Data breaches from human error and cyber attacks have unfortunately become commonplace, with serious consequences for companies in terms of financial penalties, loss of customer trust, and impacts on overall business operations. Implementing solutions to protect sensitive data through proper classification, monitoring, and encryption is no longer optional in the digital age – it is imperative for risk management. I outline the top 10 data classification offerings to consider as part of a comprehensive data loss prevention strategy. Balancing automation, usability, flexible policies, and robust engines warrants evaluation across solutions. Standardization on one enterprise-level platform proves challenging with varied legacy infrastructure, budgets, regulations, and use cases. As such companies often leverage a multi-pronged approach to cover critical systems while still allowing for specialized point products where they excel. Across test cycles and real-world applications, most organizations will want to deploy at least one broad enterprise solution along with more tailored options for unstructured data repositories.
1. Microsoft Information Protection (MIP) Capabilities
Microsoft offers native data classification and protection capabilities, particularly appealing for users running Windows and Office software to quickly implement data classifications. Pre-configured labels through Azure Information Protection integrate with Microsoft 365 for wide coverage across organizations. The Microsoft Compliance Center offers a starting point for companies already invested in Microsoft products.
2. Titus Illuminate Data Classification Suite
The Titus Illuminate data classification suite provides automation, auditing, user-directed handling, and integration with encryption to address common regulatory mandates. Policy-based scans analyze file shares and databases while allowing customizable actions by content and context. Titus focuses specifically on persistent protection controls when traveling with documents.

3. Boldon James Classifier Outlook Plugin
Part of Boldon James data classification and secure messaging suite, Classifier operates as an Outlook plugin to infer sensitivity. Users can visually tag emails and attachments while pop-up notifications recommend classifications. The Exchange module extends capabilities to mail flow transport rules for automated policy applications. Boldon James integrates classifier metadata with data loss prevention tools.
4. Symantec Data Loss Prevention
Symantec Data Loss Prevention covers a wide range of data discovery, classification, monitoring, and protection capabilities through one offering. Integrations enable enforcing configured controls for things like restricting access and movement of sensitive data or applying rights management protections. The machine learning algorithm improves over time while accounting for localized data types and privacy regulations, reducing reliance on complex configurations. One unique capability automatically redacts sensitive data from files when users attempt to share or distribute information inconsistent with policies. This helps reduce unintended data leaks from employee accidents or negligence.

5. Digital Guardian
Digital Guardian takes a data-centric approach that classifies and controls sensitive information directly instead of just regulating access to systems or files. The platform connects both on-premises and cloud data sources, providing a unified view and consistent policy application. Machine learning models incorporate data science and behavioral analysis to account for zero-day and evolving threats when labeling and protecting information. The solution provides advanced data tracing, and tracking file lineage across copies, extracts, and derivatives to maintain links between classified data and child files. This helps organizations maintain control even as sensitive information changes hands or gets transformed.

6. Informatica Data Privacy Management
As a dedicated data privacy platform, Informatica Data Privacy Management enables organizations to discover, classify, and govern personally identifiable information scattered across business systems. The intelligent discovery engine leverages machine learning and reference data on common data types falling under privacy regulations. Configurable dashboards deliver visibility while notifications alert to potential non-compliance risks. Informatica connects with downstream security controls to apply encryption, tokenization, or masking based on sensitivity classification. Organizations can automatically redact sensitive elements from files accessed inconsistently with policies.

7. Varonis Data Classification Engine
The Varonis Data Classification Engine scans local file systems, collaboration platforms, and object stores to categorize sensitive information using customizable classification criteria and machine learning models. Once categorized, administrators can apply an array of controls encompassing access restrictions, encryption requirements, retention rules, and activity monitoring alerts based on sensitivity levels. Varonis provides transparency through detailed classification analysis reports for both technical teams and business leaders. The dashboards deliver actionable intelligence to continuously tune classification schemas and policies towards improved protection. Integrations auto-apply visual labels helping to guide end users when accessing files in Windows or SharePoint.
8. Netwrix Auditor
Netwrix Auditor enables discovering, classifying, and governing sensitive and regulated data distributed across on-premises or cloud infrastructure regardless of where it resides. The platform audits user behavior, data access, permission changes, administrator actions, and threat patterns—all used to inform data classification. Machine learning improves detection and policy efficacy over time while accounting for localized privacy legislation in global deployments. The solution’s visibility and control capabilities help organizations simplify compliance with regulations like GDPR and CCPA. Automated remediation workflows mitigate risk by revoking access or quarantining sensitive data following suspicious access attempts, inadvertent exposure, or policy violations. The customizable dashboards and unified reporting streamline audit preparation and evidence gathering, saving organizations substantial overhead. For infrastructure spanning multiple platforms, Netwrix deserves evaluation.

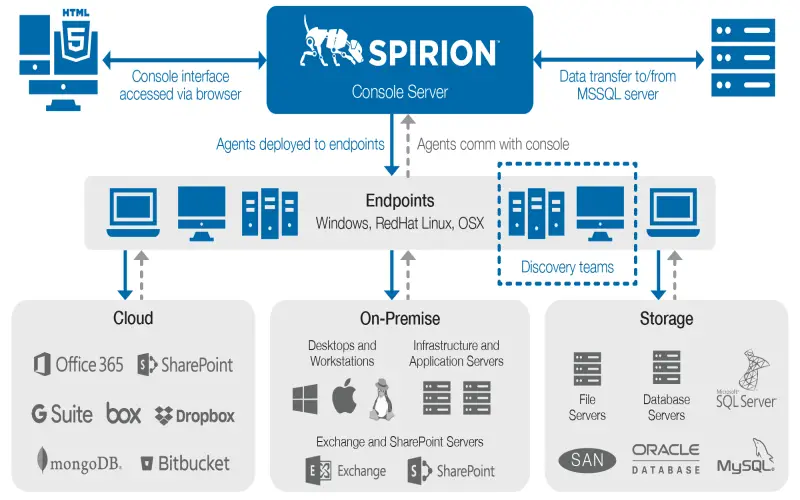
9. Spirion Data Platform
The Spirion data discovery, classification, and protection technologies operate through a single platform without needing agents. The solution connects over 240 different data stores, including leading cloud apps, databases, messaging platforms, and collaboration tools. Using optical character recognition and natural language processing, Spirion builds context-aware metadata to group related information into concepts during classification. After categorization, Spirion applies configured encryption, access restrictions, activity monitoring, and other data-centric protections based on sensitivity. The platform incorporates user behavior analytics to detect risky patterns involving classified data sets. Advanced classification analysis provides visibility enabling continuous optimization of policies and controls. For those prioritizing streamlined administration through a unified offering, Spirion warrants consideration.
10. PKWARE Data Classification
PKWARE takes a business-centric approach to data discovery, classification, and security tailored to ease compliance burdens. The platform leverages machine learning to catalog sensitive information across business systems while tailoring classification to align with organizational taxonomy. Dashboards give data owners transparency into what data resides where—enabling targeted remediation of improperly secured sensitive information. The solution can directly mask or tokenize classified information to reduce compliance scope. PKWARE also applies automated redaction of sensitive data from files when users share information improperly. Secure collaboration capabilities facilitate cross-organization data sharing without relinquishing control over sensitive data.