Cyber threats mean the chance of a successful cyber-attack that aims to damage the system, steal data, gain unauthorized access to your computer, or gain any other sensitive and valuable information. As increases in internet connectivity, cybercrimes also have increased. To protect our data from cyber criminals, we need to know about cyber security and the threats we face in cyber security. A hostile nation and terrorist groups perform cyber threats, hacker groups, or individual hackers. Things about Cyber threats that you need to know about it. Let’s see 10 cyber security threats.

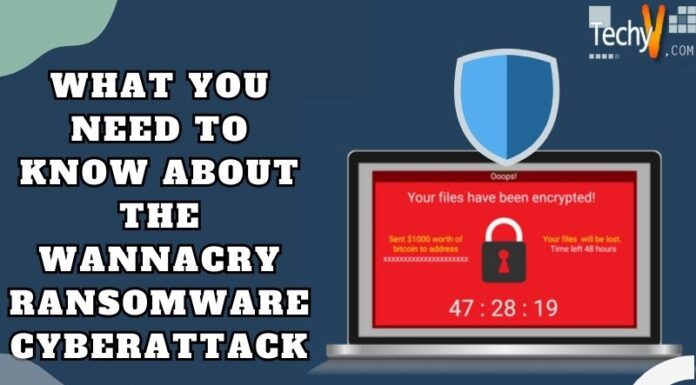
1. Ransomware
The ransomware attack is a prevalent and significant cyber threat. In a ransomware attack, a hacker locks the user’s computer and encrypts valuable data so the user cannot access them. Then hackers demand money or ransom in exchange for decrypting or unlocking data. Ransomware attacks are made by clinking on the unknown link on a third-party website or phishing email. Ransomware is harmful due to the difficulty in recovering the affected data. It is used to target small businesses due to weaker cyber security measures.

2. Phishing attack
The phishing attack is one of the common attacks made by hackers. The hacker or attacker sends emails or messages that look like they are from a trusted website or company. The email is mainly fraudulent and contains a link that takes the user to a third-party website that takes the user’s personal information, such as bank account and credit card information.

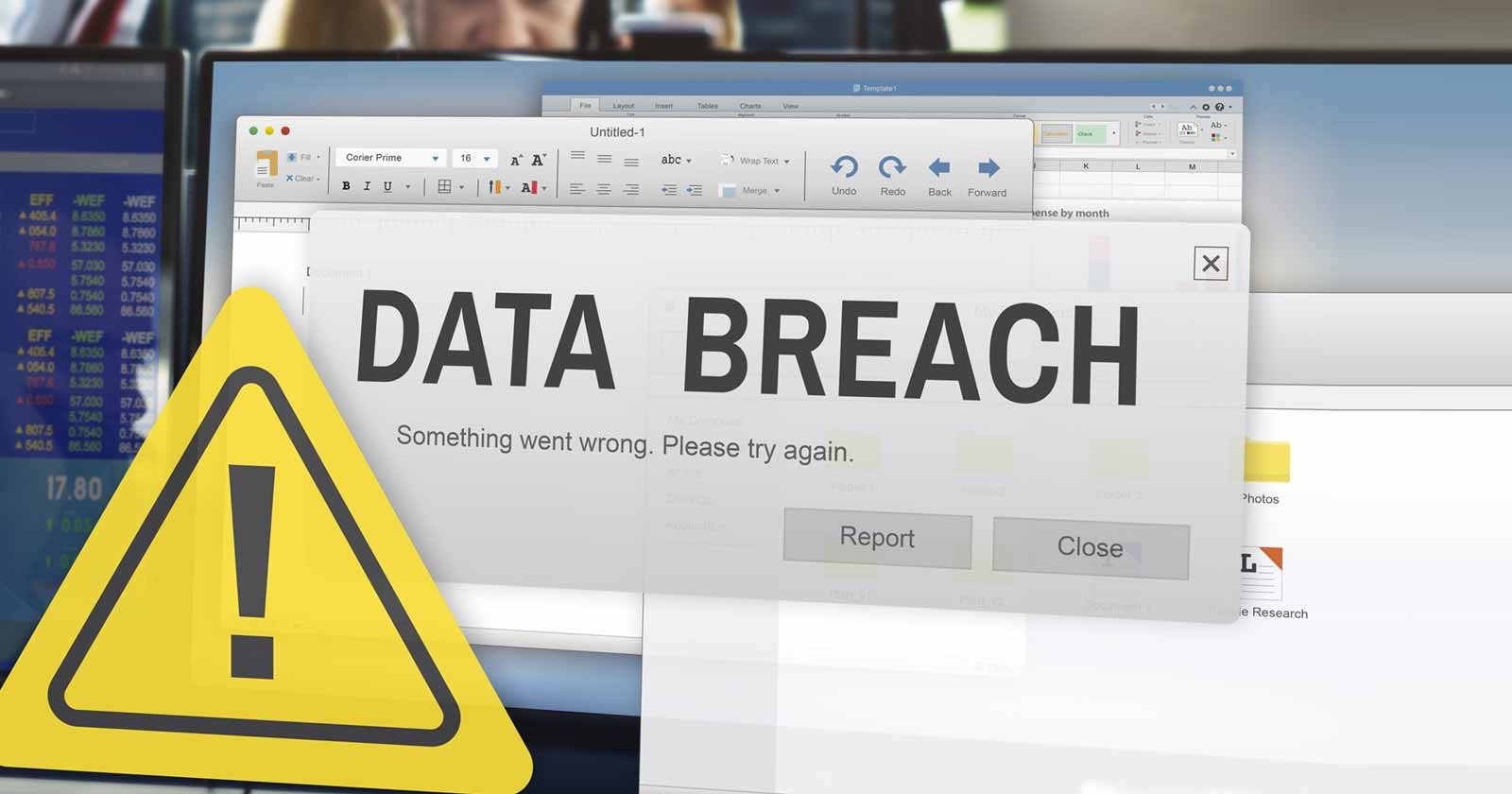
3. Data breach
A data breach is a cyber-attack during which sensitive data is stolen from a system without the knowledge or authorization of the system owner. Data breaches are commonly seen in any size organization. Data breaches are done by an accidental insider, a malicious insider, or a malicious outsider. Due to data breaches, the company faces heavy losses in both reputational and financial.
4. Spyware
Spyware is malware software installed on a computer without user knowledge. It is the most common threat to internet users. When installed in a system, it tracks login and internet activity and spies on sensitive data. Spyware is also used for monitoring the location, web browsing history, and passwords. One of the latest Spyware is Pegasus. Spyware is difficult to detect in the system.

5. Social-Engineering
Social engineering attacks depend most on human interaction to gain the user’s valuable data. Cybercriminals interact with users and manipulate or trick them into accessing sensitive information. Cyber security can’t stop social engineering that why it is one of the top threats in the cyber world. Social engineering is dangerous because it depends on human error rather than software mistakes.

6. Internet of things (IoT) attack
The IoT device is connective all over the internet, allowing a network of devices to store, receive and send data. Hackers can exploit internet connectivity and steal data. The IoT attack is becoming a big concern in the upcoming year because of the increase in technology and connectivity. Everyone is using an IoT device. Many companies are increasingly dependent on IoT devices.

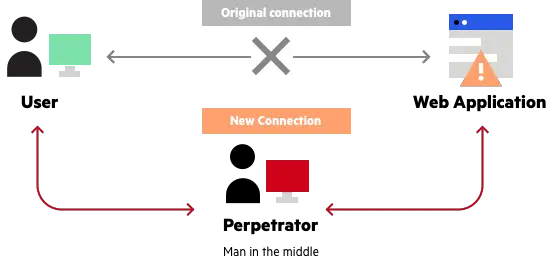
7. Man in the middle
Man in the middle is a cyber attack in which the attacker secretly accesses the information between two parties, and the parties think they communicate directly. Hackers can use data captured during an attack for various purposes, including identity theft, fraudulent money transfers, and fraudulent password changes. The Man in the middle attack focuses on gaining personal information such as login ID and bank details. Examples of MITM are eavesdropping, DNS spoofing, Email hijacking, etc.
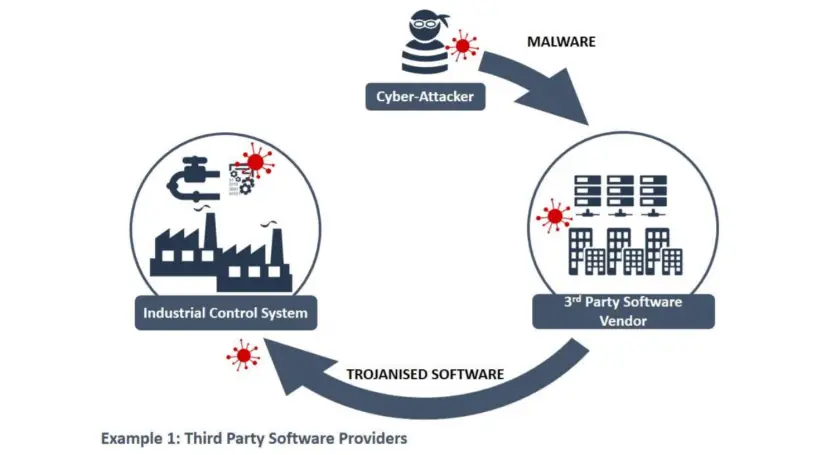
8. Third-Party Exposures
The third-party threat is the top concern for all businesses. As cybercrime becomes more sophisticated and cybersecurity threats continue to increase, organizations are becoming more aware of potential dangers by third parties. Third-party attacks can steal the valuable data of a company’s employees and customers. Hackers quickly exploit poor hygiene and loophole.
9. Cloud vulnerabilities
Cloud computing is now increasing rapidly. Most companies are shifting their data to the cloud. Cloud hosting is used for storage and computing. This increase the risk of attacks on cloud services. Attackers can steal the data which are uploaded on cloud services. Hackers can also enter the cloud environment to mine cryptocurrencies. Vulnerabilities like cloud misconfigured, Data breaches, malicious injection, ensure APIs, etc.

10. Insider Threat
Insider Threat is the threat where the attacker is the organization’s insider. Human mistakes are one of the primary reasons for data breaches. The insider will use the authorized access intentionally or without intent to harm the organization’s mission, data, or personal information of organization, network, or system. It’s tough to stop insider threats to cyber security because it’s based on human errors.