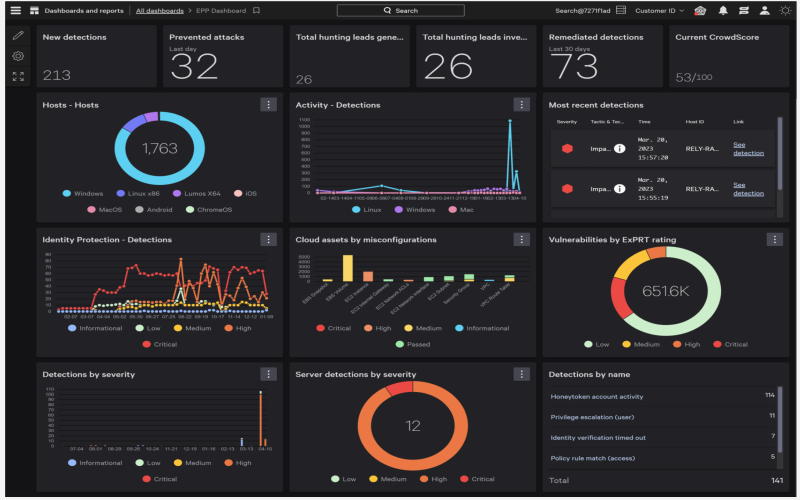
7. Trend Micro Managed XDR
Trend micro-managed XDR is an excellent threat analysis and monitoring tool that operates 24/7. It uses network, email, server, cloud, workload, and endpoint sources to correlate for more robust detection and spread of targeted attacks. It comes with features such as email, endpoint, cloud workload, and network sweeping for threats and offers tools for investigating anomalous behavior in systems.
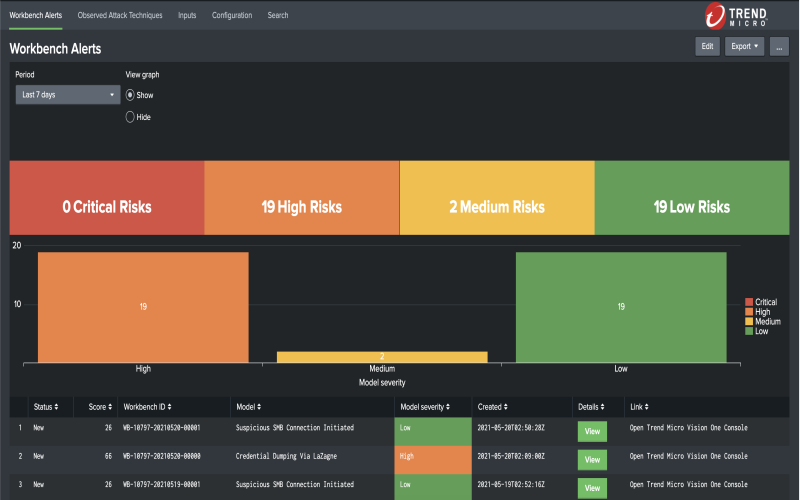
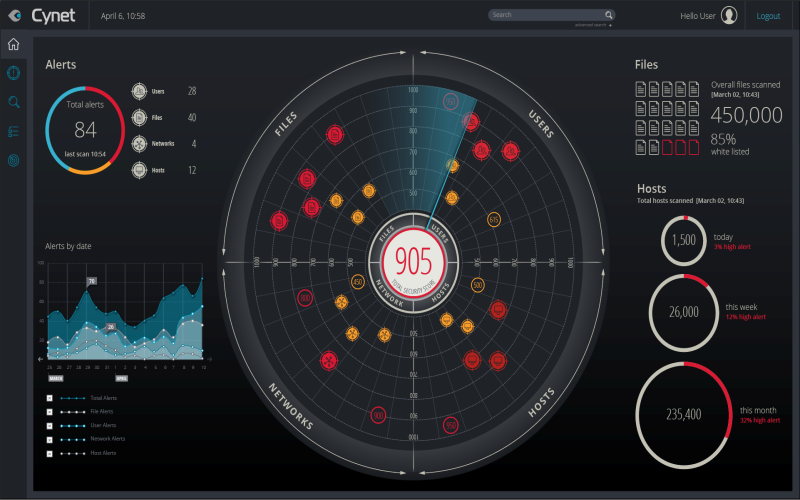
8. Cynet 360
Cynet 360 uses intelligent machines and robots to look for threats and attacks. It can work on different types of computers like cloud and regular homes. It has several features such as finding computer bugs (malware), detecting when someone tries to break in (exploits), it watches over your computer endpoint, it can allowlisting & blocklisting computer programs, it gives you tools to monitor threats and making reports it can learn on new threats outbreaks to keep you safe and send you threat alerts.
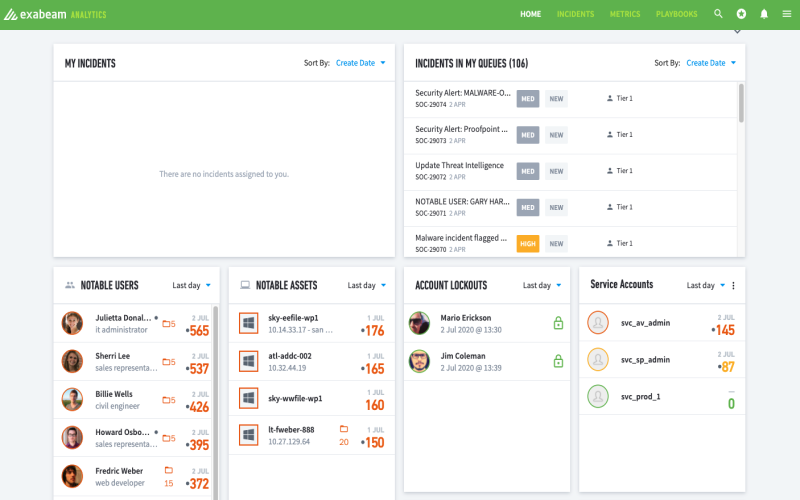
9. Exabeam Fusion
Exabeam Fusion is a cloud security system. It brings together all the best things from the Exabeam toolbox. It’s great at storing data, understanding information, and quickly spot trouble. It’s also brilliant. It knows how people and devices usually behave. If something starts acting weird, Exabeam Fusion notices and takes action. It uses over 1800 rules and 750 models to find even the most minor threats that other tools might miss. But that’s not all it automates the detecting, checking out, and solving problems. So your security team can focus on what’s important. Exabeam Fusion is a powerful and valuable tool for safeguarding sensitive information and data.
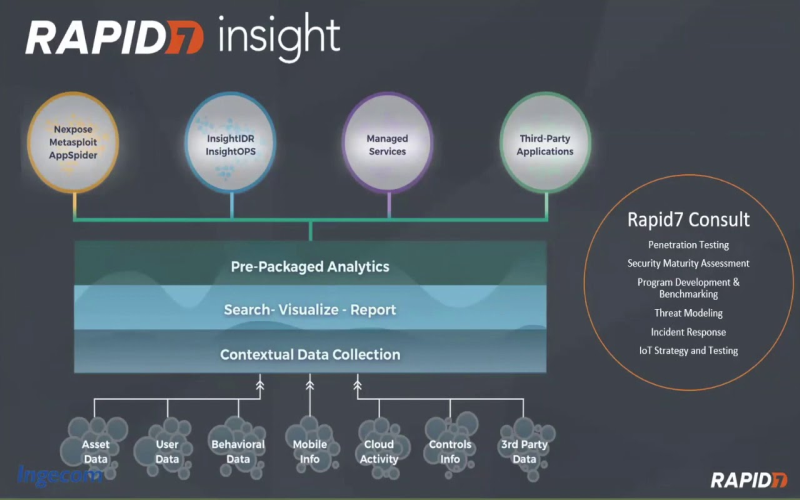
10. Rapid7 InsightIDR
Rapid7’s InsightIDR is all about finding and dealing with problems, keeping an eye on who’s coming and going, and checking what’s happening with your devices. You don’t need to monitor and understand large amounts of data because it spots strange data and relations. This tool combines different type of unstructured data, like logs, files, and network traffic, and provide structured data in graphs and easy-to-read reports. If something doesn’t look right, InsightIDR notify the user and offers insights and measures for protection. In conclusion, it’s your trustful software for protecting organizations and general users.