Encryption protects sensitive data like financial transactions, healthcare records, and proprietary communications by scrambling plain text into indecipherable cipher text. It provides fundamental data security controls across industries dealing with critical information assets and privacy regulations. As cyber threats grow exponentially more advanced and persistent, organizations must implement robust encryption both at rest and in transit to safeguard systems. However, with countless algorithms available, discerning the most secure ciphers suited for different data types and use cases challenges even seasoned security professionals. I outline the top 10 encryption algorithms cybersecurity teams should familiarize themselves with based on widespread adoption, sophisticated security protections, speed, flexibility, and interoperability. While no single solution proves unbreakable forever as computing power advances, combining multi-layered algorithms with protocols like SSL/TLS thwarts most attacks allowing teams to transmit, analyze, and store data securely.
1. AES (Advanced Encryption Standard)
AES constitutes the encryption standard used ubiquitously by governments, banks, and enterprises to protect classified information. It ciphers and deciphers data in block sizes of 128, 192, or 256-bit keys at blistering speeds through substitution, transformation, and permutation methods. AES encryption proves complex enough to render brute force attacks infeasible versus vulnerable algorithms like DES and 3DES which higher computing now cracks. It ships natively on hardware from Intel, AMD, and ARM alongside operating systems like Windows, Linux, and macOS. This ubiquity and speed accelerates widespread AES adoption specifically the AES-256 variant for optimal security against threats like quantum-powered decryption emerging in the future.

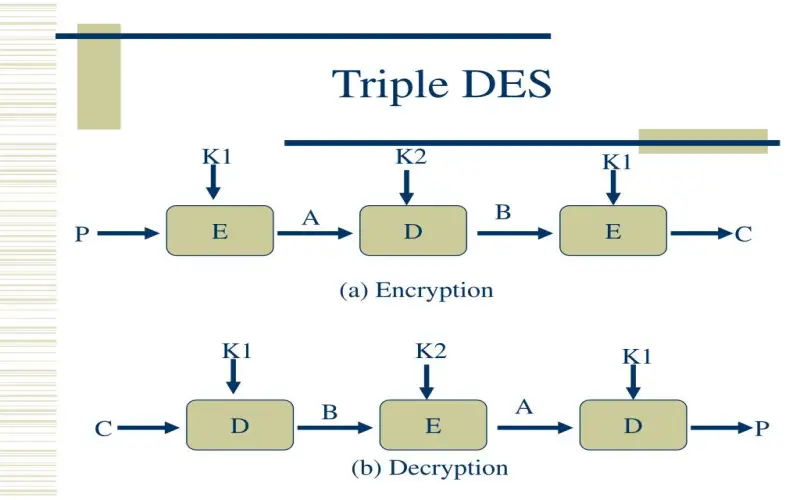
2. Triple DES (3DES)
3DES constitutes the legacy encryption predecessor to AES that processes plaintext blocks through three keys along a pipeline. It ciphers first in one direction then back across two more 56-bit keys totaling 168 bits for heightened protection versus DES with one 56-bit key now considered cryptographically broken. The downside remains decreased performance, and most recommendations point to migration to AES. Still, 3DES support persists across legacy systems and backup protocols giving teams continued access when transitioning proves difficult. Just remember it leaves data lightly exposed to brute force risks long-term as threats evolve.
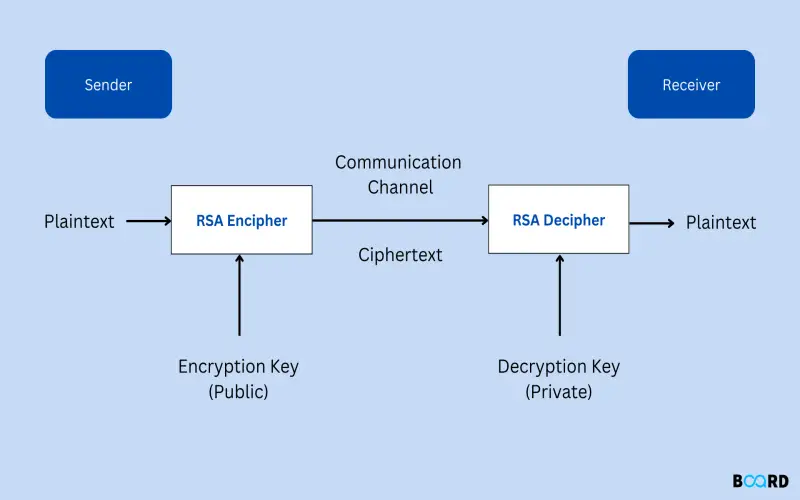
3. RSA
As the dominant encryption algorithm for secure key exchanges, RSA enables public key infrastructure by having key pairs wherein the public key encrypts data such that only the private key holder deciphers. Its mathematically complex asymmetric process lets parties transmit securely without pre-exchanging secret keys beforehand. RSA undergirds the initial secret handshakes enabling SSL/TLS web encryption. However, given slower speeds than symmetric key algorithms like AES, its role focuses on allowing session secrets that subsequently symmetrically encrypt communications. Key lengths of 2048 & 3072 bits provide short-term safety but warrant upgrades to guard against future quantum attacks.
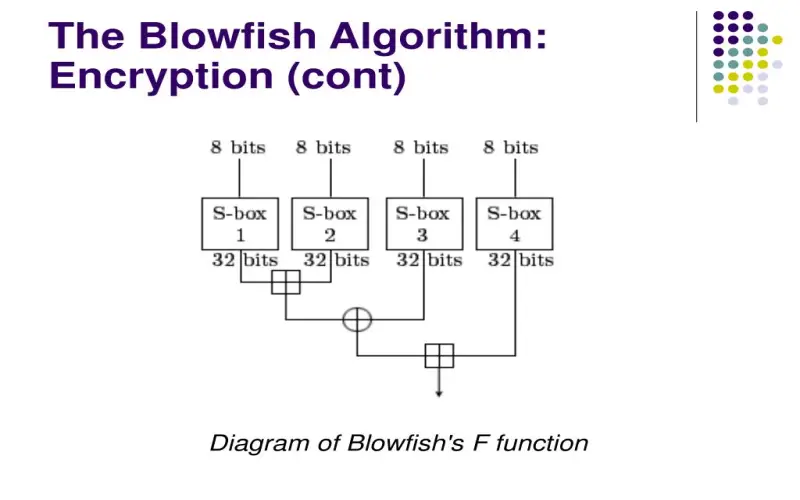
4. Blowfish
Accessible free license-free across all platforms, Blowfish provides speedy, license-free symmetric key encryption. It executes faster than 3DES yet slower than AES. Blowfish usage spans VPN tunnels, and data stores like SQLite and Linux kernel encryption. Some disadvantages include: 64-bit blocksize risks versus AES’s 128 which increases collisions, slow adoption elsewhere diminishing analysis, and weakened protection against complex attacks like differential cryptanalysis compared to AES according to scholastics. Still, Blowfish’s speed and flexibility accommodate environments handling sensitive data without complex requirements.
5. Twofish
As a symmetric key encryption contender to replace DES submitted alongside AES and other proposals, Twofish failed to gain similar ubiquity despite expert commentary ranking its security on par with AES. The related-key attack risks first outlined in AES remain its main disadvantage. However, Twofish executes faster than AES and supports flexibility across key sizes and platforms. Smartcard vendor Cyberflex utilizes Twofish in banking cards given the cryptography agreement on its safety. Conservative adopters dealing with only modern threats may lean towards Twofish for improved throughput over AES initially. However, AES provides better long-run quantum-proofing as risks emerge.

6. IDEA (International Data Encryption Algorithm)
Initially standardized across Europe and utilized in early versions of PGP encryption, IDEA constitutes a symmetric key algorithm similar to DES and AES but based on mixing operations across subkeys. Governments approved IDEA for protecting classified information, and its security once compared closely with AES. However, with patents expiring allowing deeper analysis, researchers demonstrated vulnerabilities allowing efficient cryptanalysis attacks. Thus IDEA warrants avoidance in modern software. Some legacy systems still rely on IDEA protection but require transition off given long-term risks.
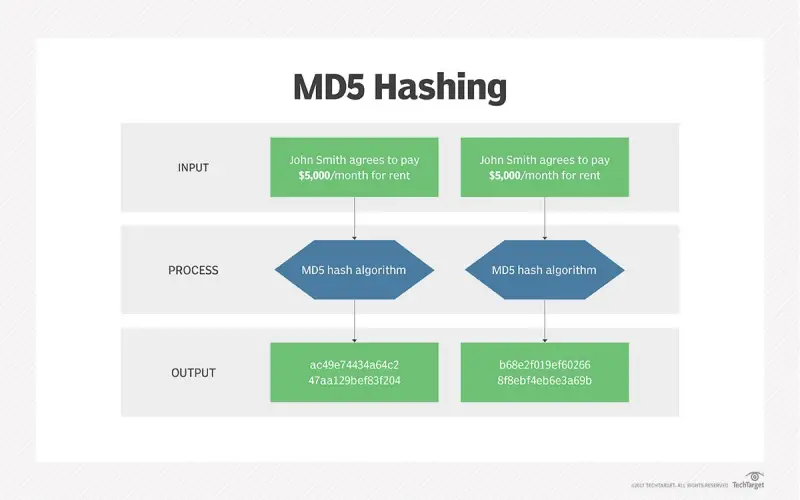
7. MD5 (Message Digest Algorithm 5)
As a widely supported one-way hashing encryption algorithm, MD5 creates fixed-length 128-bit digests irreversibly from plaintext. Hashing proves essential to integrity checks by detecting changes across data. However, given MD5 cracks easily now through hash collisions that spoof integrity, usage requires replacement by SHA-2 algorithms like SHA-256 despite persisting commonality. Hashing differs from ciphers like AES or RSA by lacking secret keys that allow decryption. So while still safely verifying file contents against tampering lacking encryption, MD5’s role now focuses only on checksums not actual data protection—thus failing to cut a secure cipher.
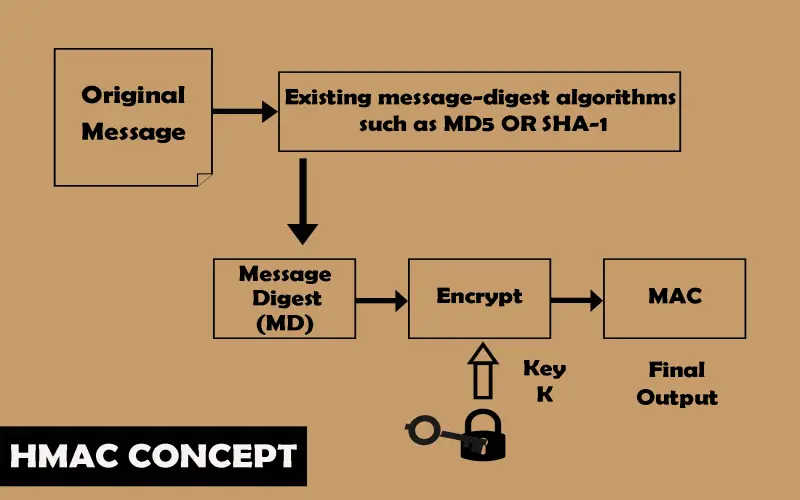
8. HMAC (Hash-Based Message Authentication Code)
Unlike basic hash functions like MD5 and SHA-1, HMACs allow hash-based message authentication using secret keys across hashing algorithms by combining both cryptographic hashing and MAC authenticators. The combinatorial processing heightens security protections for integrity checks and tamper detection above straight hashes vulnerable to spoofing. Software developers leverage HMACs across authentication tokens, message integrity checks, and protecting API communications at speed. Recommendations center on SHA-2/SHA-3 algorithms as the hashing foundation paired with strong encryption keys.
9. RC6
As a symmetric key block cipher submitter unsuccessful alongside AES for the Advanced Encryption Standard designation, RC6 provides speedy encryption across 32-bit to 256-bit keys. It constitutes an enhancement of RC5 correcting certain decryption weaknesses. RC6 proves software friendly leveraging serial word-based rotations, mixing, and modular addition executed through fast logical operations.
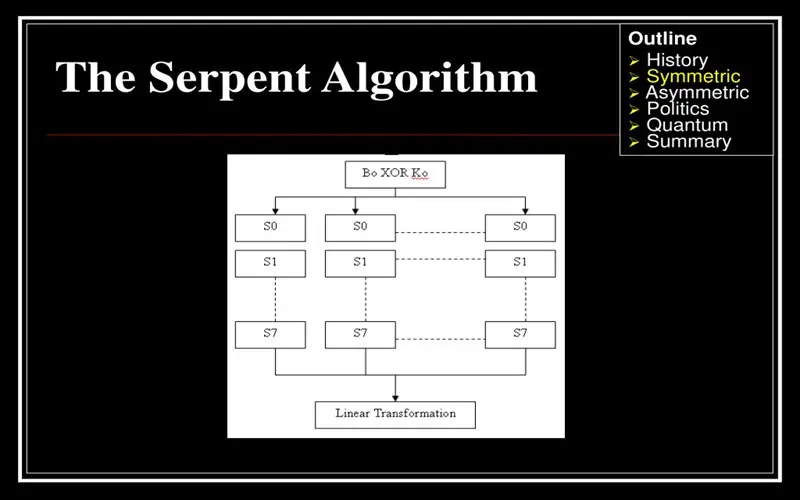
10. Serpent
Complimenting AES finalist Twofish, Serpent competed as part of the same AES evaluation, also losing to Rijndael, the successful AES candidate. Software efficient using a 128-bit block size, Serpent utilizes variable-length keys (128, 192, or 256-bit) and remains resistant to differential and linear cryptanalysis, attack vectors threatening inferior algorithms. Today the extensibility and conservative design of Serpent position the symmetric cipher as a secure, general-purpose solution for commercial cryptography needs across desktop, hardware, and embedded systems.